Search Results for "importance of security protocols"
Find videos related to your search query. Browse through our collection of videos matching "importance of security protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "importance of security protocols"
50 results found

10:16
Cryptography and Network Security Protocols - Part 8
Information Security Awareness
25 views
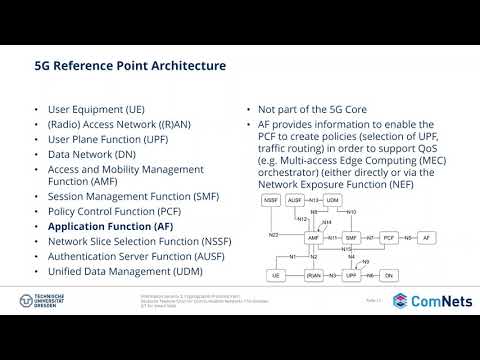
28:46
L13 - 01 - Information Security 2 - Cryptographic Protocols Part 1
ComNets Lectures
127 views

0:41
Crypto Security Protocols for Investors
Crypto Compass
2 views

1:02:29
Security of Quantum Key Distribution Protocols – Ph.D. Thesis Seminar by Rotem Liss
Rotem Liss
66 views

3:30
Wireless Cryptographic Protocols - CompTIA Security+ SY0-501 - 6.3
Professor Messer
68.6K views

20:31
27-Secure Socket Layer (SSL) Part 2 | Handshake & Alert Protocols | Cryptography & Network Security
Sundeep Saradhi Kanthety
90.1K views

11:19
USENIX Security '23 - Automated Analysis of Protocols that use Authenticated Encryption: How...
USENIX
148 views

13:37
SSL/TLS Protocols Explained: Security, Encryption & the Handshake Process
CodeLucky
35 views
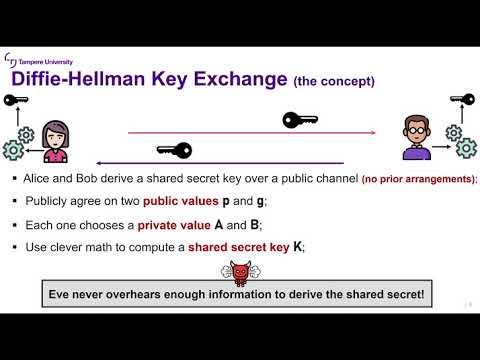
24:31
Security Protocols: Lecture 2d (Asymmetric Encryption)
Antonis M
415 views
3:05
How Do Cryptographic Protocols Like RSA Secure Network Security? - Talking Tech Trends
TalkingTechTrends
1 views
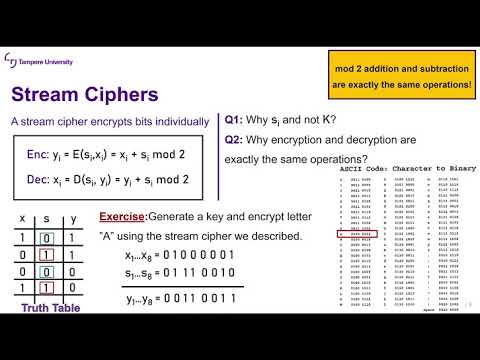
41:18
Security Protocols: Lecture 2c (Symmetric Encryption)
Antonis M
557 views

3:17
How Do Network Security Protocols Like HTTPS Protect Your Data? - Talking Tech Trends
TalkingTechTrends
1 views
17:04
UNIT IV-COMMUNICATION SECURITY,AUTHENTICATION PROTOCOLS
janadeep n
24 views

3:40
How Do Encryption Protocols Work Within Cloud Security? | Cloud Stack Studio News
Cloud Stack Studio
0 views
11:30
Client Work (Coursework)COMP.SEC.220 Security Protocols & Functional Encryption| Tampere University
Europe Assignment Helper
4 views

2:04
STRICT SECURITY PROTOCOLS FOR ERLA
CCNTV6
624 views

0:06
Read Security Protocols Ebook Free
Sgarcha
0 views

14:04
Quantum Protocols for Secure Communication: The Future of Digital Security
Quanten Deep-Dive Podcast
78 views

5:11
How Do Quantum Computers Threaten Current Security Protocols? - Next LVL Programming
NextLVLProgramming
0 views

3:08
SSL and TLS Explained: Secure Communication Protocols for Web Security
CodeLucky
5 views

0:08
Read Bundle: Network Defense: Fundamentals and Protocols + Network Defense: Security Policy
Sbjorn
0 views

13:26
Essential Guide to Network Security and Wireless Protocols | Insights from a Cybersecurity Expert
Skillfloor
6 views
![[PDF] Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security](/image/s1.dmcdn.net/v/FVODb1e98sGL1pB3Q/xx720.pagespeed.ic.r2Q32Sqpki.jpg)
0:05
[PDF] Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security
OceaNewton
3 views

0:06
Read Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security
Bgerstner
0 views

12:53
Narendra Modi's security enhanced with special protocols
Inkhabar
0 views

2:27
Updated security protocols announced for international flights
Daily News
0 views

1:58
PCI Requirement 4.1 – Use Strong Cryptography & Security Protocols to Safeguard Sensitive CHD
KirkpatrickPrice
1.3K views

1:56
Security Protocols (TLS), Public-Key Cryptography, X.509 & Certificate Issuance
Carizmian
496 views
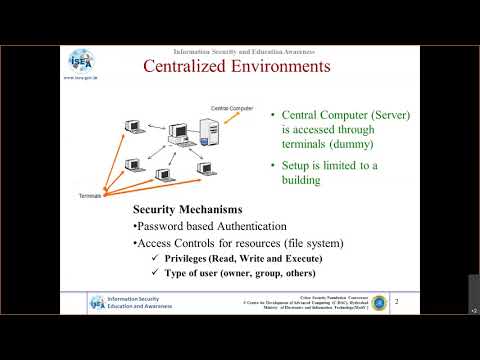
10:34
Cryptography and Network Security Protocols - Part 1
Information Security Awareness
87 views

1:23:30
Proving the security of real-world cryptography and protocols by Jonathan Protzenko
CS Research Week
68 views

0:16
What is Port 49? #cybersecurity #ports #protocols #security #networking #learnnetworking #learn
Sean Talks Cybersecurity
247 views
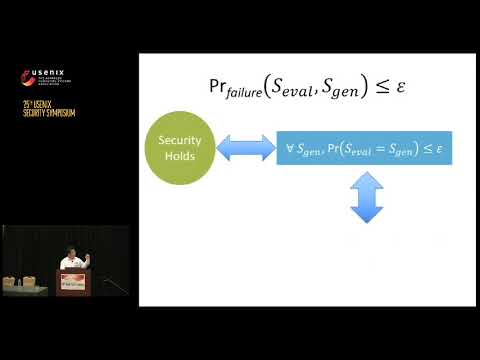
21:55
USENIX Security '16 - The Cut-and-Choose Game and Its Application to Cryptographic Protocols
USENIX
186 views
13:57
HTTPS Security | SSL | TLS | Network Protocols | System Design
ByteMonk
28.7K views

21:02
The Price of Active Security in Cryptographic Protocols
Rg G
2 views

21:02
The Price of Active Security in Cryptographic Protocols
IACR
346 views

8:38
IPsec Explained Simply: A Deep Dive into VPN Security Protocols (IKE, AH, ESP, Tunnel Modes)
LevelUP I.T.
43 views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

44:53
Networks Security | Security Services | Security Goals | Cryptography | Steganography | Attacks | IA
Bhavishya Coaching SGNR
929 views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

9:23
MIME protocol in Cryptography and Network Security | Email security in Network Security
Abhishek Sharma
119.7K views

3:42
GuardMe Security - Home Security Systems & Commercial Security Systems
Craig Metzger
5 views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

4:53
Cyber Security in hindi | Cyber security | What is cyber security
hackploit
18 views

5:30
What is security , information security and cyber security
Noor_khan official
3 views