Search Results for "Systèmes d'information"
Find videos related to your search query. Browse through our collection of videos matching "Systèmes d'information". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Systèmes d'information"
50 results found
![[Read PDF] Information Assurance: Security in the Information Environment (Computer Communications](/image/s1.dmcdn.net/v/H0ZzQ1e0SUQ22BTpJ/xx720.pagespeed.ic.gf-aEABY4p.jpg)
0:24
[Read PDF] Information Assurance: Security in the Information Environment (Computer Communications
Dawoodbertrad
4 views
![[PDF] Electronic Healthcare Information Security (Advances in Information Security) Popular](/image/s2.dmcdn.net/v/Hg3Wn1e9-WYLu6Q99/xx720.pagespeed.ic.02DI6pcnBZ.jpg)
0:27
[PDF] Electronic Healthcare Information Security (Advances in Information Security) Popular
Biel Payton
1 views
![[FREE] Legal Issues In Information Security (Jones Bartlett Learning Information Systems](/image/s1.dmcdn.net/v/RJ8wz1epHT6d0flFG/xx720.pagespeed.ic.zppxVAjH3E.jpg)
0:34
[FREE] Legal Issues In Information Security (Jones Bartlett Learning Information Systems
lamajshamar
1 views

10:01
BASIC CAR INFORMATION - CAR KI BASIC JANKARI IN HINDI - CAR BASIC CONTROLS INFORMATION #nowplaying
whitemountaindrive
22 views

3:56
What is NIOS Board Full Information in Hindi | NIOS Board Kya Hai | By The Big Information
The Big Information
1 views

0:53
Computer Security: Personal Information & Passwords : Is it safe to send personal information in an email?
VideojugTechnologyandCars
1 views

0:46
Fastest Music & Technology Information Online. Latest Music Technology Information
seomustech
14 views

6:14
Difference between Hash and MAC in Information Security | Comparison | Information Security Lectures
Easy Engineering Classes
10.7K views

0:37
Phishing | Types of security threats to Information System
Knowledge Valley
318 views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

10:22
Confusion And Diffusion In Cryptography |Confusion And Diffusion Example|Information Security | AKU
Er. Rashmi sinha
557 views

59:50
Russian Information Warfare: A Conversation with Dr. Bilyana Lilly
Carnegie Endowment
1.9K views

4:50
What is Business Information Technology? (Quick Guide)
IT Brezel
51.9K views

0:08
What is the Full Form Of BCA? | What is BCA? | Full Information About BCA
Helmety YouTuber
204.7K views

0:29
ECB - Electronic code book (encryption) | information security #studyshorts #studyeasierbypoojapatel
Pooja Patel
360 views

7:08
Why Information Technology is THE BEST career (In 2025)
BigBroTECH
2.1K views

10:57
How to Get Started with I.T. - Information Technology
IT Career Questions
416.9K views

0:46
Asymmetric key cryptography क्या है || Useful Information 🔥 #technology #techvideo #networksecurity
VL Facts
1.4K views

1:16:27
Information Security—Before & After Public-Key Cryptography
Computer History Museum
112.2K views

24:54
Proceedings Podcast: Dr. Bilyana Lilly on Russia's Information Warfare Campaign
U.S. Naval Institute
2.4K views

4:33
DMZ Network Zone | Information Security Management Fundamentals Course
Instructor Alton
949 views

5:11
IT Fundamentals | Quick IT Basics | Understanding IT | Information Technology
Of The Internet Things
4.2K views

11:11
#17 Block Cipher Introduction & Design Principles Of Block Cipher |Information Security|
Trouble- Free
129.6K views

0:21
What is Information Technology
3Scode
899 views

0:31
Unlocking the Secrets of Cryptography: How Algorithms Keep Your Information Safe
BillionaireMotivation
41 views

1:58
Justin Holmgren, Research Scientist, Cryptography & Information Security Lab
NTT Research
134 views

5:16
Fighting an Information War, Israel Hosts Christian Media Summit
CBN News
6.9K views

11:47
Information Security: Context and Introduction || Coursera || The Complete Solution
saisoluz
2.3K views

1:41
Cybersecurity Shorts for Executives: The New Chief Information Security Officer
George Mason University Television
210 views

0:47
Saif ko bahar se information mil rahi hai? 😱 - #OvaisRiaz | #AyazSamoo | #ARYPodcast
ARY Podcast
136.1K views

10:21
Caesar Cipher Encryption and Decryption in Hindi | Information Security
Hamza Learning
987 views

0:59
Who was Charles Babbage? Interesting information
Misha.Prayu. Show
304 views

16:06
Substitution Techniques | Caesar Cipher | Monoalphabetic Cipher | Part 1 | Information Security
eVeda
79 views

1:10:02
Single Systems | Understanding Quantum Information & Computation | Lesson 01
Qiskit
271.7K views

1:00:52
Quantum Circuits | Understanding Quantum Information & Computation | Lesson 03
Qiskit
77.5K views
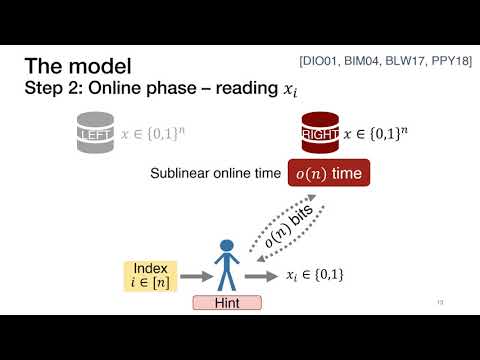
21:18
Private Information Retrieval with Sublinear Online Time
IACR
2.0K views

0:45
Symmetric and Asymmetric Cryptography|CC-413|Information Security|@PU-shift-swift
PU-Shift-Swift
6 views

4:46
Asymmetric Information, Adverse Selection & Moral Hazard | Economics Explained
INOMICS
117.2K views

4:31
Steganography of Binary Information in Image Using Deep Learning Method
IBIMA Media
80 views

8:51
Hill Cipher Decryption in 5 steps Example in hindi | Information and Network Security Course | GTU
AXL huB
200 views
![What is Python With Full Information? – [Hindi] – Quick Support](/image/i.ytimg.com/vi/3dy_PYF9xOI/hqdefault.jpg)
8:56
What is Python With Full Information? – [Hindi] – Quick Support
Quick Support
2.1M views

8:54
Comparison of the Use of M-Bit LSB Steganography Methods on MAV Files in Information Storage
imelda duma
20 views

3:28
Charles Babbage || Father of Computer || Information || P S Computer
P S Computer Center
6.6K views

18:38
Information and Network Security , Module 1, Introduction
GNS S
173 views

6:37
Quantum information and quantum cryptography
Science Technology And Engineering
4 views
2:12
Android Based Image Steganography System | Information Security Projects Ideas
Nevon Projects
7.6K views

2:16:24
Information Security Oversight Office Training Seminar
US National Archives
617 views

0:33
Image Hide text file information#education#informationsecurity #img#hacker#hack#command#datasecurity
Cyber Neta IT
33 views

0:21
Reality of Scholarship in Italy.Watch full video get the information #internationalstudents #italy
Indian in Europe
219.6K views

0:38
Binwalk Image forensic extract information from image #cybersecurity #imageforensic #binwalk #exif
Zodiac
8.1K views