Search Results for "Network Security Protocols"
Find videos related to your search query. Browse through our collection of videos matching "Network Security Protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Network Security Protocols"
50 results found

10:16
Cryptography and Network Security Protocols - Part 8
Information Security Awareness
25 views

20:31
27-Secure Socket Layer (SSL) Part 2 | Handshake & Alert Protocols | Cryptography & Network Security
Sundeep Saradhi Kanthety
90.1K views
3:05
How Do Cryptographic Protocols Like RSA Secure Network Security? - Talking Tech Trends
TalkingTechTrends
1 views

3:17
How Do Network Security Protocols Like HTTPS Protect Your Data? - Talking Tech Trends
TalkingTechTrends
1 views

13:26
Essential Guide to Network Security and Wireless Protocols | Insights from a Cybersecurity Expert
Skillfloor
6 views
10:34
Cryptography and Network Security Protocols - Part 1
Information Security Awareness
87 views
13:57
HTTPS Security | SSL | TLS | Network Protocols | System Design
ByteMonk
28.7K views

1:21
Solar Energy - Renewable Energy - Montreal Protocols & Kyoto Protocols
Cyber Energy Ltd
11 views
![[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley](/image/s2.dmcdn.net/v/Pt3_y1e9_0lvZvH-V/xx720.pagespeed.ic.GE78wmqjuE.jpg)
0:33
[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley
phamza-elhaddars
7 views

0:08
Read [ AACN Protocols for Practice: Noninvasive Monitoring[ AACN PROTOCOLS FOR PRACTICE: NONINVASIVE
Airini Arono
0 views

0:05
Download Telephone Triage Protocols for Adults 18 Years and Older (Telephone Triage Protocols
MarianRench
1 views

4:37
Adherence to Covid-19 Protocols: Clamp-down on persons violating protocols begins (10-8-21)
The Multimedia group
3 views

0:35
Best product Telephone Triage Protocols for Nurses (Briggs, Telephone Triage Protocols for
walker
1 views

0:36
TCP/IP Illustrated, Volume 1: The Protocols: Protocols v. 1 (APC) Review
yoheg
5 views

0:59
Protocols | meaning of Protocols
The Definition Channel
504 views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

14:40
SECURITY ATTACKS || TYPES || ACTIVE || PASSIVE || OSI SECURITY ARCHITECTURE --NETWORK SECURITY
t v nagaraju Technical
35.3K views

6:31
Network Security vs Cyber Security | What is Security? | Explained in Hindi
Tech Guru Manjit
16.0K views

0:06
Read Security+ Guide to Network Security Fundamentals (Cyber Security) PDF Free
Tbestavashvili
1 views

0:05
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Kurtanidze 83
0 views
![[PDF] Operational Semantics and Verification of Security Protocols (Information Security and](/image/s1.dmcdn.net/v/FVG161e0X8s_TZyY4/xx720.pagespeed.ic.3BE1Bzcodl.jpg)
0:07
[PDF] Operational Semantics and Verification of Security Protocols (Information Security and
SoletteHawkins
8 views

0:08
Read Operational Semantics and Verification of Security Protocols (Information Security and
Kstocker
0 views

0:24
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook Free
London Schwartz
2 views

22:37
Internet Security Protocols IPSEC | Cryptography and System Security
Ekeeda
89 views

0:06
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Hannawald
0 views

0:08
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Mlexer
1 views

6:33
What Is Network Marketing Network Marketing Explained! What Is Network Marketing Anyways
Most Popular Videos
1 views

11:37
What is Pi Network | Pi Network in Pakistan | Pi Network kya Hai | Pi Cryptocurrency Review in urdu
90s Mentor
25 views

7:54
Network Marketing Nedir, Neden Network Marketing, Network Marketing Gerçeği
musaduman
3 views

45:59
01731, Network Steganography / Network Information Hiding, Chapter 7a Network-level Countermeasures)
Steffen Wendzel
812 views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

28:12
Computer Network & Lab | Network Security and Privacy | CSE | AKM Monzurul | University of Scholars
University of Scholars
12 views

11:03
Unit 4 Asymmetric Key Algorithm ▶️Cryptography and Network Security #makaut #ai#cryptography#network
Makaut Smashers
85 views
12:05
What is Network Security? | Types of Network Attacks | How these Attacks are done
Tech Guru Manjit
14.6K views

3:14
lecture 5 classification of encryption technique in cryptography & network security #viral network
GainThroughIT
17 views

39:52
Network Security | What is a network and reference model? | Great Learning
Great Learning
4.4K views

13:07
Network Protocols Explained: Networking Basics
WhiteboardDoodles
434.1K views

1:03:26
Automatically Binding Cryptographic Context to Messages in Network Protocols Using Formal Methods
UCYBR - UMBC Center for Cybersecurity
60 views

1:06:45
Colloquium: Gláucia Murta: Device-independent quantum cryptography: towards network protocols
Instituto de Física Teórica, IFT-UNESP
209 views
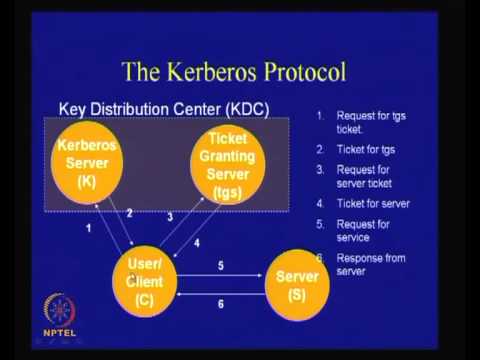
55:26
A Tutorial on Network Protocols
nptelhrd
12.3K views

0:38
Full version Attacking Network Protocols: A Hacker's Guide to Capture, Analysis, and
JoyceMendez1308
1 views

10:20
Computer network protocols
BPSC TRE COMPUTER SCIENCE
9 views

3:05
Do Internet Encryption Protocols Cause Network Performance Overhead?
Internet Infrastructure Explained
0 views

12:27
Network Protocols - ARP, FTP, SMTP, HTTP, SSL, TLS, HTTPS, DNS, DHCP - Networking Fundamentals - L6
Practical Networking
2.2M views

23:43
Networking For Hackers! (Common Network Protocols)
Hacker Joe
1.0M views

0:33
Full Version Attacking Network Protocols: A Hacker's Guide to Capture, Analysis, and
dm_d0697032f1d08d949273cd69d0d7b40d
1 views
Previous Page 2