Search Results for "Purchase Key Attack"
Find videos related to your search query. Browse through our collection of videos matching "Purchase Key Attack". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Purchase Key Attack"
50 results found

0:36
Purchase of former B&M building
National World - Other Local Sites
834 views
![AdobeAdobe Photoshop 2024 v25.1.0.120 [Pre-Activated] is for trial/educational and non-commercial use only. Using non-genuine software may cause various problems To use this software without any problems Please purchase a genuine license from the offi](/image/s2.dmcdn.net/v/VMZBQ1eoTSnCiWZzK/xx720.pagespeed.ic.fHZu5RdCkw.jpg)
0:51
AdobeAdobe Photoshop 2024 v25.1.0.120 [Pre-Activated] is for trial/educational and non-commercial use only. Using non-genuine software may cause various problems To use this software without any problems Please purchase a genuine license from the offi
IIIIIIRuS_Q
225 views

0:24
Export Sale Purchase by Party in Excel/PDF | Raseed Billing Software#billingsystem #raseedapp #short
Raseed
54 views

2:27
How to Export All Purchase invoice at once in PDF file from tally erp9
Suman Education hub
171 views

0:39
China: PH idea to purchase mid-range capability system 'provocative'
Manila Bulletin
4.5K views

16:29
DIFFIE HELLMAN KEY EXCHANGE || MAN IN THE MIDDLE ATTACK || EXAMPLE || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
46.1K views

11:35
Symmetric key and Asymmetric key cryptography explained in hindi # Asymmetric key cryptography kya h
FUTURE MENTOR
19 views

15:44
Public Key Distribution in Cryptography | Public Key Distribution | Key Distribution
Chirag Bhalodia
57.3K views

38:43
Public Key Cryptography | Asymmetric Key Cryptography | Components of Public Key Cryptography
Dr. Majid Khan Mathematics Waley
343 views

2:56
Encryption key cryptography type(symmetric key cryptography & asymmetric key cryptography) in HINDI
Shukla Classes
40 views

3:18
Difference Between Key Size, Key Length, and Key Space - CISSP
CISSPrep
2.8K views

6:43
Network & Cyber Security Lecture: Symmetric key Encryption (Private Key) Key Based Cryptography
Sanjay Pathak
1.8K views

5:34
Public-Key Certificate and Public-Key Infrastructure (PKI) - Asymmetric Cryptography and Key
Ton Ha Nhi
11 views

4:20
What is PUBLIC-KEY CRYPTOGRAPHY? WHat does PUBLIC-KEY CRYPTOGRAPHY mean? PUBLIC-KEY CRYPTOGRAPHY meaning & explanation
The Audiopedia
1 views

11:18
Symmetric Key Cryptography VS Asymmetric Key Cryptography | Private vs Public Key Cryptography
Simple Snippets
8.7K views

18:04
Symmetric Key and Public Key Encryption | Public key Encryption hindi urdu (IT430)
theITeducation.com
897 views

4:09
public key applications in urdu hindi | public key applications lecture | public key tutorial | p 41
IT Expert Rai Jazib
121 views

26:05
symmetric key distribution || urdu hindi | symmetric key distribution lecture |symmetric key |part38
IT Expert Rai Jazib
2.4K views

29:00
Asymmetric Key Encryption (Private key vs public key encryption)
iq pop
48 views

18:08
CS14: Digital Signature in Cyber Security | Symmetric Key | Asymmetric Key| Public Key Cryptography
University Academy
37.2K views

7:56
Key Distribution in Asymmetric Key |Asymmetric key distribution |Network Security Hindi explain
DK Technical Point 2.0
1.1K views

6:55
Key Distribution in Symmetric key |Symmetric key Distribution |Network security Hindi...
DK Technical Point 2.0
3.1K views

1:00
Key Management Systems, Key Box - Key Tracer
Keytracer
1 views
![Key Remapper Key Gen [key remapper windows]](/image/s1.dmcdn.net/v/8wPMm1e0Gum_TF5WY/xx720.pagespeed.ic.czhaQcEBlV.jpg)
1:35
Key Remapper Key Gen [key remapper windows]
Jeff Butler
47 views

0:06
Download Investigating Psychology: key concepts key studies key approaches PDF Free
Kiriaki Reme
9 views

1:02
Windows 7 key, office key, norton key from www.keyyeah.com
neriosamed
370 views

1:05
Windows 8 KEYGEN (activation key,serial key,key generator)
Sornililio
5 views

0:28
FIFA 14 CD Key (Key Generator for PC)Serial Key
jsar
41 views

0:28
FIFA 14 Serial Key (Key Generator for PC)CD Key
utikjholh
76 views

0:32
PES 14 Serial Key (Key Generator for PC)CD Key
ppsee2014
2 views

26:08
(1) Public Key Encryption: DH key exchange and key generation in RSA
Rands
150 views

22:19
MODULE 3- Use of key hierarchy, Key distribution scenario, Hierarchial key control.
SAVI
2.9K views
0:30
FIFA 14 Serial Key (Key Generator for PC)CD Key
jassja
18 views

16:29
Birthday Attack in Cryptography | Part 2 | How to attack a Person | Explained In Hindi | AR Network
A.R Network
803 views

0:25
Brute Force attack || How to password Crack || Brute force attack prank || Brute force stimulator
Renu Computer Tricks
23.5K views

5:28
Dictionary Attack and Brute Force Attack: hacking passwords
Sunny Classroom
97.5K views

2:16
'Attack on Afghan soil': After condemning Kabul attack, Taliban now slam U.S for targeting ISIS-K
Hindustan Times
25.5K views

0:49
KP Police close to terrorist network involved in attack #kp #police #attack (1)
ULTRA NEWS
117 views

6:26
Active Attack in network security | Types of security attack in cryptography | What is cryptanalysis
Chirag Bhalodia
17.2K views

5:58
Cyber Security L-13 | cryptanalysis attacks| cipher text attack |plain text attack| choosen text
Btech_cse _notes_bank
2.8K views

6:17
Active Attack Vs Passive Attack ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
164.4K views
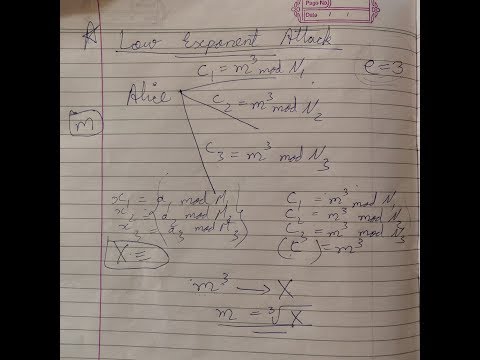
14:08
Low Exponent Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
11.4K views

4:58
Passive Attack in network security | Types of security attack in cryptography | Cryptanalysis
Chirag Bhalodia
27.5K views

1:48
Known Plaintext Attack || Chosen Plaintext Attack
Pritesh Prajapati
34.8K views

14:37
Cryptography Part 4: Cryptanalysis, Attack Surfaces, Attack Trees
Tech Lover
2.3K views

2:47
“Learn how pro’s train to convert defence to attack and get back to defence from Attack positions “
Simply Sport Badminton Excellence Program
520 views

8:58
Denial of Service Attack ( DoS Attack ) 🔥🔥
Perfect Computer Engineer
148.1K views

0:17
he attack😱 on old women 😨 #kdrama #shorts #attack #netflix #feed
Kdrama shorts
209 views

8:10
Security Attacks : Active and Passive Attack ll Passive Attack Types Explained in Hindi
5 Minutes Engineering
504.3K views

12:16
Common Modulus Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
14.1K views