Search Results for "encrypted remove"
Find videos related to your search query. Browse through our collection of videos matching "encrypted remove". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "encrypted remove"
50 results found

21:21
HYBRID CRYPTOGRAPHY AND STEGANOGRAPHY METHOD TO EMBED ENCRYPTED TEXT MESSAGE WITHIN IMAGE
VERILOG COURSE TEAM-MATLAB PROJECT
493 views
0:43
The Unsolved Mystery of Kryptos: CIA's Encrypted Sculpture!
Mystery Stories of the World 🌎
612 views
10:37
Authentication by Encrypted Negative Password in Python
OKOKPROJECTS
183 views

0:47
The Encrypted Messages of World War II
CineDecoded
54 views

54:29
Charalampos Papamanthou: Leakage Abuse Attacks in Encrypted Databases
CMU Cylab Crypto Seminar
191 views
21:16
NSDI '20 - TimeCrypt: Encrypted Data Stream Processing at Scale with Cryptographic Access Control
USENIX
924 views

21:30
Computing On Encrypted Data // Kurt Rohloff, Duality (Firstmark's Data Driven NYC)
The MAD Podcast with Matt Turck
482 views
4:40
Reversible 3D encrypted image steganography with lossless recovery using MATLAB
IEEE Projects Bengaluru
27 views

0:52
LOSSLESS AND REVERSIBLE DATA HIDING IN ENCRYPTED IMAGES WITH PUBLIC KEY CRYPTOGRAPHY
KI Tech Solutions
92 views
2:49
Lossless and Reversible Data Hiding in Encrypted Images with Public Key Cryptography
finalsemprojects
458 views

52:37
12 Jan 2015, Computing on Encrypted Data - Somewhat Homomorphic Encryption
Secure IoT at Stanford
3.8K views

59:15
Computing On Encrypted Data with C++
CoreCppIL
481 views
23:57
Efficient Boolean Search over Encrypted Data with Reduced Leakage
IACR
206 views

1:07:27
Lattices and Encrypted Computation
Simons Institute for the Theory of Computing
3.2K views
3:05
Encrypted Steganography using command prompt
HackerWorld
198 views
4:11
Separable Reversible Data Hiding in Encrypted JPEG Bitstreams
ArihantTechnoSolutions ATS
89 views
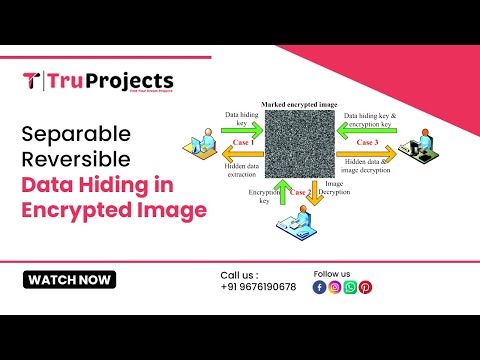
3:45
separable reversible data hiding in encrypted image FINAL BTECH - MTECH IEEE PROJECTS IN HYDERABD
TRU PROJECTS
96 views
0:21
encrypted passwords generator Using few lines of Python code#python #trending #short #shorts #viral
To-TechArea
907 views

3:25
How Is Data Encrypted With Asymmetric Encryption? - CryptoBasics360.com
CryptoBasics360
4 views

2:51
Understanding Cryptanalysis: Unlocking the Secrets of Encrypted Language
Vocabulary Vault
14 views

9:06
Make ANY Messaging Service E2E Encrypted With PGP
Mental Outlaw
86.4K views
13:54
Use These Before They're Banned: 7 Encrypted Services
Techlore
103.8K views
0:18
How To: Set Up Encrypted Backups on WhatsApp
WhatsApp
118.0K views

0:57
The Ultimate Offigrid Encrypted Comms Platform
The Tech Prepper
27.6K views

3:57
Navjaxx - Encrypted Memory (4K Official Music Video)
Navjaxx
1.8M views
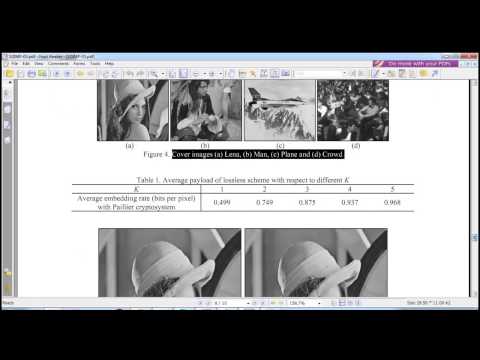
2:34
Lossless and Reversible Data Hiding in Encrypted Images with|IEEE MATLAB IMAGE PROCESSING 2015
SD Pro Solutions Pvt Ltd
2.6K views
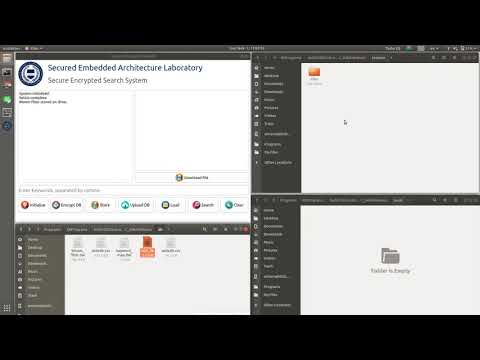
3:35
Encrypted Search Prototype for Cloud Infrastructure Using Searchable Symmetric Encryption
Secure Embedded Architecture Laboratory
218 views

0:56
WhatsApp end to end encrypted explained !
DEV KUMAR
164.5K views
13:48
A Privacy Preserving Multi Keyword Ranked Search Over Encrypted Data in Hybrid Clouds in Java
OKOKPROJECTS
34 views
6:29
Privacy Preserving Multi keyword Ranked Search over Encrypted Cloud Data
Xtream Technologies
159 views

3:10
Decryption : Process Of Converting Encrypted Data Into Plaintext Explained In Hindi
The Curious Lab
10 views

22:21
How To Use One-Time Pads To Send Encrypted Messages - Hak5
Hak5
170 views

22:21
How To Use One-Time Pads To Send Encrypted Messages, Hak5 1620
Hak5
17.9K views

27:35
Bootable Encrypted VHD (AES-256) (Disk Wipe Included)
BytezAutomations
2 views
0:38
Applying CNN to encrypted MNIST images
Shreya Garge
879 views

5:55
DARPA Awards Duality Technologies Multi-Million Dollar Contract to Accelerate ML on Encrypted Data
Duality Technologies
384 views

52:34
SDC 2017 - !Oxymoron: Encrypted (Database) Search - Srinivasan Narayanamurthy
SNIAVideo
82 views
13:46
Break an Encrypted Letter of a Child Killer
Cryptography for Everybody
1.6K views
2:11
how your computer sends encrypted information
Michael Penn
3.5K views

3:06
Cryptography Explained Part 2: Digital Signature & Encrypted Certificate
CyberTutor
84 views

17:01
Let's Decipher Two Encrypted English Postcards – Secret Messages From the Past Revealed
Cryptography for Everybody
586 views

1:07:03
Hoeteck Wee: Encrypted computation from lattices (1/3)
IDEAS NCBR
183 views

1:32:28
Shweta Agrawal: Encrypted computation from lattices (3/3)
IDEAS NCBR
76 views
56:40
Tutorial: Encrypted Computation from Lattices
Simons Institute for the Theory of Computing
1.4K views

0:43
Quantum Shield: A City Goes Encrypted
TechPulse Vision
84 views
2:25
Live Test of an Encrypted Call on Android phone using ...
MobileAppTester
11 views

3:04
Live Test of an Encrypted Call on iPhone using Cellcrypt Mobile
MobileAppTester
4 views

2:09
PDF File Decryption | Decrypt Encrypted PDF File after Password Forgot
Padany
1 views
3:32
WhatsApp ~ এর End to End Encrypted এর কাজ কি || How to Use Whatsapp End to End Encryption
TecH Bangla Info
10 views

8:58
WhatsApp ~ এর End to End Encryption কি এবং এর কাজ কি || How To Use End to End Encrypted Backup
TecH Bangla Info
3 views
Previous Page 2