Search Results for "how to avoid ransomware attacks"
Find videos related to your search query. Browse through our collection of videos matching "how to avoid ransomware attacks". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "how to avoid ransomware attacks"
50 results found

0:14
Paris Attacks-Attacks during football match
Media Updates
18 views
17:00
Paris attacks compilation: ISIS attacks on Stade de France and Bataclan in France
TomoNews US
1 views

4:08
Animal Attacks ➤ Piranha Fish Attack Human ➤ Piranha Attacks Video
DESI MASTI TV
71 views

11:07
Animal Attacks , Large Animal Attacks Human attack larger animals attack humans
Habibie Faizal
5 views

11:27
Wild Animal Attacks Leopard Hunting - Cheetah Attacks Animals Attack -
sadi
103 views
![What is DDos Attacks? DDoS Attacks Detail Explained in [Hindi/Urdu]](/image/s2.dmcdn.net/v/I0tbF1e0P3K1AaRkh/xx720.pagespeed.ic.BBA9JaC4dM.jpg)
6:46
What is DDos Attacks? DDoS Attacks Detail Explained in [Hindi/Urdu]
TechInfoEdu
36 views

1:26
Elephants attacks - Animals attack - Animals attacks videos
Animal Channel
1 views

5:00
What Causes Panic Attacks? Panic Attacks Cause
alextaylor1720
60 views

5:01
What Causes Anxiety Attacks? Causes of Anxiety Attacks
alextaylor1720
287 views

3:58
{Wild Animals Attacks} Animals Attack Snake Attacks | Animal Fails
HaseenA ShaiK
61 views

10:55
Leopard attacks dog, dog attacks leopard dog wins
WildFilmsIndia
94 views

10:55
Leopard attacks dog dog attacks leopard dog wins
WildFilmsIndia
2 views

5:07
J&K Terrorist attacks: Pakistan High Commission condemns terrorist attacks in Jammu
NewsX
322 views

2:34
Fauci says attacks on him are 'attacks on science'
USA Spot News
15 views

2:27
Panic Attacks Treatment | Stop Panic Attacks
Ashish Kumar
61 views

2:57
Most Amazing Wild Animal Attacks - Crocodile vs Zebra - Crocodile Attacks Zebra - Lion vs Zebra
Tout est art
822 views

6:20
Animal attacks - Best cheetah attacks - fastest predator
Hadeer cA TV
3 views

14:51
Attacks and animal fights! Attacks of lions, leopards, cheetahs and hyenas in the wild
Animal Kingdom Page
3 views

2:16
Panic Attacks and Anxiety Attacks
curepanicattacksinfo
2 views

1:31
Stop panic attacks & anxieties; panic attacks symptoms and help
stockm74
12 views

1:48
Stop Panic Attacks | Stop Anxiety Attacks
thepanicstopper
215 views

4:01
Cryptographic Attacks Explained | Common Attacks & How They Work
Cyberconnect
454 views

18:03
02-Types of Attacks in Network Security | Active vs Passive Attacks | Cryptography &Network Security
Sundeep Saradhi Kanthety
406.7K views

4:01
Ransomware and Crypto-Malware - CompTIA Security+ SY0-501 - 1.1
Professor Messer
366.5K views

3:19
Ransomware's New Game Plan: Why Data Exfiltration is the Latest Threat
Infinity Space
1 views

41:33
DEF CON 25 Crypto and Privacy Village - Mark Mager - Cryptanalysis in the Time of Ransomware
DEFCONConference
1.6K views
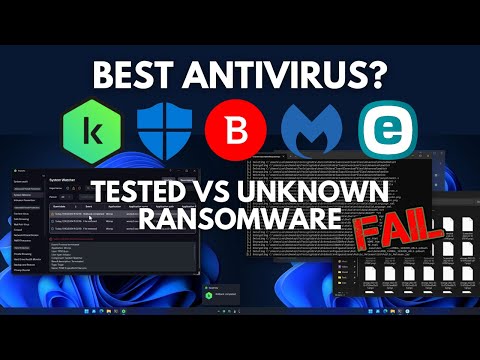
6:28
Best Antivirus vs Unknown Ransomware II
PC Security Channel
231.9K views

15:58
The Hacker Who Built a Ransomware Empire
Blackfiles
153.5K views
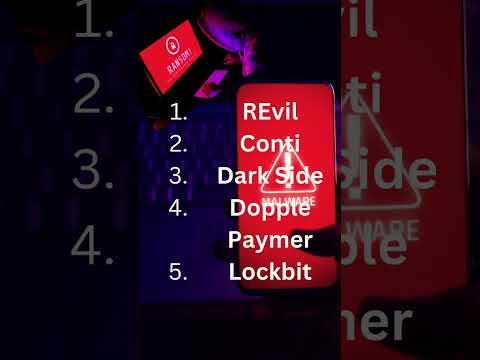
0:16
🔐🔑Top 5📢Ransomware 🗞Gangs💰💰 #cryptography #viral #youtubeshorts #reels #cryptology #cryptanalysis
Tech Lover
57 views
1:27
Ponto de armazenamento da chave de criptografia do Ransomware no arquivo criptografado..
Diógenes Santos
536 views

54:57
Ransomware Encryption Internals: A Behavioral Characterization by Antonio Cocomazzi
scrt.insomnihack
1.0K views

0:42
Lynx Ransomware: How Hybrid Tactics Threaten Global Organizations and Cut Costs
Hacked dAily
30 views

4:55
What is Cybercrime? Types of Cybercrimes-Hacking Phishing Ransomware Cyberstalking DDoS Piracy etc.
Management Tutorials
13.3K views

0:46
2025 Cyber Threats: Ransomware & Beyond
IBM Technology
20.9K views
0:23
ransomware live attack | live Android hack
Anonymousploit
117.1K views

0:30
VerdaCrypt Ransomware: Exploring Its Unique Philosophy and PowerShell Encryption Techniques
Hacked dAily
14 views

0:58
Rust being used in Ransomware
Apna College
886.0K views

0:47
What's a Ransomware Attack?
Legal Consultant - Dr Hassan Elhais
172 views

9:08
Malware and its types l Virus, Worms, Trojan, Ransomware, Adware and Spyware Explained in Hindi
5 Minutes Engineering
107.4K views

0:39
The SCARIEST And DANGEROUS Malware ☠️ (Hexa Ransomware)
CYBER SOLDIER
111.6K views

2:38
Ransomware Explained in Under 3 Minutes
CCAWorks
61.3K views

10:01
Dealing with a Ransomware Attack: A full guide
PC Security Channel
500.9K views

0:16
🔥💰Ransomware🔐🔑 Attack🤔🤐#youtubeshorts #viral #cryptography #reels
Tech Lover
267 views

5:19
Le Ransomware expliqué en 5 minutes
Cookie connecté
47.3K views

2:28
The truth about ransomware
VICE
50.6K views
13:07
2025 Threat Intelligence Index: Dark Web, AI, & Ransomware Trends
IBM Technology
54.1K views

12:48
What is Ransomware?
IBM Technology
52.4K views
1:03
Ransomware Just Got WAY WORSE
Zach's Tech Turf
459.5K views

17:37
TWIM Episode 2: Sodinokibi Ransomware Vulnerabilities & Maryland Criminalizes Malware Possession
This Week in Malware
66 views

35:36
From Cryptography to Ransomware Defence: Bob Blakley’s 49-Year Journey & Mimic Security
CyberBytes: The Podcast
10.8K views
Previous Page 2