Search Results for "Secure A P Is"
Find videos related to your search query. Browse through our collection of videos matching "Secure A P Is". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure A P Is"
50 results found

3:22
How to Secure App-Level Encryption Keys with Unbound Key Control (UKC) via REST API
Unbound Security
564 views

7:49
Hybrid Algorithm for secure data over Cloud OS
Avin Pasupuleti
1.4K views

9:49
HAR 2009: How to use quantum cryptography for secure identification 4/6
Christiaan008
151 views

0:15
HOW ! ASUS LAPTOP BOOT MENU BIOS SETTINGS ! SECURE BOOT ! BOOT FROM USB ! DVD ROOM
Vcarelaptops
496.1K views

14:15
Entity Encryption using AES | Spring Boot | JPA | Advanced Encryption Standard | Secure your data
VKS Tech
10.7K views

17:28
10 Principles for Secure by Design: Baking Security into Your Systems
IBM Technology
42.9K views

8:32
Secure Electronic Transaction (SET) in hindi || SET Protocol || Network Security || Akant 360
Unbeaten Learning
63.5K views
![[8B] Forward and Backward-Secure Range-Searchable Symmetric Encryption](/image/i.ytimg.com/vi/3Ri_VXm9SJM/hqdefault.jpg)
12:00
[8B] Forward and Backward-Secure Range-Searchable Symmetric Encryption
Privacy Enhancing Technologies Symposium
244 views

1:04
Java Secure Coding: Data Confidentiality and Integrity 12 2 Asymmetric Crypto
AppSec Labs
823 views

13:45
Secure Binary Image Steganography Using F5 algorithm Based on Data Hiding and Diffusion techniques
Jitendra Singh
954 views
1:09
What is Quantum Secure Communication? All You Need to Know
NewsX Live
276 views

1:02
Unpacking Quantum Cryptography: Will It Secure Our Digital World?
AI BreakDown
1 views

20:10
Saber on ARM: CCA secure module lattice based key encapsulation on ARM
IACR
327 views

8:02
Yubico's Post-Quantum Cryptography Revolution: Secure Digital Identity Beyond Passkeys
Creative Space
4 views
1:00
5 QUANTUM SECURE CRYPTOCURRENCIES
Crypto Mason 2
13.2K views

1:08:14
Cryptography: From Mathematical Magic to Secure Communication
Simons Institute for the Theory of Computing
36.1K views

4:50
Compact and Tightly Selective-Opening Secure Public-key Encryption Schemes
IACR
66 views
18:00
Digital privacy: The 2025 guide to secure messaging & WhatsApp alternatives
The Urban Herald
22 views

5:58
Module 4.9. Distribution of Secret Keys Using Public-Key Cryptography|S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
2.6K views
10:47
Hash function | S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
3.1K views

0:45
Quantum Computing & Post-Quantum Cryptography Explained | Future of Secure Tech 2025
Rise Academy Career Connect
54 views

8:46
Quantum-Safe Crypto-Agility: Secure Your Enterprise Future
IBM Technology
4.2K views

4:52
Secure File Storage On Cloud Using Hybrid Cryptography (part 1)
Awais Akbar
2.8K views

6:28
LDAP and Secure LDAP - CompTIA Security+ SY0-401: 5.1
Professor Messer
95.6K views

3:36
Module 4.3 Requirements of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.4K views

52:18
Quantum secure communication
Fysikum Stockholm University
777 views

2:55
Will Quantum Computing Secure Our Digital Archives? - CountyOffice.org
County Office Law
1 views

1:12
"Cryptography 101: The Secrets Behind Secure Transactions"
theblueprint
40 views

0:51
Quantum Cryptography: The Future of Secure Communication #shorts #science #technology #tech
A3TR
81 views

33:11
CNS UNIT - 4|Secure Socket Layer,Transport Layer Security,HTTPS,SSH, IEEE 802.11 i | JNTUH #r18 #r22
One Day Batting
8.5K views

0:55
Secure Crypto With Hardware Wallet | SafePal S1 | #shorts #crypto
Market Nama
20.4K views

15:55
DOE CSGF 2022: Communication-Efficient Secure Two-Party Computation From Minimal Assumptions
Krell Institute
27 views

3:01
OTP - Secure Communication
Neetha Merin
167 views

21:09
DT107B: Secure, Real-Time Watermark Detection for Effective Privacy Monitoring
Streaming Media
152 views

1:00
Quantum cryptography for secure communication
Fact Filled Shorts
6 views

6:11
Understanding RSA Algorithm: The Key to Secure Communication
securityconceptsnotes
55 views
5:31
Secure Cloud Data Using Hybrid Cryptography Using Python
Myra Projects
60 views

0:09
🔒 SSL (Secure Sockets Layer) 🌐 | Data Encryption, Cybersecurity & Safe Web Browsing
Smart Digital Pakistan
138 views
26:05
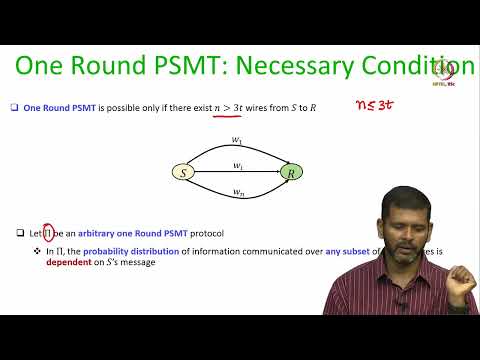
Lec 20 Perfectly-Secure Message Transmission
NPTEL - Indian Institute of Science, Bengaluru
528 views
5:00
A More Secure Steganography Method in Spatial Domain -PASS 2011 IEEE Projects
pass pandian
320 views

0:46
What is Steganography | Secure your data #ethicalhacking #hindi #cybersecurity #hindishorts
Cyberverse Academy
4.9K views

3:36
What Cryptographic Principles Secure Internet VPN Tunnels? - Internet Infrastructure Explained
Internet Infrastructure Explained
0 views

1:00
Unlocking the Power of BasedAl: The Future of Secure Al Networks!
💰 CG Money 247
46 views

0:44
Quantum Cryptography—The Secret to Secure Communication!
Legends & Innovations
87 views

0:15
Quantum Cryptography: Unbreakable Encryption and Secure Key Distribution 🔒🔑
Dev Job Seekers
543 views

0:52
Tools for Implementing Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent
NextGen AI Explorer
3 views

1:53
A Robust and Secure Video Steganography Method in DWT-DCT Domains | Projects
Projectsatbangalore
218 views

11:35
Module 4.1 Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434#engineering #ktutuition
bushara abdulrahim
4.5K views
11:52
Cryptography Project - Secure Message Send
Catherine E
516 views
7:35
Intelligent cryptography approach secure distributedbig data | Final Year Projects 2016 - 2017
ClickMyProject
130 views