Search Results for "rail fence cipher in network security"
Find videos related to your search query. Browse through our collection of videos matching "rail fence cipher in network security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "rail fence cipher in network security"
52 results found

3:57
Security Mechanisms | Network Security | Cryptography and Network Security
Bikki Mahato
184 views

6:06
Need for Security | Network Security | Cryptography and Network Security
Bikki Mahato
405 views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

0:59
Cipher’s Greek References EXPLAINED | Honkai: Star Rail #honkaistarrail #hsr #amphoreus #cipher
JorJor EXP
157.6K views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

40:38
Cryptography in network (Network security basics) |Lecture 25| Data Communication & Computer Network
Mateen Yaqoob
58 views

10:20
Block Cipher and Stream Cipher | Explain with animation | Block cipher vs Stream cipher
Chirag Bhalodia
38.3K views

6:31
Shift Cipher/Caesar Cipher | Monoalphabetic Cipher | Substitution Cipher
Study Table
10.6K views

7:12
An Indecipherable Cipher | Vigenère cipher | Vigenere Cipher | Polyalphabetic Cipher | Cryptography
Muhammed Mustaqim
144 views

10:35
Hill cipher|Hill cipher encryption and decryption|Hill cipher example|Hill cipher in cryptography
Last Night Study
39.7K views

13:51
Affine cipher|Affine cipher encryption and decryption|Affine cipher example|Affine cipher decryption
Last Night Study
113.1K views

6:37
caesar cipher | atbash cipher | keyword cipher| pigpen cipher|cryptography types and applications
Sir Huzaifa Sabir
46 views

6:13
Imran Khan Pr Ciphar Case Batna Hi Nahi | The cipher case of Imran Khan is not being made.. The cipher case is being dragged unnecessarily... The day the cipher was waved?... The cipher case is not a crime... This crime has been added. ... Aitzaz Ahsan
Update Pakistan News
6 views

5:34
Substitution Cipher vs Transposition Cipher|Substitution Cipher and Transposition Cipher|E Commerce
Last Night Study
3.5K views

11:42
Feistel cipher|Feistel block cipher|Feistel cipher structure|Feistel cipher example|cryptography
Last Night Study
18.2K views

2:41
Difference between Block cipher and stream cipher / Block cipher vs stream cipher
ms coder
5.3K views

1:05
Vernam cipher || Cipher || Will cipher || Verum rex || bill cipher || airbnb
CryptobyQB
21 views

4:47
8.2 (part-3) - Monoalphabetic cipher and Polyalphabetic cipher of Security | Computer Network Bangla
Engineering Bangla
831 views

7:11
Cryptography & Network Security: #17 Polyalphabetic Cipher and its type Autokey Cipher
Shreya's E-Learning
637 views

6:39
Poly alphabetic Cipher || Vigenere Cipher in cryptography and Network Security
Lab Mug
15.4K views

5:48
symmetric cipher || urdu hindi | symmetric cipher model in cryptography and network security }part13
IT Expert Rai Jazib
458 views

25:07
Substitution Techniques: Caesar Cipher &Monoalphabetic Cipher-Cryptography & Network Security#21is71
VTU padhai
3.7K views
![Caesar cipher (first cipher technique) Cryptography and Network security in HINDI [ हिंदी ].](/image/i.ytimg.com/vi/efEXsGIALuE/hqdefault.jpg)
9:23
Caesar cipher (first cipher technique) Cryptography and Network security in HINDI [ हिंदी ].
Helping Tutorials
6.4K views
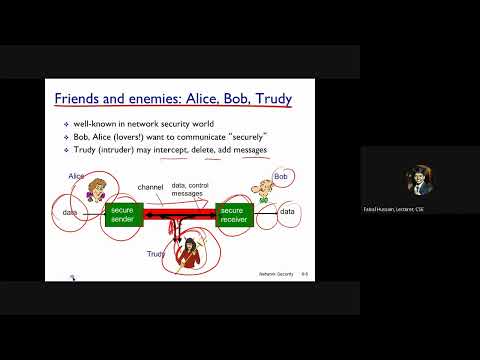
32:30
Lecture 36 Network Security, Caesar Cipher, Mono-alphabetic Cipher
Qubits 45
108 views

5:20
ROT13 cipher text || urdu hindi | rot13 cipher text lecture in network security | ROT13 | part 14
IT Expert Rai Jazib
599 views

32:30
L.1.6.66: Network Security, Caesar Cipher, Mono Alphabetic Cipher || Computer Networks
Study With Janin A Apurba
13 views
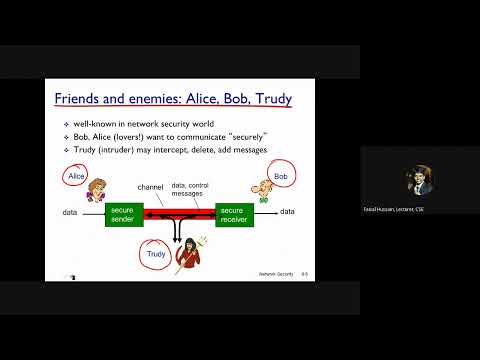
36:59
Lec 36 Network Security, Caesar Cipher, Mono alphabetic Cipher
Chris P Bacon
4 views

30:19
05-Substitution Techniques in Network Security 🔐 | Caesar Cipher & Playfair Cipher Explained
Sundeep Saradhi Kanthety
216.7K views

9:41
monoalphabetic cipher | Cryptography and Network Security | Substitution Cipher Babita Verma
ITCS classes
8.6K views

5:37
What is Cryptography? Network Security| Block Cipher |Stream Cipher | Symmetric Key | Asymmetric Key
IT Academy
123 views

21:07
L-11 | Stream Cipher vs Block Cipher |Algorithm Type in Network Security & Cryptography|By Chealsha
Simply Studies With Chealsha
21 views

10:41
Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplilearn
Simplilearn
59.8K views

4:27
Block Cipher Mode of Operations | Mode of Opreations in Block Cipher | Network security..
DK Technical Point 2.0
187 views

14:20
Caesar Cipher (part-1) in Cryptography and network security in bangla | Math of caesar cipher bangla
content on demand
4.2K views

12:58
Cryptography and Network Security - Monoalphabetic Substitution Cipher, Playfair Cipher
Dr. Bhuvaneswari Amma N.G.
38 views

19:43
Cryptography | Transposition Cipher | Caesar Cipher | Network Security | One Day One Topic Series
Unify Study
3.5K views

3:03
Monoalphabetic cipher and Polyalphabetic cipher in Hindi Urdu - Network security 9.0
RaxsCorp
1.6K views

3:02
Difference between Substitution Cipher and Transposition Cipher | Network Security Explain..
DK Technical Point 2.0
1.0K views

10:11
What is Stream Cipher |Stream Cipher Introduction and working |Network security hindi
DK Technical Point 2.0
314 views

7:56
Difference between Block cipher and Stream cipher /CS 409 Cryptography and Network Security -Part 8
Renisha's CS Eduworld
1.1K views

32:08
SM4 (SMS4) Block Cipher Algorithm | ShangMi Block Cipher | Cryptography and network security
H Logix & Solutions
584 views

10:12
Hybrid cipher|Hybrid Transportation Cipher|Transposition techniques in cryptography|Network Security
Last Night Study
1.2K views

38:05
Network Security Tutorial | Introduction to Network Security
CRAW SECURITY
1.1K views

42:46
RSA Algorithm in Cryptography and Network Security - UGC NET PYQs | NETWORK SECURITY - RSA ALGORITHM
Unify Study
4.6K views

6:53
Network security attacks in Hindi | Active attacks and Passive attacks in Network security in Hindi
QuickCS
1.2K views

13:06
Steganography | network Security in tamil,#sscomputerstudies,#steganography,#network,#security
SS Computer Studies
1.5K views

11:33
Module 2: Network security and definitions | Communications and Network Security | Cybersecurity
Flipped Classrooms
2 views

10:09
Cryptography and Network Security Course | Cryptography and Network Security Playlist | Cryptography
Abhishek Sharma
397 views

13:31
LEC01|Cryptography & Network Security | Intd.. to Cryptography&Network Security by Ms. M . Saranya
MLID - MLR Institute of Technology
185 views

4:11
Cryptography and Network Security BCS072 Syllabus Introduction | AKTU Cryptography Network Security
EduShine Classes - Arman Ali
470 views

1:53
Drones, fences and roadblocks: How The Hague ramped up security for NATO summit
euronews (in English)
1.1K views

2:20
Pro-Palestinian activists protest outside DNC in Chicago
DW (English)
920 views