Search Results for "hash functions in blockchain"
Find videos related to your search query. Browse through our collection of videos matching "hash functions in blockchain". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hash functions in blockchain"
50 results found

5:33
Inverse Trigonometric Functions - Functions
Saameer Mody
2 views

13:47
Relation and Functions Part 6 (Graphs of functions ) Mathematics CBSE Class X1
examfear
1 views

1:43
Inverse Trigonometric Functions - Algebra Functions
Saameer Mody
224 views

3:56
Inverse Trigonometric Functions - Composition of Functions
Saameer Mody
227 views

0:18
Linear functions have a constant rate of change and graph as Linear functions#amanyt #sirajshaikh#pw
Ravaan Tutorial
1.0K views

12:12
9 Statistical functions in Excel you need to know | Excel Functions
Excel Tutorial
3.2K views
![[Chapter 2a] Cryptography II + Hash Functions & Wordlists](/image/i.ytimg.com/vi/-lCGZIPeExI/hqdefault.jpg)
2:16:21
[Chapter 2a] Cryptography II + Hash Functions & Wordlists
Avocado
5.9K views

0:51
One way hash functions explained #shorts
Standard Edition Security
225 views

7:27
Hash Functions 🔥🔥
Perfect Computer Engineer
159.9K views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views
![[CompNetSec] - 13 - Cryptographic Hash Functions](/image/i.ytimg.com/vi/2yxHePuitJc/hqdefault.jpg)
1:00:43
[CompNetSec] - 13 - Cryptographic Hash Functions
Hicham Elmongui
7.3K views
26:57
CH3 Cryptographic Hash Functions 1
د محمود-الحاسبات وتقنية المعلومات
293 views

0:56
Cryptographic Hash Functions
Mathematical Minutes
46 views
6:50
Cryptographic Hash Functions (Part 1): Overview
Sourcefire
52.3K views
24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views

49:06
Cryptographic Hash Functions (Contd...2)
nptelhrd
8.8K views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

7:28
Passwords & hash functions (Simply Explained)
Simply Explained
389.8K views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

9:50
Cryptography Explained. Symmetric and Asymmetric Encryption. Hash functions. Digital signatures.
Encyclopedia
136 views

59:18
CSE571-11-11: Cryptographic Hash Functions
Raj Jain
8.1K views
1:36:49
Winter School on Cryptography Symmetric Encryption: Cryptanalysis of Hash Functions - Eli Biham
Bar-Ilan University - אוניברסיטת בר-אילן
632 views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views
2:12
Cryptographic Hash Functions in 2 Minutes
2 Minute Expert
160 views

0:54
🔑 What is Hashing? | Hash Functions & Collision Handling Explained | Java Data Structures #dsa
Dev Dood
186 views

32:39
Four* non-cryptographic hash functions enter. One leaves. by Adam Harvey
PyCon AU
852 views

3:58
What Are Cryptographic Hash Functions And How Are They Used? - Next LVL Programming
NextLVLProgramming
16 views

18:43
Lecture 1.1 - Cryptographic Hash Functions
MyDigitalDiary
1.7K views
16:59
Hash Functions in Cryptography
Abhishek Sharma
544.2K views

0:48
Power of Cryptographic Hash Functions
BTC Bill
217 views

12:16
How Does SHA-1 Work - Intro to Cryptographic Hash Functions and SHA-1
Fullstack Academy
69.1K views

1:22:01
21. Cryptography: Hash Functions
MIT OpenCourseWare
190.7K views

43:07
On Attacking Hash functions in Cryptographic schemes
Simons Institute for the Theory of Computing
962 views

3:47
7.2 Security Requirements for Cryptographic Hash Functions
EngiNerd
152 views

15:34
Symmetric and Asymmetric Key Cryptography, Hash Functions
Information Security Awareness
192 views
1:09:00
Hash Functions ☆ Requirements & Security ☆ IT Lecture
Lernvideos und Vorträge
233 views

0:44
Decoding Bitcoin How Cryptographic Hash Functions Work
Maxwealth Shorts
60 views

22:07
Basics of Cryptology – Part 13 (Modern Cryptography – Cryptographic Hash Functions)
Cryptography for Everybody
2.9K views

1:05:04
Lecture 20: Hash Functions by Christof Paar
Introduction to Cryptography by Christof Paar
72.0K views

15:26
Security Protocols: Lecture 2e (Cryptographic Hash Functions & Communication Integrity)
Antonis M
322 views
1:31:45
Overview of Cryptography topics (Symmetric ciphers, hash functions, Asymmetric encryption, PRGs)
Ricardo Calix
72 views

7:39
Hashing & Cryptographic Hash Functions - Explained
Crypto Catch Up
2.6K views
![[cryptography series] episode 4 : "hash functions"](/image/i.ytimg.com/vi/VkNJe4_Yug0/hqdefault.jpg)
24:52
[cryptography series] episode 4 : "hash functions"
CLEARSEC
168 views

8:21
Cryptographic Hash functions under 10 mins
CyberApe
9 views

17:52
The PHOTON Family of Lightweight Hash Functions (Crypto 2011)
IACR
1.9K views

7:04
Cryptographic Hash Functions - CompTIA Security+ SY0-401: 6.2
Professor Messer
46.0K views
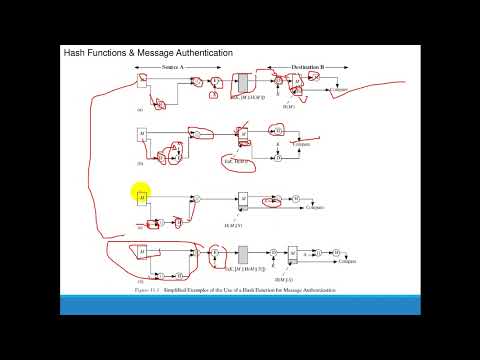
12:41
Chapter 11 - Cryptographic Hash Functions
j neama
6.7K views

24:26
Learn Cryptography | Part 5 - Hash Functions
Cryptosense
1.4K views
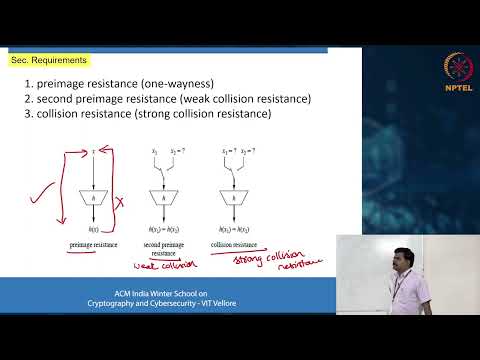
1:19:45
Hash Functions, Digital Signatures and Quantum Cryptography
Aswani Kumar Cherukuri
165 views

15:04
Lesson 14: One-way and hash functions (intypedia)
UPM
7.9K views