Search Results for "hash functions explained"
Find videos related to your search query. Browse through our collection of videos matching "hash functions explained". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hash functions explained"
50 results found

49:06
Cryptographic Hash Functions (Contd...2)
nptelhrd
8.8K views

1:02:56
Network Security - Cryptographic Hash Functions (Security Requirements and Attacks)
Waqas Ali
125 views
1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views
16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views
39:09
Cryptography Hash Functions (CSS322, L18, Y14)
Steven Gordon
1.1K views

0:16
🛡️Cryptographic Hash Functions 🔒 #knowledge #shorts #short #tech
TechWiseNow
81 views

0:51
Exploring Cryptographic Hash Functions
esperanza
26 views

0:41
Understanding Crypto Hash Functions
Crypto Bytes Basics
74 views

48:34
ZKPodcast: Alan Szepieniec on Hash Functions & Supersonic SNARKs
Zero Knowledge
147 views

59:18
CSE571-11-11: Cryptographic Hash Functions
Raj Jain
8.1K views
1:36:49
Winter School on Cryptography Symmetric Encryption: Cryptanalysis of Hash Functions - Eli Biham
Bar-Ilan University - אוניברסיטת בר-אילן
632 views

15:24
Cryptographic Hash Functions: Part 1
myAcademic-Scholartica
9.4K views

3:17
Cryptographic Security: Understanding Hash Functions and Their Implications for Investment in 2025
Crypto Luminary
4 views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views
2:12
Cryptographic Hash Functions in 2 Minutes
2 Minute Expert
160 views

15:29
Lesson 01 - Symmetric Cryptography and Asymmetric Cryptography, Hash Functions
Sayed Mansoor Rahimy
16 views

22:14
V3d: Iterated hash functions (Applied Cryptography 101)
Cryptography 101
639 views

21:15
MD5 in Hindi - Message Digest, Hash Functions, Working and Operation of MD5 - Network Security
Easy Engineering Classes
263.7K views

0:52
Exploring Cryptographic Hash Functions in Crypto Investments
Cryptonic
61 views

18:31
Fingerprinting with Hash Functions
Aleksander Essex
9.4K views

2:43
#23 - Cryptographic Hash Functions Examples | Blockchain Tutorial Series @FameWorldeducatonalhub
FAME WORLD EDUCATIONAL HUB
388 views

32:39
Four* non-cryptographic hash functions enter. One leaves. by Adam Harvey
PyCon AU
852 views

3:58
What Are Cryptographic Hash Functions And How Are They Used? - Next LVL Programming
NextLVLProgramming
16 views
17:23
Two Simple Hash Functions
Dr. Chandra Sekhar Sanaboina
7.2K views

6:57
Cryptographic Hash Functions - CompTIA Security+ SY0-301: 6.2
Professor Messer
21.2K views

18:43
Lecture 1.1 - Cryptographic Hash Functions
MyDigitalDiary
1.7K views
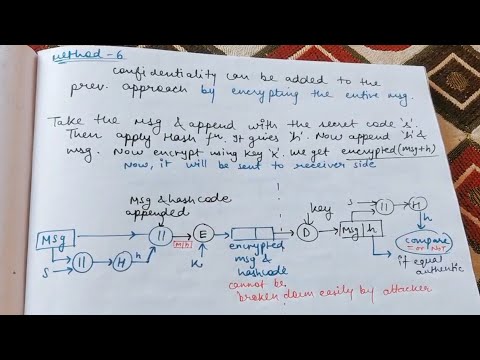
16:59
Hash Functions in Cryptography
Abhishek Sharma
544.2K views

11:16
Hashes 4 Hash Functions for Strings
RobEdwards
73.6K views

7:20
CRYPTOGRAPHY | HASH Functions
Irsa Khan
137 views

0:48
Power of Cryptographic Hash Functions
BTC Bill
217 views

5:37
Properties of Hash Functions 🔥
Perfect Computer Engineer
59.0K views
12:16
How Does SHA-1 Work - Intro to Cryptographic Hash Functions and SHA-1
Fullstack Academy
69.1K views
1:19:45
Hash Functions, Digital Signatures and Quantum Cryptography
Aswani Kumar Cherukuri
165 views

1:22:01
21. Cryptography: Hash Functions
MIT OpenCourseWare
190.7K views

43:07
On Attacking Hash functions in Cryptographic schemes
Simons Institute for the Theory of Computing
962 views

3:47
7.2 Security Requirements for Cryptographic Hash Functions
EngiNerd
152 views
28:25
Cryptography/SSL 101 #2: Cryptographic hash functions
Matt Thomas
15.6K views

4:33
SSMRV Video Lectures-Cryptography and Network security-Hash Functions
SSMRV College
211 views

15:34
Symmetric and Asymmetric Key Cryptography, Hash Functions
Information Security Awareness
192 views

6:06
Cryptography Basics: Securing Blockchain | Hash Functions, Public Keys & Digital Signatures
CodeLucky
6 views
1:09:00
Hash Functions ☆ Requirements & Security ☆ IT Lecture
Lernvideos und Vorträge
233 views

5:48
Introduction to Cryptography: Hash Functions
Wolfram U
200 views

0:16
How Blockchain Uses Hash Functions #HashFunctions #Blockchain #cryptotrends2024
Daily crypto predictions
41 views
21:18
Property-Preserving Hash Functions for Hamming Distance from Standard Assumptions
IACR
353 views
40:53
Attacks on Hash Functions
Dr. Chandra Sekhar Sanaboina
1.5K views
0:11
Hash Functions 🔄 || #shorts #knowledge #learning #blockchain
TechWiseNow
1.2K views

0:11
Crypto Fact #192 Hash Functions
April Token
236 views

0:44
Decoding Bitcoin How Cryptographic Hash Functions Work
Maxwealth Shorts
60 views

0:55
Decoding Cryptocurrency Hash Functions
Crypto Simplified 101
56 views

22:07
Basics of Cryptology – Part 13 (Modern Cryptography – Cryptographic Hash Functions)
Cryptography for Everybody
2.9K views