Search Results for "adaptively chosen ciphertext attack"
Find videos related to your search query. Browse through our collection of videos matching "adaptively chosen ciphertext attack". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "adaptively chosen ciphertext attack"
50 results found

8:10
Chosen Cipher Attack on RSA
Bill Buchanan OBE
18.4K views

2:06
Chosen Plaintext Attack - ESET CHannel
ESET Channel
174 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views

0:54
Day 24: Cryptography Basics 🔐 | Plaintext, Ciphertext, Symmetric vs Asymmetric Key| #100daychallenge
Encrypticle
82 views

7:06
Ciphertext
Wikivoicemedia
283 views
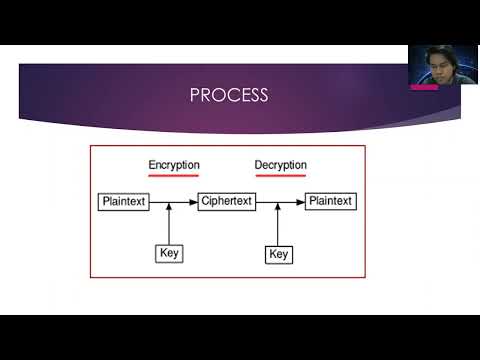
3:39
Ciphertext-Only Method ( Earphone Very Recommended )
Eizlan Yusof
45 views

3:13
Ciphertext Only Method
MUHAMMAD IKMAL
44 views

23:43
Fully Homomorphic Encryption with Relatively Small Key and Ciphertext Sizes.
IACR
1.4K views

1:00
क्या होता है #ciphertext?? What is #Cryptography?? Kumar S Bhaweshnu
civil academy
2.3K views

3:19
Ciphertext-only attacks on randomly permuted many-time-pad (3 SOLUTIONS!!)
Nida Karagoz
10 views

1:03
What is the difference between ciphertext and plaintext (or cleartext)?
What is cybersecurity?
448 views

6:18
Introduction to Cryptography | Plaintext vs Ciphertext | Information Security | Urdu/Hindi
Fawad Speaks
96 views
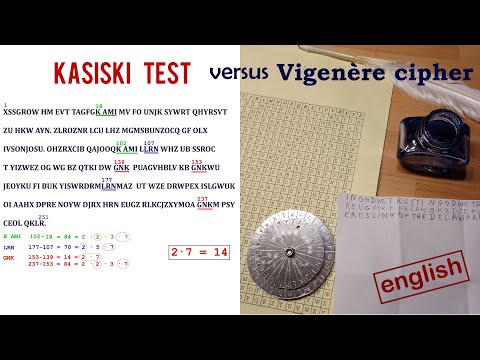
8:47
Cryptanalysis: Breaking a Vigenère ciphertext with Kasiski's test
Jens Puhle
4.1K views
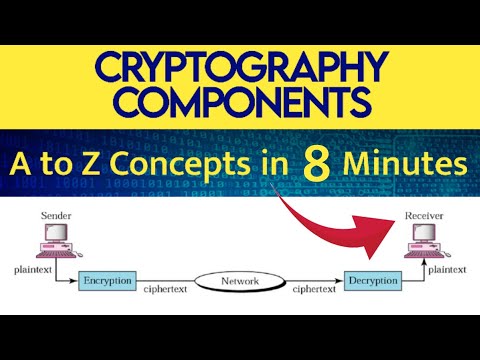
8:34
Cryptography Components & Network Security Model | Plaintext | Ciphertext | Encryption | Decryption
Pinnacle !! Bhagyashri Thorat
148 views

0:14
Cipher Text Web Application #ciphertext #encryption #crypto
Jonathan Gillman
129 views

11:01
ITJCC06 - PKE-MET: Public-Key Encryption with Multi-Ciphertext Equality Test in Cloud Computing
Spiro Prime Tech Services
191 views

25:17
Anne Canteaut | Stream ciphers. A Practical Solution for Efficient Homomorphic Ciphertext Compressio
Horst Goertz Institute for IT Security
259 views

0:32
Cryptography, Cryptanalysis, Cryptology, Cleartext, Ciphertext
Professor Wolf
7.0K views
0:19
Ciphertext Only
Quick Cybersecurity Study
71 views

1:00
Cryptanalysis: Breaking a ciphertext with Kasiski's test
Jens Puhle
776 views
14:16
Information Security | Vigenere Cipher | cryptanalysis | How we find Key length From Ciphertext
NextGen Learners
50 views

3:39
Basic Cryptography Explained | Plaintext & Ciphertext | Cyber Security for Beginners
SAURAV EDUCATION
6 views

0:44
Circuit Ciphertext-policy Attribute-based Hybrid Encryption with Verifiable Delegation in Cloud
career explorer
47 views

0:28
How to Pronounce Ciphertext
Pronunciation Guide
6.9K views

0:17
What is the difference between a ciphertext and plaintext?
Intelligence Gateway
1.6K views

4:18
Decrypting Ciphertext with the Vigenère Cipher: Step-by-Step Tutorial"
PHY, CHM, MATHS & COMP MUHAMMAD HAMZA BIN ATTA
7 views

0:16
Unlocking the Secrets: Understanding Ciphertext in Cryptography #short #shortvideo #shorts
Aarnaaology
36 views
5:17
What is a plaintext? What is a ciphertext?
internet-class
29.3K views
15:22
Cryptography in Excel | Ciphertext & Plaintext Calculator | How to use | Free download
Pink Moon
374 views

0:58
Yaytsogram cipher code November 8 #Yaytsogram #yaytsogramcipher #ciphercodes #ciphertext #airdrop
Digital Assets
36 views
2:01
Ciphertext Plaintext Blowfish | WhatsApp End-to-End Encryption | MCQ Explained
Schrödingervert
85 views

13:05
Circuit Ciphertext policy Attribute based Hybrid Encryption with Verifiable Delegation in Cloud Comp
Cloud Technologies
570 views

3:12
Encryption : plaintext to ciphertext , frequency analysis , substitution cipher , Computer science
Ans Tutor
46 views

4:06
Circuit Ciphertext-policy Attribute-based Hybrid Encryption with Verifiable Delegation
MICANS IEEE PROJECTS 2015 PPT VIDEOS
990 views

16:16
Ciphertext-Policy Attribute-Based Encryption
Bill Buchanan OBE
12.4K views

8:36
Was sind Angriffsszenarien Ciphertext und Knownplaintext?
Mike Majewski
826 views

1:01
The Mysterious Ciphertext
HOTWIRE
760 views

16:29
Birthday Attack in Cryptography | Part 2 | How to attack a Person | Explained In Hindi | AR Network
A.R Network
803 views

0:25
Brute Force attack || How to password Crack || Brute force attack prank || Brute force stimulator
Renu Computer Tricks
23.5K views

5:28
Dictionary Attack and Brute Force Attack: hacking passwords
Sunny Classroom
97.5K views

2:16
'Attack on Afghan soil': After condemning Kabul attack, Taliban now slam U.S for targeting ISIS-K
Hindustan Times
25.5K views

0:49
KP Police close to terrorist network involved in attack #kp #police #attack (1)
ULTRA NEWS
117 views

6:26
Active Attack in network security | Types of security attack in cryptography | What is cryptanalysis
Chirag Bhalodia
17.2K views

5:58
Cyber Security L-13 | cryptanalysis attacks| cipher text attack |plain text attack| choosen text
Btech_cse _notes_bank
2.8K views

6:17
Active Attack Vs Passive Attack ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
164.4K views

14:08
Low Exponent Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
11.4K views

4:58
Passive Attack in network security | Types of security attack in cryptography | Cryptanalysis
Chirag Bhalodia
27.5K views

14:37
Cryptography Part 4: Cryptanalysis, Attack Surfaces, Attack Trees
Tech Lover
2.3K views

2:47
“Learn how pro’s train to convert defence to attack and get back to defence from Attack positions “
Simply Sport Badminton Excellence Program
520 views

8:58
Denial of Service Attack ( DoS Attack ) 🔥🔥
Perfect Computer Engineer
148.1K views