Search Results for "chaining technique in hashing"
Find videos related to your search query. Browse through our collection of videos matching "chaining technique in hashing". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "chaining technique in hashing"
51 results found

1:58
Cipher Block Chaining Mode - Applied Cryptography
Udacity
131.2K views
6:02
Symmetric-Key Cryptography: Block Ciphers & Chaining @DatabasePodcasts
Database Podcasts
4 views
0:56
What is Cipher Block Chaining? #shorts
Cyber Guys Podcast
463 views

0:54
What is a Hash Table? | Separate Chaining
Greg Hogg
65.3K views

7:18
CIPHER BLOCK CHAINING |Block Cipher Mode of opreation| CBC Mode Explain hindi
DK Technical Point 2.0
741 views

0:51
CBC Cipher Block Chaining Mode
Quick Cybersecurity Study
423 views
5:57
CIPHER BLOCK CHAINING USING AES AND BLOWFISH ENCRYPTION ALGORITHM
Kalva Venkata Naga Jyothi Swaroop
34 views

7:38
Block Cipher Mode : Cipher Block Chaining (cbc) Mode Explained in Hindi
5 Minutes Engineering
153.9K views

0:37
CBC - Cipher Block Chaining - Security+
Geekus Maximus
115 views

8:38
Cipher Block Chaining (CBC)
Neso Academy
99.6K views

4:43
CBC Mode | Cipher Block Chaining Mode | Application of CBC Mode
Chirag Bhalodia
14.4K views

7:40
Hash function based on CBC in cryptography | Hash function based on cipher block chaining
Chirag Bhalodia
24.0K views

21:33
Interrupt Initiated I/O|Priority| Daisy Chaining|Parallel Priority Encoder|Cycle | Modes of Transfer
Sudhakar Atchala
174.7K views

3:11
Smarter Service Chaining & New Ways to Benefit From Qosmos Technology
LightReading
1.6K views

1:00
SMOPS - chaining method
ruidurao
506 views
17:04
Hashing Technique - Simplified
Abdul Bari
847.6K views

39:28
Hashing Technique by Mr. Akhilesh Kumar Srivastava
CETL at ABES Engineering College
2.0K views

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views
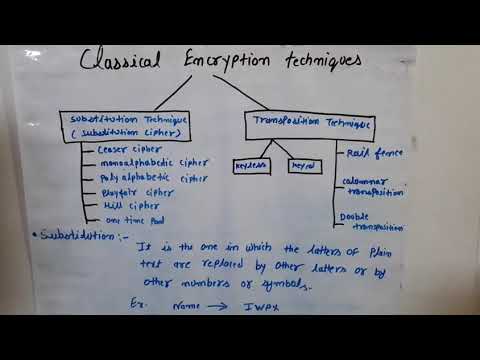
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

23:16
NIS-3.2-1 : Types of Cipher Technique (Substitution Cipher Technique, Caesar cipher)
rathod_sir
361 views

4:05
Substitution Cipher Technique V/s Transposition Cipher Technique in Cryptography and Network Securit
Short Tricks Learning
631 views

0:46
What technique do you use during competitive eating?: Competitive Eating Strategy And Technique
Scribble
1 views

5:42
Hair Cutting Technique: Mahogany Cutting Technique
Grant Sharp
8.7K views

4:30
Password Hashing, Salts, Peppers | Explained!
Seytonic
264.0K views

12:23
Encoding, Encryption and Hashing -- What's the Difference?
Auth0
3.4K views

7:01
CISM Domain 3 Preview | Hashing - Part 1
ThorTeaches.com: CISSP, CC, CISM, GenAI training
485 views

4:47
Hashing - Introduction to Hasing | C++ Placement Coure | Lecture 32.1
Apna College
248.5K views

23:26
Hashing and SSL Basics | Part 2 | | TryHackMe Intro to Cryptography
Motasem Hamdan
1.5K views

1:01:23
Hashing | Data Structure and Algorithms | NPTEl | IIT-OCW
IIT OCW
1.1K views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views
20:34
Introduction to Basic Cryptography: Hashing
Ryan Riley
39.2K views

6:37
Cryptography Explained: Encryption, Hashing, and Steganography
Cyberconnect
362 views

16:22
Hashing vs Encryption explained in-depth | 2025 | Tamil
Hareesh Rajendran
5.8K views

0:34
What is the difference between Encryption and Hashing
Andrew Jones
508 views

1:20:48
CySec101 / EP.23 / Hashing Basics / TryHackMe Cyber Security For Beginners
Hank Hackerson
1.6K views

1:26
Cybersecurity Shorts: Day 97 - What is HASHING ?
Shiva Ram Tech
1.4K views

0:31
What is the difference between encryption and hashing? #shorts
Nayyab's Lectures CS / IT
184 views

10:30
Introduction to HASHING in Data Structures || Hash Functions,Hash Table, Hash Keys,Hash Values in DS
Sundeep Saradhi Kanthety
11.5K views

2:15
Hashing ||In Hindi and English || Network security || for Exam preparation , Definition||#Shortvideo
Shukla Classes
52 views

9:13
Hashing in Blockchain Explained in Hindi
5 Minutes Engineering
74.4K views

7:40
Symmetric Encryption | Asymmetric Encryption | Hashing | Digital Signatures
Unriddle Tech
1.2K views
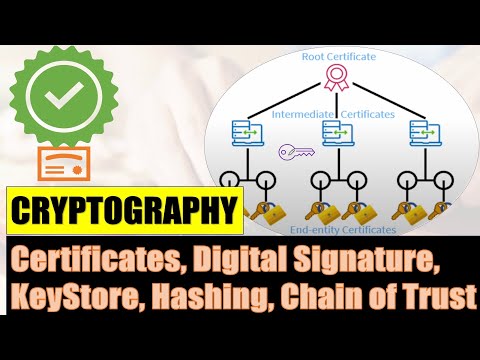
16:26
Cryptography Principles: Security, Certificates, Nexus Repository, Digital Signature, Hashing, Chain
@NurtureLearning
82 views
1:10
What is Hashing? | Crypto 101 | Episode 6
Insights 101
147 views
5:50
Hashing vs Encryption Explained in 5 Minutes
Vinsloev Academy
5.7K views

10:03
TYPES OF CRYPTOGRAPHY | Symmetric Cryptography, Asymmetric Cryptography and Hashing
Abhishek Sharma
502.7K views

8:23
"Understanding Cryptography Hashing vs Encryption Explained"
Hung Lee
10 views

1:05
Fast Authentication using Chameleon Hashing Key Chain
University of Glasgow Singapore
229 views

7:06
Encryption vs Hashing vs Encoding vs Obfuscation | Explained | Data Security | Ethical Hacking
Nerimurai Kondhar
374 views

55:39
Episode 3 | Fundamentals of Cryptography: Hashing, Encryption & Quantum Threats | BCIS 4345
Joseph H.Schuessler
43 views

7:39
Encryption vs Hashing | Explained by Cyber security Professional
AVCyberActive
663 views

55:20
Kriposna Love in Chains S04E01
Ant Grkh
1.2K views