Search Results for "modes of operations in information security"
Find videos related to your search query. Browse through our collection of videos matching "modes of operations in information security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "modes of operations in information security"
50 results found

0:53
Computer Security: Personal Information & Passwords : Is it safe to send personal information in an email?
VideojugTechnologyandCars
1 views

54:30
Designing an Information Architecture to Support Cyber Security and Information Assurance
Tech
213 views

0:08
Read Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Bbuhler
0 views

0:05
Read Multidisciplinary Perspectives in Cryptology and Information Security (Advances in Information
Ssanner
0 views

0:05
Read Information Assurance: Security in the Information Environment (Computer Communications
Hecke
0 views

9:15
CISSP Cyber Security Cryptographic Modes ECB CBC CFB OFB Counter Ciphers #cryptographicsystems
Cyber Security Cartoons
97 views

25:33
Block Cipher Modes of Operation : Explanation of all 4 types | Cryptography and Network Security
Lectures by Shreedarshan K
2.9K views

1:20:15
CS 370 Introduction to Security Lecture 4 -- Block Cipher Modes
Hack the Planet with Yeongjin Jang
263 views

5:44
Block Cipher Modes - CompTIA Security+ SY0-501 - 6.2
Professor Messer
95.4K views

36:01
Block Cipher Modes - Cryptography - Cyber Security - CSE4003
Satish C J
10.5K views

26:15
07-Network Security: Block Cipher Modes 🔄 | ECB, CBC, CFB, OFB & CTR Explained
Sundeep Saradhi Kanthety
172.5K views

10:28
Block Cipher Modes Of Operation | Computer Networking and Security | Simplilearn
Simplilearn
2.2K views

16:55
Block cipher modes cryptography cyber security cse4003
CodeFix
3 views

17:48
Network security block cipher modes of operation
CodeKick
2 views
7:44
Algorithm Modes & Algorithm Types in Network Security - ECB | CBC | CFC | OFB | CTR
Simple Snippets
11.5K views

10:57
Block Cipher Modes of Operation | Cryptography and System Security (Reshoot)
Ekeeda
70 views

7:50
Cryptographic Modes of Operation - CompTIA Security+ SY0-701 - 1.4
LabCyber
162 views
![[UNIF 2021] Checking Symbolic Security of Cryptographic Modes of Operation](/image/i.ytimg.com/vi/nD8bB3Ulses/xhqdefault.jpg.pagespeed.ic.Crwj9K2kW8.jpg)
25:02
[UNIF 2021] Checking Symbolic Security of Cryptographic Modes of Operation
FSCD 2021
16 views
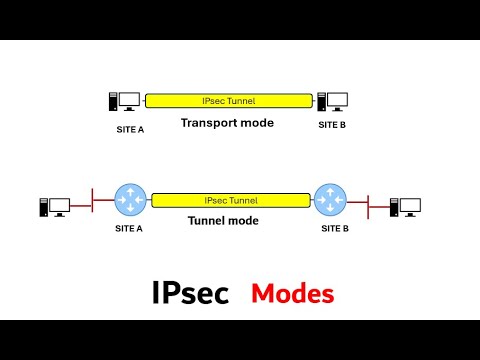
1:24
IP security modes - Transport mode and Tunnel mode quick explanation
NETWORKING WITH H
3.6K views

8:38
IPsec Explained Simply: A Deep Dive into VPN Security Protocols (IKE, AH, ESP, Tunnel Modes)
LevelUP I.T.
43 views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

12:03
VIGENERE CIPHER LESSON 7 |Polyalphabetic cipher|Cryptography& network security| Information security
Shashi KS
94 views

6:58
Vigenere cipher in easy | huzu's tution | Information Security | cyber security #education #cipher
Cyber Geek
148 views

7:31
Basics Of Network Security ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
288.9K views

14:25
#3 Types Of Security Attacks- Active & Passive Attacks and their Types |Information Security|
Trouble- Free
105.8K views

1:09
12 Security Technologies & Controls ISACA CISM DOMAIN 3 INFORMATION SECURITY PROGRAM
TUTORIAL
330 views

0:30
counter mode- Decryption | information security | cyber security #studyeasierbypoojapatel
Pooja Patel
106 views

1:31
Symmetric cipher model in Hindi || Information Security and Cyber Security || Study easier by Pooja
Pooja Patel
126 views

11:28
Information Security || Security Attacks | In Urdu
Computer Tech
40 views

1:45
Asymmetric key cryptography || Public key cryptography || Information security and cyber security
Pooja Patel
41 views

9:03
#6 Model for Network Security | Information Security |
Trouble- Free
66.5K views
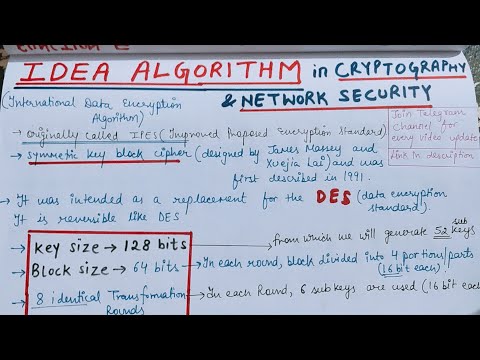
21:58
IDEA ALGORITHM in Cryptography and Network Security | Information Security
Abhishek Sharma
120.3K views

10:35
Security Mechanisms ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
204.3K views

8:02
#1 Introduction & Need for Security- Cryptography, Information Security
Trouble- Free
277.9K views
7:08
LECTURE – 36- COMPUTER NETWORKS AND SECURITY -INFORMATION SECURITY (MODULE-4) – BCA S3
BOSCOCAMPUSVISION
150 views

11:43:45
Learn Cryptography and Network Security in 12 Hours || Information Security || CNS || IS
Sundeep Saradhi Kanthety
6.2K views

0:14
security attacks ||types of attacks in information security||
Notice Point
6.7K views

8:24
Security Services ll Categories ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
191.9K views

9:17
Network Security Model ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
225.3K views

20:28
01-Network Security Basics Explained 🔐 | Information Security, Encryption & Decryption for Beginners
Sundeep Saradhi Kanthety
468.0K views

4:49
KERBEROS in cryptography and network security in Hindi information security and IT LAWS polytechnic
CSJM CLASSES INSTRUCTOR RAM SWAROOP
8.2K views

5:38
Vigenere cipher in cryptography and network security | Vigenere cipher in Information Security
Techystudy Best Learning Online
98 views

5:29
#16 Concept Of Steganography in Network Security |Information Security|
Trouble- Free
49.7K views

0:21
Security for Telecommunications Networks Advances in Information Security Pdf
tristancharles
3 views

0:05
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Kurtanidze 83
0 views
![[PDF] Operational Semantics and Verification of Security Protocols (Information Security and](/image/s1.dmcdn.net/v/FVG161e0X8s_TZyY4/xx720.pagespeed.ic.3BE1Bzcodl.jpg)
0:07
[PDF] Operational Semantics and Verification of Security Protocols (Information Security and
SoletteHawkins
8 views

0:08
Read Towards Hardware-Intrinsic Security: Foundations and Practice (Information Security and
Mzildjian
0 views

0:07
Read Security for Telecommunications Networks (Advances in Information Security) PDF Online
Thierse
2 views
Previous Page 2