Search Results for "PKIX protocols"
Find videos related to your search query. Browse through our collection of videos matching "PKIX protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "PKIX protocols"
50 results found
1:11:02
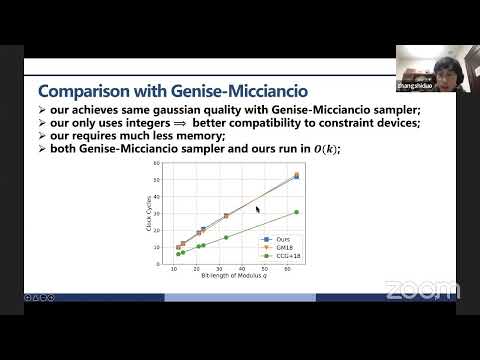
session-14: Cryptographic Protocols + Tools
IACR
259 views
1:09:14
s-20: Cryptographic Protocols and Secure Computation II
IACR
361 views

2:45
The Fascinating World of Cryptographic Protocols
BITCOIN HARDER
9.4K views

0:59
Encryption protocols: "Strong encryption = strong security. #VPN #onlineprivacy #techtips
norexvpn
6 views

0:50
Top Three DeFi Security Protocols Explained
CryptoSpectra
32 views

3:38
How Do QKD Protocols Like BB84 Ensure Quantum Security? - Quantum Tech Explained
Quantum Tech Explained
5 views

8:07
3 14 Applying Cryptography Cryptographic Protocols CISSP
cissp kuwait
57 views

25:09
Card-based cryptographic protocols for three-input functions using private operations
Fields Institute
139 views

0:19
Quantum Key Distribution Protocols
Sciwords
18 views

10:27
Secure Protocols - CompTIA Security+ SY0-501 - 2.6
Professor Messer
146.7K views

23:06
Master Advanced Cryptography: Digital Certificates, PKI, & Secure Protocols | Chapter 4
Joseph H.Schuessler
67 views

3:05
Protocols - Applied Cryptography
Udacity
7.0K views
17:13
Clear-text Vs Cryptographic Protocols | Network Security // Perumal Jegan
Perumal Jegan
194 views
7:32
Security Protocols: Lecture 2b (Core Idea of Cryptography and Basic Terminology)
Antonis M
354 views
9:41
Cryptographic Protocols CompTIA Security+ Study Session 21 August 2020
Cyberkraft
52 views

15:46
🌟🔒 Preparing for Quantum Threats Developing Quantum Resistant Cryptographic Protocols
Science News
10 views

28:24
Integrating post-quantum cryptography into protocols: the case of Wireguard | Kai-Chun Ning
Cryptography Summits and more
97 views

58:51
MPC-TP: Probabilistic Termination and Composability of Cryptographic Protocols - Juan A Garay
CrIS Lab IISc
127 views

16:47
Security Protocols 02 : Asymmetric and Symmetric Key Pairs
Shan Zhang
10 views

58:41
Cryptographic protocols in the era of cloud computing
All Hacking Cons
8 views
39:30
An Industry Perspective On Automated Analysis For Designing Cryptographic Protocols - Marc Ilunga
BlackAlps CyberSecurityConference
71 views

47:14
DEF CON 26 CRYPTO AND PRIVACY VILLAGE - Matt Cheung - Prototyping Cryptographic Protocols
DEFCONConference
651 views

1:38:51
PETS 2022 Moti Yung Keynote: "Privacy Integrated Computing:” Cryptographic Protocols in Practice
Privacy Enhancing Technologies Symposium
196 views

1:06:45
Colloquium: Gláucia Murta: Device-independent quantum cryptography: towards network protocols
Instituto de Física Teórica, IFT-UNESP
209 views
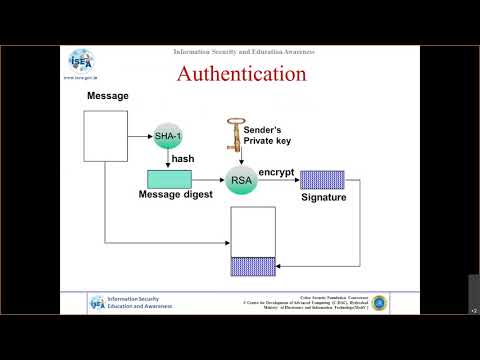
12:26
Cryptography and Network Security Protocols - Part 10
Information Security Awareness
48 views

3:14
Security and Composition of Rational Cryptographic Protocols
IACR
207 views
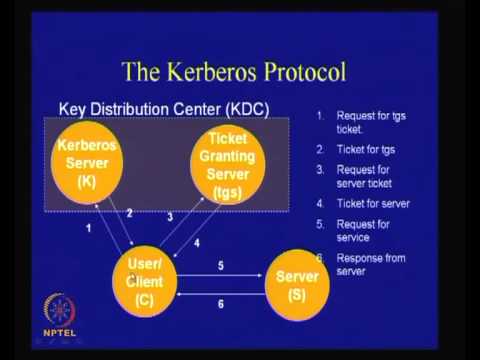
55:26
A Tutorial on Network Protocols
nptelhrd
12.3K views

15:26
Security Protocols: Lecture 2e (Cryptographic Hash Functions & Communication Integrity)
Antonis M
322 views

4:09
What Are The Types Of Cryptographic Protocols? - Tactical Warfare Experts
Tactical Warfare Experts
41 views

25:33
2019 EuroLLVM Developers’ Meeting: S. Celi “Clang tools for implementing cryptographic protocols...”
LLVM
426 views

25:09
MPC-Friendly Symmetric Cryptography from Alternating Moduli: Candidates, Protocols, and Applica...
IACR
303 views

0:23
Crypto 101 Understanding Protocols #crypto #bitcoin
The Bitcoin Bob Show
75 views
1:20:56
COSIC Course 2024: "Cryptographic protocols for entity authentication and..." (Bart Preneel, COSIC)
COSIC - Computer Security and Industrial Cryptography
239 views

4:04
How Will Quantum Cryptography Impact Encryption Protocols? - Internet Infrastructure Explained
Internet Infrastructure Explained
0 views

45:48
HOPE Number Six: Constructing Cryptographic Protocols
Matha Stecker
0 views

9:35
Foundations of Cryptography || Cryptographic Protocols || PART-6 || #cybersecurity #cryptography
Cyberguardian Rushi
15 views
0:30
What is the purpose of a nonce in cryptographic protocols?
Computer Science Quizzes
60 views

1:00
Exploring Quantum Cryptographic Protocols
MoreTECH
96 views

3:38
Rav Shmuel Protocols
Pfff
1 views

2:46
JFK Secret Service Protocols
Krill
4 views

1:18
DEEPAK KUMAR PATTANAYAK - Protocols
PoemHunter.com
3 views

0:37
Vikram Seth - Protocols
PoemHunter.com
157 views

2:53
Application protocols
Cryonic Medical
52 views
6:57
WAN Protocols
Punjab Group Of Colleges
4 views
10:46
45.Common TCPIP Protocols
StudyNetworking
18 views

0:05
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Kurtanidze 83
0 views

0:05
Read Introduction to Modern Cryptography: Principles and Protocols (Chapman & Hall/CRC Cryptography
Kaanaana20
0 views

0:05
Read Cryptography: Protocols Design and Applications (Cryptography Steganography and Data Security)
Epataraia
0 views
![[PDF] Operational Semantics and Verification of Security Protocols (Information Security and](/image/s1.dmcdn.net/v/FVG161e0X8s_TZyY4/xx720.pagespeed.ic.3BE1Bzcodl.jpg)
0:07
[PDF] Operational Semantics and Verification of Security Protocols (Information Security and
SoletteHawkins
8 views
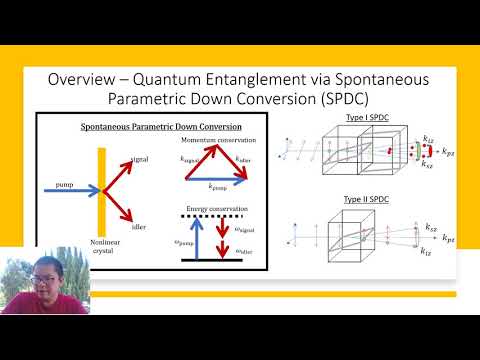
5:47
Brian Tey 17142084/1 Study of Quantum Cryptography Protocols for Secure Quantum
Brian Tey
34 views
Previous Page 2