Search Results for "and Protection of Information"
Find videos related to your search query. Browse through our collection of videos matching "and Protection of Information". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "and Protection of Information"
50 results found

0:08
Read Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Bbuhler
0 views

0:07
Download Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Maisi Baker
3 views
![[Read PDF] Information Assurance: Security in the Information Environment (Computer Communications](/image/s1.dmcdn.net/v/H0ZzQ1e0SUQ22BTpJ/x720)
0:24
[Read PDF] Information Assurance: Security in the Information Environment (Computer Communications
Dawoodbertrad
4 views
![[PDF] Electronic Healthcare Information Security (Advances in Information Security) Popular](/image/s2.dmcdn.net/v/Hg3Wn1e9-WYLu6Q99/xx720.pagespeed.ic.02DI6pcnBZ.jpg)
0:27
[PDF] Electronic Healthcare Information Security (Advances in Information Security) Popular
Biel Payton
1 views
![[FREE] Legal Issues In Information Security (Jones Bartlett Learning Information Systems](/image/s1.dmcdn.net/v/RJ8wz1epHT6d0flFG/x720)
0:34
[FREE] Legal Issues In Information Security (Jones Bartlett Learning Information Systems
lamajshamar
1 views

10:01
BASIC CAR INFORMATION - CAR KI BASIC JANKARI IN HINDI - CAR BASIC CONTROLS INFORMATION #nowplaying
whitemountaindrive
22 views

3:56
What is NIOS Board Full Information in Hindi | NIOS Board Kya Hai | By The Big Information
The Big Information
1 views

0:53
Computer Security: Personal Information & Passwords : Is it safe to send personal information in an email?
VideojugTechnologyandCars
1 views

0:46
Fastest Music & Technology Information Online. Latest Music Technology Information
seomustech
14 views

11:50
Mastering Data Protection: Symmetric, Asymmetric and Homomorphic Encryption, Hash and Key Management
RCTECH - Cloud Data Management
53 views

0:06
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Zotikishvili
0 views

0:07
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Chikovani 1981
0 views

0:08
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Buxbaum
0 views

0:20
Read Communications and Multimedia Security. Advanced Techniques for Network and Data Protection:
Elaina Coffey
0 views
6:47
Data Protection and Backup - Realcomm and RestorePoint
jimyoung_realcomm
13 views

49:48
Key Management and Protection: Evaluation of Hardware, Tokens, TEEs and MPC
RSA Conference
946 views

3:25
Incentivizing the Protection and Restoration of Forests and Ecosystems
TIME
2.5K views

0:56
#Shorts: What Is A Computer Encryption And How Does It Work? | Understanding Data Protection
COMPUTER LITERACY VIDEOS
85 views

5:00
Hybrid Data Protection Method CombiningHomomorphic Encryption and Steganography
Kyrylo Smetanin
6 views
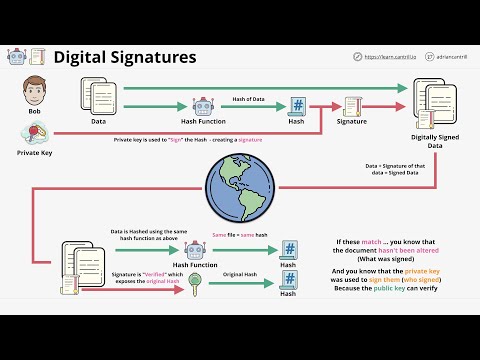
9:27
Digital Signatures - Data authenticity and integrity protection
LearnCantrill
20.2K views

32:57
Data Protection 101💀 Understanding Symmetric Encryption and DES working🤫
The Builders
20 views

32:34
Psalm 23 and Psalm 91 | The Most Powerful Prayers for Divine Protection!.mov
My Dear Sir
470 views

3:13
Brute-Force Attack on MAC - Cryptographic Hash and Integrity Protection
Ho Quang Ninh
727 views
22:51
Cryptography and Data Protection
Marmelo Abante Official
10 views

0:14
Double the Protection: Hamsa Hand and Evil Eye Necklace
Elm Studio
530 views

0:42
Why the F5 Distributed Cloud Web Application and API Protection Firewall is Important?
NGINX
1.1K views
11:30
Cryptography as a Security Tool-Operating Systems-20A05402T-UNIT – 5 Protection and System Security
D Sumathi
13.0K views

15:08
Enhance EFS file system protection with TLS and IAM
cloudonaut
1.1K views
3:24
Quantum Computing for Malware Detection in Indoor Robots: 95% Accuracy and Privacy Protection
Boundless Space
0 views

3:33:33
1111 Hz | Open up to the Universe and connect to its Energy | Receive Divine Love & Protection.
Healing Meditation
1.0M views

0:18
6 Types of Password Attacks and Protection Measures - now on @Heimdalcompany channel!!
Heimdal®
616 views

3:11:50
Cyber Defense and Protection Mechanism
IIPM International
81 views

9:31
The Key to Data Protection: An In-Depth Look at Encryption and Its Role in Securing Your Privacy
Cartoon Societies
34 views

0:14
🥇Cane Corso attack! Super security and protection! #СТРАЖ Dog training. GUARD. Odessa. Ukraine.
Dog Breeds Shorts
44.0M views

2:56
Bullet Proof And Bomb Proof Car Protection By Alif International
Alif International
332 views

0:50
JEW JEWLY Eruner Hamsa Necklace, Hamsa and Infinity Necklace, Hand Pendant, Protection Necklace Review
Reikowhu
10 views

4:10
Computer Science Basics: Firewall Usage / Computer Security and Protection
Pushyroasted
3 views

0:08
Download Problems of Protection: The UNHCR Refugees and Human Rights PDF Free
Azadiamira
1 views

0:06
Read Multimedia Security:: Steganography and Digital Watermarking Techniques for Protection
Akhujadze
0 views

0:08
Read Data Protection and Security for Personal Computers: A Manager's Guide to improving the
Ledeboer
0 views

0:27
Read Data Mining IX : Data Mining, Protection, Detection and other Security Technologies (Wit
Sophia Tran
0 views

0:25
Read Multimedia Security:: Steganography and Digital Watermarking Techniques for Protection of
Katie Whitehead
0 views

5:03
Checking the health of Security Network Protection and Security Network IPS sensors
Al Quran
6 views

0:56
Caring For Your Car Paint Protection Applications Brands And Products
MarkPrigno
0 views

0:56
Auto Paint Protection Films Brands And Products
Donald Brockman
2 views

6:27
This Defender Uses Cover And Concealment Effectively | Active Self Protection
Popular Videos en
6 views

2:25
Electronic Security System | Fogging Security System | Bank And Locker Protection
Xsort Technologies LLP
13 views

0:40
Full version Securing Digital Video: Techniques for Drm and Content Protection Complete
dm_170d419b8b4cccdb8d615d10d07882c3
1 views

1:31
Italy Bans OpenAI's ChatGPT and Launches Data Protection Investigation
Wibbitz Top Stories
8 views
![[Free Pro License] IObit Malware Fighter 11 Pro: The Best and Most Complete Protection for PC](/image/s2.dmcdn.net/v/W7LBg1eoDYnPUjHWi/x720)
2:51
[Free Pro License] IObit Malware Fighter 11 Pro: The Best and Most Complete Protection for PC
Software and Giveaway
3.3K views