Search Results for "cryptographic hash functions explained"
Find videos related to your search query. Browse through our collection of videos matching "cryptographic hash functions explained". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cryptographic hash functions explained"
50 results found
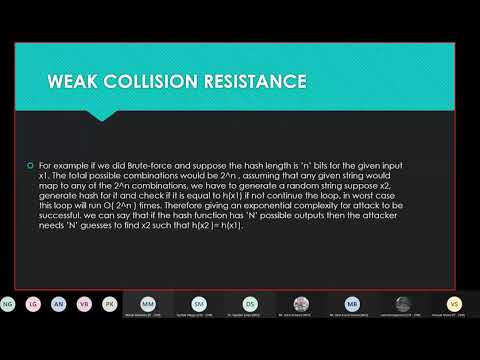
27:10
CryptoGraphic Hash functions and attack complexity Analysis
VS
30 views

8:21
Cryptographic Hash functions under 10 mins
CyberApe
9 views

0:42
Understanding Cryptographic Hash Functions in Cryptocurrency
Quantum Prosperity
58 views

7:04
Cryptographic Hash Functions - CompTIA Security+ SY0-401: 6.2
Professor Messer
46.0K views

0:35
Cryptographic Hash Functions – Break down how hashing secures blockchain data? #shorts
ankush
403 views
12:41
Chapter 11 - Cryptographic Hash Functions
j neama
6.7K views

13:18
Introduction to Cryptographic Hash Function| Merkel Damgard Scheme | SHA-256 | Secure Hash Algorithm
Muhammed Mustaqim
607 views

8:19
LEC11| Blockchain | Cryptographic Hash Function & Properties of Hash Function by Mrs. G. Sowmya
MLID - MLR Institute of Technology
2.3K views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views

0:51
One way hash functions explained #shorts
Standard Edition Security
225 views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views

7:28
Passwords & hash functions (Simply Explained)
Simply Explained
389.8K views

9:50
Cryptography Explained. Symmetric and Asymmetric Encryption. Hash functions. Digital signatures.
Encyclopedia
136 views

0:54
🔑 What is Hashing? | Hash Functions & Collision Handling Explained | Java Data Structures #dsa
Dev Dood
186 views
0:46
Hash Functions Explained in 60 Seconds! #learnandgrow #technology #blockchain #shorts #automation
MS Learning
679 views

4:00
How Do Hash Functions Work In Encryption Protocols? - Internet Infrastructure Explained
Internet Infrastructure Explained
1 views

0:57
Understanding SHA-1 & SHA-256 Hash Functions Explained
TWiT Tech Podcast Network
7.8K views

1:34
Hash Security, Pass-the-Hash, and PKI Explained | Security+ in 60 Seconds
Cyber Buddy
40 views
1:00
Cryptographic Hashing Functions Explained in Under 60 Seconds | The Bitcoin Advocate #shorts
The Bitcoin Advocate Podcast
120 views

1:01
What is cryptographic hash function in crypto? Explained!! #crypto #cryptocurrency #bitcoin
Niyas Kp
16 views

7:36
Cryptographic Hash Function Explained | How it works? | Properties | Uses and Examples
JXploit
13.8K views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

0:18
Linear functions have a constant rate of change and graph as Linear functions#amanyt #sirajshaikh#pw
Ravaan Tutorial
1.0K views

12:12
9 Statistical functions in Excel you need to know | Excel Functions
Excel Tutorial
3.2K views

0:32
3 dynamic array functions you need to know. Who knew all three of these functions?! ✋🏼 #excel
Excel Dictionary
18.0K views

39:14
Python Functions Tutorial | Working With Functions In Python | Python Training | Edureka
edureka!
159.2K views

13:47
Relation and Functions Part 6 (Graphs of functions ) Mathematics CBSE Class X1
examfear
1 views

3:56
Inverse Trigonometric Functions - Composition of Functions
Saameer Mody
227 views

1:43
Inverse Trigonometric Functions - Algebra Functions
Saameer Mody
224 views

5:33
Inverse Trigonometric Functions - Functions
Saameer Mody
2 views
![[Chapter 2a] Cryptography II + Hash Functions & Wordlists](/image/i.ytimg.com/vi/-lCGZIPeExI/xhqdefault.jpg.pagespeed.ic.QXc4mtbpKC.jpg)
2:16:21
[Chapter 2a] Cryptography II + Hash Functions & Wordlists
Avocado
5.9K views

0:37
Weak Hash Functions are a SECURITY RISK!
World Economic and Cryptocurrency News
1.1K views

7:27
Hash Functions 🔥🔥
Perfect Computer Engineer
159.9K views

0:51
Hash Functions
Gnana Lakshmi T C
149 views

57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

13:44
V3a: Hash functions: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
1.0K views

14:13
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views

24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views

16:13
ACISP2020 Tightly Secure Chameleon Hash Functions in the Multi User Setting and Their Applications
Xiangyu Liu
230 views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views
39:09
Cryptography Hash Functions (CSS322, L18, Y14)
Steven Gordon
1.1K views

0:16
🛡️Cryptographic Hash Functions 🔒 #knowledge #shorts #short #tech
TechWiseNow
81 views

0:41
Understanding Crypto Hash Functions
Crypto Bytes Basics
74 views

48:34
ZKPodcast: Alan Szepieniec on Hash Functions & Supersonic SNARKs
Zero Knowledge
147 views

1:36:49
Winter School on Cryptography Symmetric Encryption: Cryptanalysis of Hash Functions - Eli Biham
Bar-Ilan University - אוניברסיטת בר-אילן
632 views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

15:29
Lesson 01 - Symmetric Cryptography and Asymmetric Cryptography, Hash Functions
Sayed Mansoor Rahimy
16 views

22:14
V3d: Iterated hash functions (Applied Cryptography 101)
Cryptography 101
639 views