Search Results for "Multi-factor Authentication"
Find videos related to your search query. Browse through our collection of videos matching "Multi-factor Authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Multi-factor Authentication"
50 results found
1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views
2:20
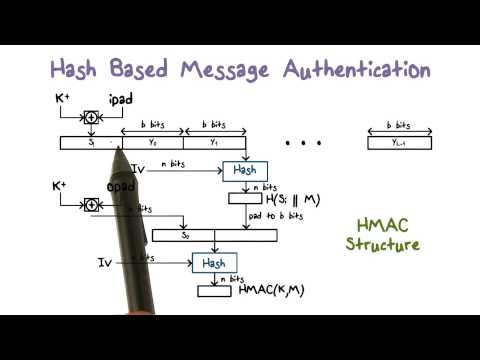
Hash Based Message Authentication
Udacity
59.1K views
16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

0:20
What is Biometric Authentication? #Cybersecurity #TechEducation #onlinelearning #definitions #short
Keerthan V Suvarna
38 views

0:41
🔐 IKE Authentication Explained Secure Cisco VPN | IPsec & Pre Shared Key Step by Step #ccnpsecurity
CoreSah Networks
212 views
14:13
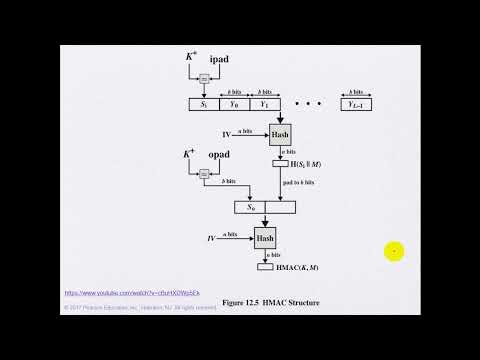
Chapter 12 - Message Authentication Codes
j neama
1.9K views

6:35
Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Unbeaten Learning
112.9K views
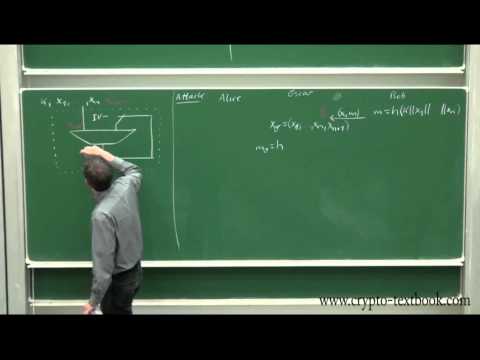
1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

13:19
18_Public Key Cryptography - Key pair, Secrecy and Authentication
Angayarkanni S A
238 views

2:24
Network Security and Cryptography: Message Authentication Code(MAC)
OnlineTeacher
598 views
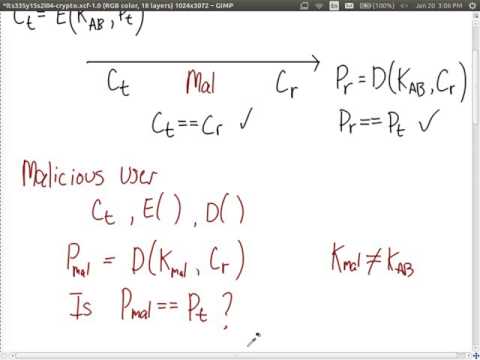
1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views
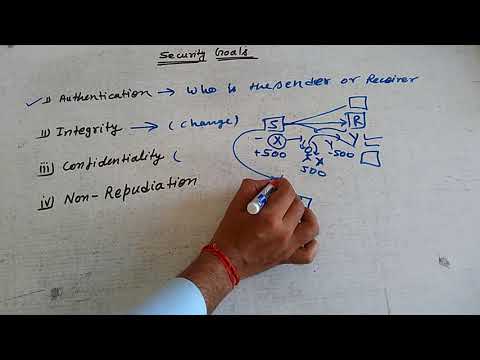
9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

13:16
Public Key vs Private Key | SSH Authentication | DevOps Realtime Interview Questions
DevOps and Cloud with Siva
12.4K views
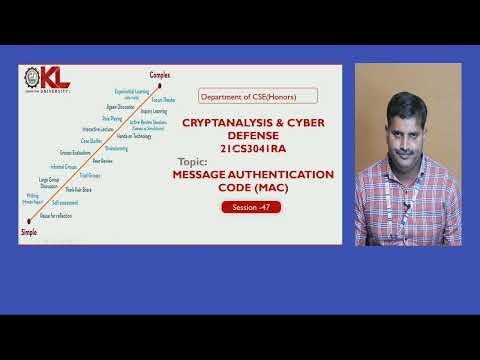
13:23
Message Authentication Code (CO4: Session-7)
Cyber Security
47 views
8:51
A Secret-Sharing-Based Method for Authentication of Grayscale Document Images via the Use of the PNG
JP INFOTECH PROJECTS
1.6K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

4:33
Authentication fundamentals: The basics | Microsoft Entra ID
Microsoft Azure
253.3K views

10:25
Network Security 4.4: Message Authentication Codes (MACs)
Cihangir Tezcan
258 views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

26:44
Message Integrity and Authentication
Computer Science Learning Videos
336 views

1:00
Authentication vs Authorization
A Binary Code
92.8K views

7:43
Secure Wireless Authentication & Encryption Methods: Protecting Your Wi-Fi
Hans IT Academy
35 views

8:02
5.1 Introduction to Authentication
IST OnlineLearning
518 views

13:01
Message Authentication Code MAC
Ekeeda
284 views

3:24
MAC (Message Authentication Code) | Unit 4 Cryptography and Cyber Security CB3491 | Anna University
CSE IT Exam Preparation
1.1K views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

10:06
Message Authentication Codes (MACs)
Tanja Lange: Intro to crypto
855 views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views

27:44
Behavioral Biometrics: Re-inventing Authentication using Python | SciPyLA 2019 | Jesús Solano
SciPy Latin America
263 views

1:09:38
CSE571-11-15B: User Authentication Protocols (Part 2 of 3)
Raj Jain
1.8K views

3:17
Image Steganography | Digital Image Password | Image Authentication System using Arduino (latest )
Techpacs
455 views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views

11:49
Network Security - Message Authentication Code (MAC) | Cryptography and Network Security
Lectures by Shreedarshan K
2.5K views

12:56
CMAC Explained: A Deep Dive into Cipher-based Message Authentication
Network Technician
6 views

2:07
What Is A Message Authentication Code? - SecurityFirstCorp.com
SecurityFirstCorp
14 views

0:47
Biometric Authentication in Cybersecurity
Tomorrow’s Tech Today
17 views
1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views
17:04
UNIT IV-COMMUNICATION SECURITY,AUTHENTICATION PROTOCOLS
janadeep n
24 views

9:37
Introduction of Message Authentication Code (MAC) | Application of MAC | Cryptographic MAC Function
Chirag Bhalodia
31.5K views

22:57
20-What is X.509? | Digital Certificates & Authentication in Network Security | Part 1
Sundeep Saradhi Kanthety
127.1K views
1:06:48
Camp++ 0x7e2 // Modern cryptographic password and authentication methods by stf
Budapest Hackerspace
168 views

4:33
Kerberos Realm | Inter-realm authentication in kerberos Realm
Chirag Bhalodia
14.1K views
0:55
OSPF Authentication Types #ospf #ccna #ccnp #cybersecurity #networking #routingprotocol
IT INDEX
277 views

15:10
4.5 Message Authentication Code(MAC) Part 1 in Tamil
BECAUSE
21.3K views
14:06
Authentication Bangla tutorial 2 : encrypting database
Anisul Islam
5.3K views

22:09
PhotoProof: Cryptographic Image Authentication for Any Set of Permissible Transformations
IEEE Symposium on Security and Privacy
851 views

47:47
Cryptographic Binding Should Not Be Optional: A Formal-Methods Analysis of FIDO UAF Authentication
UCYBR - UMBC Center for Cybersecurity
99 views