Search Results for "non-standard methods"
Find videos related to your search query. Browse through our collection of videos matching "non-standard methods". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "non-standard methods"
50 results found

17:50
Non Stop Party Songs Mashup 2022 _ Dj Party Mix _ Non Stop Remix Mashup _ Bollywood Party Songs
Movie trailers
147 views

28:17
Non Drop 4k Hours Watch Time Trick 2023 | Watchtime kaise pura kare | Non drop Watchtime Method 2023
Sub Koch Methods Only
440 views

0:46
Adobe Photoshop 2024 v25.2 Beta + Neural Filters | Photo editing programme This file is for trial, educational, and non-commercial use only. Using non-genuine software may cause various problems To use this software without any problems Please purchas
IIIIIIRuS_Q
287 views
![AdobeAdobe Photoshop 2024 v25.1.0.120 [Pre-Activated] is for trial/educational and non-commercial use only. Using non-genuine software may cause various problems To use this software without any problems Please purchase a genuine license from the offi](/image/s2.dmcdn.net/v/VMZBQ1eoTSnCiWZzK/xx720.pagespeed.ic.fHZu5RdCkw.jpg)
0:51
AdobeAdobe Photoshop 2024 v25.1.0.120 [Pre-Activated] is for trial/educational and non-commercial use only. Using non-genuine software may cause various problems To use this software without any problems Please purchase a genuine license from the offi
IIIIIIRuS_Q
225 views

24:38
Non Stop Love Mashup Love Songs Non stop mashup#lovemashup#love
Entertainment33
11.5K views

1:04
Mais non ! NON !
Real Boy Jimmy
2.7K views

3:16
HIMRA - BÂTON NON NON (Clip Officiel)
Infanta Sofia
2.2K views

3:33
What Is Non-Ionizing Radiation (Radiation Meters) What Is Non-Ionizing Radiation
Jennifer Smith
1 views

1:05
ELLY LA MELONI LA MANDEREMO A CASA NON NON CE BISOGNO CHE Si dimetta 😂😂😂😂😂
PATRIOTA ITALIANO 🇮🇹
4.9K views
![VTU COMPUTER NETWORKS AND SECURITY (18CS52) [Security Methods, Cryptography] (M4 L2)](/image/i.ytimg.com/vi/-TKiDUSDoqk/xhqdefault.jpg.pagespeed.ic.4MvFQi-c68.jpg)
28:04
VTU COMPUTER NETWORKS AND SECURITY (18CS52) [Security Methods, Cryptography] (M4 L2)
Canara Engineering College Mangalore
7.0K views

1:00:27
Tools and Methods Used in Cybercrime Part 4 | Dr. Reshma Kadam
Reshma Patil
309 views

10:45
3 Ways to Make Money with GPT-5 (Beginner Methods)
Liam Ottley
222.9K views

11:08
Tanner Chidester Review (Elite CEO) - Can his methods scale online coaching biz?
Hunter Martin
174 views

8:19
System of Equations: Solve by Graphing and Substitution Methods
Kwakulus
312 views
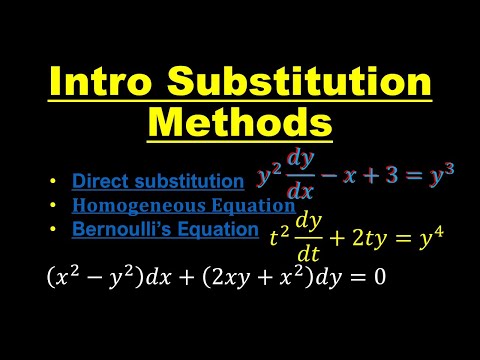
6:36
Introduction to Substitution Methods | Differential Equations
The Math Tutor
3.6K views
0:45
3 Forecasting Methods in Excel
Kenji Explains
124.2K views

0:21
Time Complexity of sorting methods - Best Case, Average Case, Worst Case/ Data structure - I
Education Guru
50 views

4:16
Spam Review Detection Using the Linguistic and Spammer Behavioral Methods | IEEE Projects Hyderabad
Cloud Technologies
240 views

42:40
AppSecIL 2018 - How to hack cryptographic protocols with formal methods, Ofer Rivlin
OWASP Israel
112 views
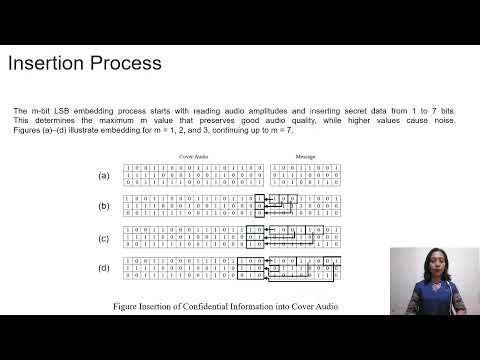
8:54
Comparison of the Use of M-Bit LSB Steganography Methods on MAV Files in Information Storage
imelda duma
20 views

3:23
CISSP -60 Security Architecture and Engineering: Understand methods of cryptanalytic attacks
sumon infosec
128 views

32:44
JNTUK R16 III CSE SEM2 CYBER SECURITY UNIT 4 INTRODUCTION TO TOOLS & METHODS USED IN CYBER CRIME LEC
RVIT — Autonomous, Guntur
1.8K views
0:16
Which One’s the Worst? Testing Dent Repair Methods on a Car!#car #dentrepair #Carlovers
Car Lover's Corner
25.9M views
7:54
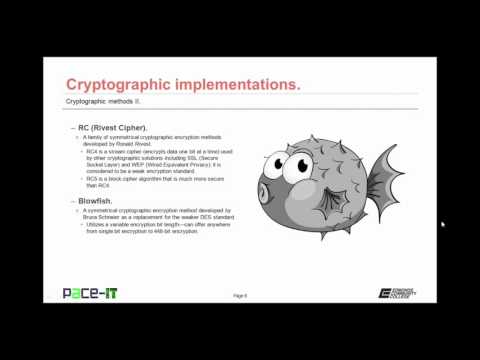
PACE-IT: Security + 6.2 - Cryptographic Methods (part 2)
PaceIT Online
249 views

9:31
Learn about Encryption Methods in CISSP Exam Prep Part 2 from GogoTraining
GogoTraining - PeopleCert Accredited (ATO)
240 views

0:44
Quantum Algorithm Achieves Major Speedup Over Classical Methods
AI Tech Pulse
1.3K views

52:55
Tools and Methods Used in Cybercrime Part 2 | Dr. Reshma Kadam
Reshma Patil
826 views
1:41
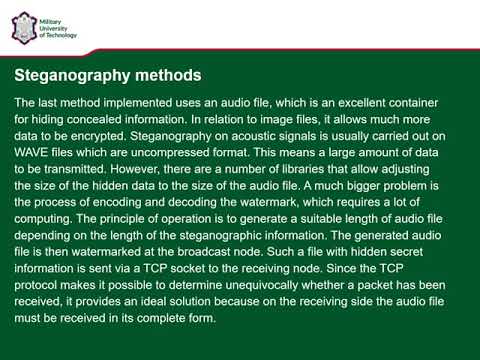
Implementation And Comparison of Three Network Steganography Methods
IBIMA Media
43 views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

18:54
Post Quantum Crypto - Lattice Methods
Bill Buchanan OBE
10.1K views

6:28
PACE-IT: Security + 6.2 - Cryptographic Methods (part 1)
PaceIT Online
233 views

35:11
Introduction to cost estimation methods in construction | Estimating project costs
Cost Engineering Professional
181.3K views
1:58
Cryptography and Formal Methods
Galois
3.4K views

1:43
4 Common Encryption Methods to Shield Sensitive Data From Prying Eyes
GetApp
2.2K views

1:03:24
Konstantinos Kartas: Nonstandard methods in almost mathematics
Hausdorff Center for Mathematics
177 views
1:10:03
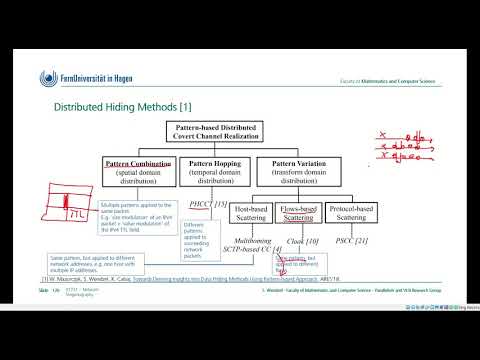
01731, Network Steganography, Chapter 6 (Distributed Hiding Methods), FernUniversität in Hagen
Steffen Wendzel
885 views

3:42
Securing ISF Data: Encryption and Integrity Methods!
ISF Solution
6 views
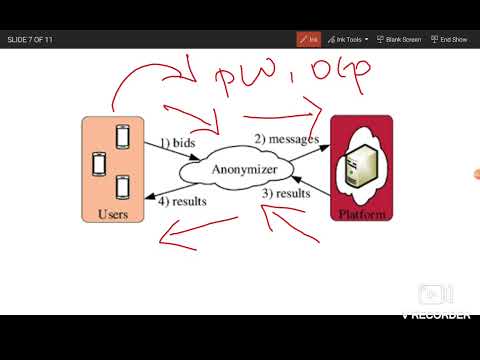
7:19
Tools and Methods in Cyber Security
Rohini CSE Tech Talk (RCTT)
630 views

24:31
KGB HQ - All Methods - Call of Duty Black Ops Cold War
AFGuidesHD
2.0M views

10:21
#59 Internet Key Exchange - Phases, Modes, Methods |CNS|
Trouble- Free
72.1K views
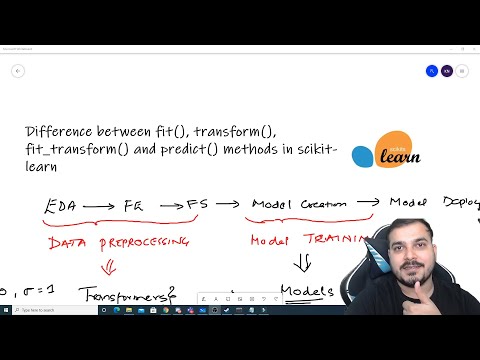
26:03
Difference Between fit(), transform(), fit_transform() and predict() methods in Scikit-Learn
Krish Naik
104.8K views

18:56
Python Crash Course #3 - Methods & Functions
Net Ninja
32.4K views

1:21
How To Open Password Protected PDF File (2 Methods)
ezyZip
31.8K views

0:16
Which Year Was Better? The Evolution of Car Paint Removal Methods! #car #paintremoval #Carlovers
Car Lover's Corner
74.7M views

1:06:28
Benchmarking and Survey of Explanation Methods for Black Box Models | AISC
LLMs Explained - Aggregate Intellect - AI.SCIENCE
647 views

7:04
The Caesar and other methods - Cryptography
Alexandra Georgieva
20 views

6:40
Lec - 22: Clustering in Data Mining Explained | Top Clustering Methods You MUST Know!
Gate Smashers
64.5K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

5:46
Classical Cryptography, the Evolution of Early Methods for Protecting Information
A Channel
55 views

4:19
#26 Symmetric Key Distribution - Methods |CNS|
Trouble- Free
142.8K views