Search Results for "ai-powered attacks"
Find videos related to your search query. Browse through our collection of videos matching "ai-powered attacks". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ai-powered attacks"
53 results found

6:20
Animal attacks - Best cheetah attacks - fastest predator
Hadeer cA TV
3 views

14:51
Attacks and animal fights! Attacks of lions, leopards, cheetahs and hyenas in the wild
Animal Kingdom Page
3 views

2:16
Panic Attacks and Anxiety Attacks
curepanicattacksinfo
2 views

1:31
Stop panic attacks & anxieties; panic attacks symptoms and help
stockm74
12 views

1:48
Stop Panic Attacks | Stop Anxiety Attacks
thepanicstopper
215 views

4:01
Cryptographic Attacks Explained | Common Attacks & How They Work
Cyberconnect
454 views

18:03
02-Types of Attacks in Network Security | Active vs Passive Attacks | Cryptography &Network Security
Sundeep Saradhi Kanthety
406.7K views

15:27
prevention of phishing attacks in voting system using visual cryptography
Krishna
197 views

13:29
Man in the Middle Attacks & Superfish - Computerphile
Computerphile
1.1M views

1:00
Day 18: Password Attacks with Hydra
IYS
9.2K views
6:04
Kerckhoff Principle | Cryptanalysis and its Attacks | Symmetric Key Cipher | Telugu
SHARAN KUMAR VADDADI
749 views

0:59
Understanding DOS and DDOS Attacks: A Hacker's Perspective
NewVersionHacker | New Version Hacker
14.0K views

0:11
Naagin 6 episode 76 mayuri attacks pratha #naagin6 #tejaswiprakash #shorts #youtubeshorts #trending
NAGAKANNI TV
1.5M views
6:19
What do we know about the 'Scattered Spider' cyber attacks? | ABC NEWS
ABC News (Australia)
20.0K views

3:59
Security Attacks |Cryptography |Network Security
Last Night Study
431 views

7:16
Password Attacks - CompTIA Security+ SY0-701 - 2.4
Professor Messer
107.0K views
11:10
COURSERA:INTRO. CYBER SECURITY TOOLS&ATTACKS | WEEK 3 : INCIDENT RESPONSE,FRAME WORKS |QUIZ ANSWERS
Anand Ranjit Kumar Mukkala
2.7K views

38:00
New Slide Attacks on Almost Self-Similar Ciphers
IACR
572 views

0:31
WHEN CULTIST ATTACKS💀🔥 99Nights InThe Forest🌙 Animation #blockblast #99nightintheforest #99nights
Sarahlyn Arts
276.0K views

11:19
How to Avoid Password Attacks
Kirkham IronTech
61 views

32:54
Why are big UK cyber attacks on the rise? | BBC Newscast
BBC News
25.0K views

54:29
Charalampos Papamanthou: Leakage Abuse Attacks in Encrypted Databases
CMU Cylab Crypto Seminar
191 views

0:59
Top 3 Biggest Cyber Attacks In History | Cyber Security | Intellipaat
Intellipaat
10.6K views
1:16:17
Symmetric Key Encryption and Brute Force Attacks (ITS335, L03, Y15)
Steven Gordon
2.7K views

51:33
Tales from the Crypt(analysis): A survey of side-channel attacks
UTD CSG
46 views

3:09
Megalodon attacks boat south africa
Ali H. Abbas
7.1M views
29:03
Critical Infrastructure Network Attacks: Code Red, Alert Network Operators
RSA Conference
551 views
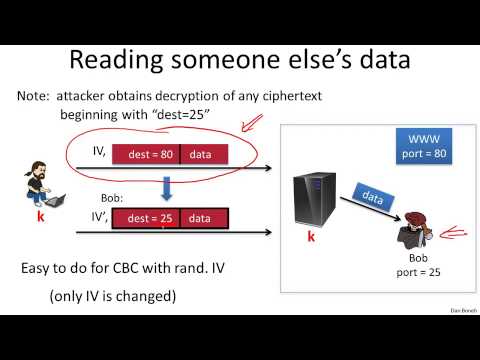
12:54
7 1 Active attacks on CPA secure encryption 13 min
Jake Danniel
305 views

3:32
Wireless Replay Attacks - CompTIA Security+ SY0-501 - 1.2
Professor Messer
148.3K views

6:05
What is Cryptography? Introduction and Types of Attacks
Algorithm Pod
361 views

7:24
Password Attacks: Social Engineering, Brute Force, Rainbow table
Cyberconnect
163 views
17:52
🚨 BREAKING NEWS: US Senators WARN of ATTACKS on the Homeland - Prepare NOW
Patrick Humphrey
21.7K views
14:51
Cryptanalysis and its types of attacks, II M.Sc(CS),R.A.College For Women, Tiruvarur
Razool Begum
53 views
2:43
Lebanon’s Aoun calls for end to Israeli attacks in meeting with US envoy
Al Jazeera English
44.7K views

2:47
UK sanctions Russian spies accused of assassination attempts, cyber attacks and sabotage | BBC News
BBC News
109.5K views

8:37
CSS #9 Cryptanalytic attacks|Ciphertext only|Known Plaintext|Chosen Plaintext|Chosen Ciphertext|BTB
Be The Best
3.1K views

1:17:41
session-8: Cryptographic Attacks on Privacy
IACR
918 views

2:16:56
Craziest Lion Attacks Ever Caught On Camera #NatureDocumentary | Wild Animals
The Majestic - Animal Documentary
3.4K views

8:01
Multimedia - Cryptography - Product Ciphers - DES - Attacks - Arabic - Video 10
Alaa Abdelmohsen
141 views

0:15
Types of cyber attacks
AthulRaj
2.7K views
44:46
ACM Cyber | Cryptographic Attacks
ACM at UCLA
73 views

4:48
Aquaman and the Lost Kingdom (2023) - Black Manta Attacks Atlantis | Movieclips
Movieclips
268.9K views
2:14
Cryptanalysis | cryptanalysis in network security in hindi | cryptanalysis attacks | #mscoder
ms coder
7.0K views

6:34
Ukraine recording hundreds of cyber-attacks on critical infrastructure daily
Sky News Australia
1.0K views
19:46
The Curse of Small Domains New Attacks on Format Preserving Encryption
IACR
370 views

3:46
An assessment of cryptographic protocols susceptible to quantum attacks
Aliro
63 views

1:22:16
16. Side-Channel Attacks
MIT OpenCourseWare
48.1K views

2:08
Japan deploys troops to northern mountains to tackle wave of deadly bear attacks
Al Jazeera English
124.4K views

2:11
Types of Password Attacks
Keeper Security
180 views

3:23
CISSP -60 Security Architecture and Engineering: Understand methods of cryptanalytic attacks
sumon infosec
128 views

1:00
Watch: AI-powered robot teaches German students
euronews (in English)
1.5K views

1:10
Reeves shown first AI-powered strike drone
ODN
581 views

9:34
What's next for AI-powered humanoid robots?
The Manila Times
225 views