Search Results for "Multi-Factor Authentication"
Find videos related to your search query. Browse through our collection of videos matching "Multi-Factor Authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Multi-Factor Authentication"
50 results found

5:28
Module 5.1_ Message Authentication requirements
bushara abdulrahim
4.1K views
6:05
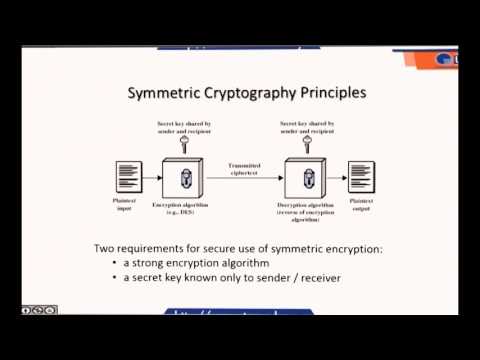
LECTURE 2- AUTHENTICATION AND BASIC CRYPTOGRAPHY (PART2)
UTeM MOOC
40 views

7:00
Authentication Header in IP Security #youtube #cryptography #ipsecurity #networksecurity #videos
Lab Mug
338 views

12:56
60 Multifold Secured Bank Application authentication service using Random Visual Cryptography and Mu
ICMISC
13 views
14:41
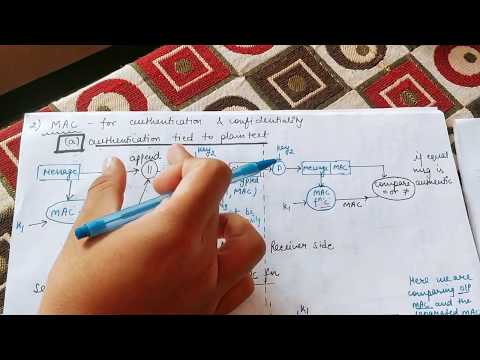
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views

6:43
Kerberos Authentication Protocol 🔥🔥
Perfect Computer Engineer
198.5K views

24:09
Passwordless Authentication Using Steganography, Cryptography And Biometrics - Tunde Oduguwa
BSides Bristol
39 views

10:23
Analysis of Biometric Authentication System – Security Issues and Working using Visual Cryptography
OKOKPROJECTS
114 views

59:27
CCoE Webinar Series: Stronger Security for Password Authentication
Trusted CI
148 views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

2:31:55
Network Security Full Course ! Cyber Security Tutorial ! Cryptography ! Encryption ! Authentication!
Sharan S
468 views
1:01
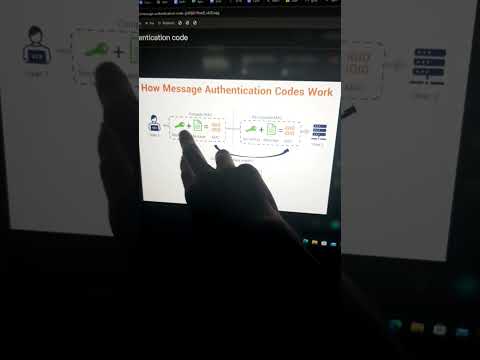
Cryptography - MAC - Message Authentication Code #cryptography
Alon Lalezari - אלון ללזרי
1.2K views
1:20:56
COSIC Course 2024: "Cryptographic protocols for entity authentication and..." (Bart Preneel, COSIC)
COSIC - Computer Security and Industrial Cryptography
239 views

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views

25:20
Future-proofing authentication: A look at the future of post-quantum cryptography, Authenticate 2025
Yubico
468 views

9:01
Message Authentication Code (MAC) in Cryptography Hash Function || Network Security in Telugu
Lab Mug
14.3K views

2:31
Cryptography And Network Security :-Authentication And key Agreement
Bharati Kale
496 views
10:37
Authentication by Encrypted Negative Password in Python
OKOKPROJECTS
183 views

15:15
5 - 1 - Message Authentication Codes-Cryptography-Professor Dan Boneh
Domonique Harder
123 views

0:05
Read Access Control Authentication And Public Key Infrastructure (Information Systems Security
Tuuli Mark
1 views

0:05
Download Access Control Authentication And Public Key Infrastructure (Information Systems Security
Maisi Baker
2 views
![[Read PDF] Mobile Authentication: Problems and Solutions (SpringerBriefs in Computer Science)](/image/s2.dmcdn.net/v/Gz4Gl1e0GalIcGrjm/x720)
0:24
[Read PDF] Mobile Authentication: Problems and Solutions (SpringerBriefs in Computer Science)
Aron Davonte
1 views
2:38
How To setup VPS with Public Key Authentication (Bitvise ssh)
panduanvps
3 views

0:30
Review ACCESS CONTROL AUTHENTICATION PUBLIC KEY INFRASTRUCTURE 2E (Jones Bartlett Learning
katewebix
1 views

1:08
Client authentication: Systems that are more and more secure
Orange
71 views

0:30
About For Books Mechanics of User Identification and Authentication: Fundamentals of Identity
dm_09d226e7605f9f5a1a3a6425e52120d4
0 views

7:13
#35 MAC ( Message Authentication Code ) - Working and Significance |CNS|
Trouble- Free
223.0K views

9:30
AAA and Authentication - CompTIA Security+ SY0-501 - 4.1
Professor Messer
117.2K views

58:48
Proxies, Linux SSH Servers, Windows Clients and Public Key Authentication - Hak5
Hak5
4 views

3:29
How Does Cryptography Enable Passwordless Authentication? - Next LVL Programming
NextLVLProgramming
8 views
47:24
Patterns of Authentication and Self-Announcement in IoT
DiscoverDev
49 views

0:46
Secure Biometric Authentication Using Privacy-Preserving Cryptographic (Trailer)
IEEE Signal Processing Society
27 views

8:26
Authentication vs Authorization | With Animation and Real Life Analogy
Gourab Banerjee
2.2K views
3:20
How is public-key encryption used in authentication?
The Security Buddy
1.3K views

10:48
Module 5.3_Message Authentication Code,Secure communication ktu s8 ec #engineering #ktutuition
bushara abdulrahim
2.3K views

6:08
Kerberos - authentication protocol
Sunny Classroom
506.1K views
![File Hider Java Project [Unique]: Learn Encryption, OTP, and Email Authentication With Source Code](/image/i.ytimg.com/vi/_31XdRjJ4pM/hqdefault.jpg)
2:11:46
File Hider Java Project [Unique]: Learn Encryption, OTP, and Email Authentication With Source Code
Sheryians Coding School
99.3K views

13:18
Authentication protocol | Cryptography and Network Security
Ekeeda
2.0K views

11:49
Network Security - Message Authentication Code (MAC) | Cryptography and Network Security
Lectures by Shreedarshan K
2.5K views

14:23
Cybersecurity project on image authentication using visual cryptography.
Chaitanya sai
661 views

56:34
Multimedia Network Security | Authentication | Digital Signature |Digital Fingerprint |Steganography
COMPUTER CHI DUNIYA
64 views

5:55
#Authentication Requirements In Cryptography and Network Security #cns #jntuh #conceptclearbydrmvk
Concept Clear
733 views

26:44
Message Integrity and Authentication
Computer Science Learning Videos
336 views

4:48
Message Encryption A type of authentication
Abisha D
292 views

0:26
EKE Authentication - Applied Cryptography
Udacity
1.4K views

7:42
Digital Signature - Asymmetric Key , Why used for Authentication & Non Repudiation (Hindi)
Easy Engineering Classes
177.3K views
0:34
Public Key Authentication #remoteaccess #pki #sdntechforum #networksecurity #sshd
SDN TechForum
232 views

22:57
20-What is X.509? | Digital Certificates & Authentication in Network Security | Part 1
Sundeep Saradhi Kanthety
127.1K views

32:24
public key encryption: Key distribution, message Authentication and hash function- part1
Dr. Moonther
384 views
1:36
Radius Authentication
mosherlisa75
1 views
Previous Page 2