Search Results for "Security Protocols"
Find videos related to your search query. Browse through our collection of videos matching "Security Protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Security Protocols"
50 results found

3:17
How Do Network Security Protocols Like HTTPS Protect Your Data? - Talking Tech Trends
TalkingTechTrends
1 views

16:47
Security Protocols 02 : Asymmetric and Symmetric Key Pairs
Shan Zhang
10 views
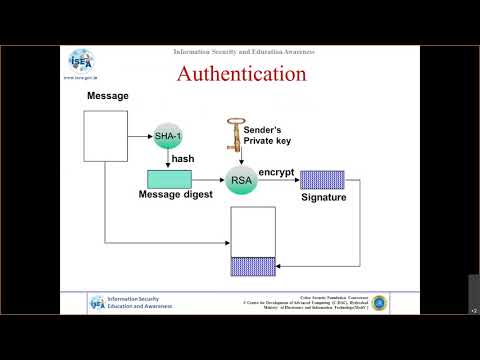
12:26
Cryptography and Network Security Protocols - Part 10
Information Security Awareness
48 views

3:14
Security and Composition of Rational Cryptographic Protocols
IACR
207 views

3:08
SSL and TLS Explained: Secure Communication Protocols for Web Security
CodeLucky
5 views

15:26
Security Protocols: Lecture 2e (Cryptographic Hash Functions & Communication Integrity)
Antonis M
322 views

21:02
The Price of Active Security in Cryptographic Protocols
IACR
346 views

1:23:30
Proving the security of real-world cryptography and protocols by Jonathan Protzenko
CS Research Week
68 views
3:05
How Do Cryptographic Protocols Like RSA Secure Network Security? - Talking Tech Trends
TalkingTechTrends
1 views

0:16
What is Port 49? #cybersecurity #ports #protocols #security #networking #learnnetworking #learn
Sean Talks Cybersecurity
247 views

0:05
Read Cryptography: Protocols Design and Applications (Cryptography Steganography and Data Security)
Epataraia
0 views

0:06
Read Security Protocols Ebook Free
Sgarcha
0 views
![[PDF] Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security](/image/s1.dmcdn.net/v/FVODb1e98sGL1pB3Q/xx720.pagespeed.ic.r2Q32Sqpki.jpg)
0:05
[PDF] Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security
OceaNewton
3 views

0:05
Download Protocols and Procedures of Cryptography and Network Security PDF Free
Ehrenfeld
1 views

0:06
Read Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security
Bgerstner
0 views

0:08
Read Bundle: Network Defense: Fundamentals and Protocols + Network Defense: Security Policy
Sbjorn
0 views

2:27
Updated security protocols announced for international flights
Daily News
0 views

12:53
Narendra Modi's security enhanced with special protocols
Inkhabar
0 views

2:04
STRICT SECURITY PROTOCOLS FOR ERLA
CCNTV6
624 views

13:26
Essential Guide to Network Security and Wireless Protocols | Insights from a Cybersecurity Expert
Skillfloor
6 views

10:16
Cryptography and Network Security Protocols - Part 8
Information Security Awareness
25 views
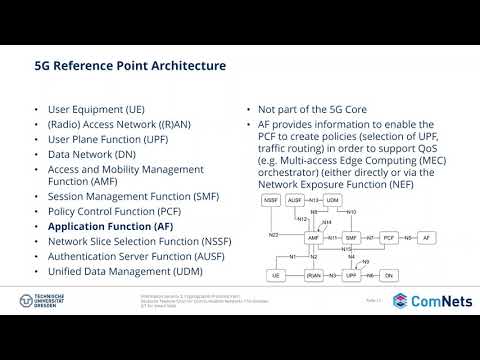
28:46
L13 - 01 - Information Security 2 - Cryptographic Protocols Part 1
ComNets Lectures
127 views

0:41
Crypto Security Protocols for Investors
Crypto Compass
2 views

1:02:29
Security of Quantum Key Distribution Protocols – Ph.D. Thesis Seminar by Rotem Liss
Rotem Liss
66 views

3:30
Wireless Cryptographic Protocols - CompTIA Security+ SY0-501 - 6.3
Professor Messer
68.6K views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

44:58
Computer Security | What Is Computer Security | Cyber Security Tutorial | Simplilearn
Simplilearn
95.6K views

12:04
Approaches of web security in urdu hindi | approaches of web security lecture | web security | p 49
IT Expert Rai Jazib
1.3K views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

44:53
Networks Security | Security Services | Security Goals | Cryptography | Steganography | Attacks | IA
Bhavishya Coaching SGNR
929 views

3:44
Cyber security क्या है? | What is Cyber Security in Hindi? | Why Cyber Security is Important?
Deepak TechTimes
59.8K views

9:13
What is Security and security attacks, security services in CNS
Lab Mug
13.4K views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

5:10:06
Cloud Security Full Course | Cloud Security Fundamentals | Cloud Security Training | Intellipaat
Intellipaat
80.6K views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

13:10
Types of security policies, www policy, email security policy, cyber security lecture series
Gaurav Khatri
9.3K views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

10:19
#2 Security Approaches and Principles or Goals of Security- Cryptography |Information Security|
Trouble- Free
99.1K views

6:06
Need for Security | Network Security | Cryptography and Network Security
Bikki Mahato
405 views

6:31
Network Security vs Cyber Security | What is Security? | Explained in Hindi
Tech Guru Manjit
16.0K views

3:57
Security Mechanisms | Network Security | Cryptography and Network Security
Bikki Mahato
184 views

7:31:09
Cloud Security Course | Cloud Security Training | Cloud Security Tutorial | Intellipaat
Intellipaat
16.2K views