Search Results for "Maintaining Access"
Find videos related to your search query. Browse through our collection of videos matching "Maintaining Access". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Maintaining Access"
50 results found

1:09
Inside Access To The Bills Locker Room Following Win Over The Panthers! #shorts #nfl #buffalobills
Buffalo Bills
68.7K views
21:16
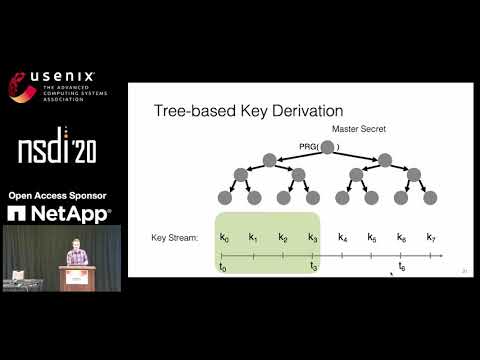
NSDI '20 - TimeCrypt: Encrypted Data Stream Processing at Scale with Cryptographic Access Control
USENIX
924 views

2:30
What Is Unauthorized Access? - SecurityFirstCorp.com
SecurityFirstCorp
307 views

15:52
CISSP Domain 5 Walkthrough: Identity & Access Controls Demystified
INFOSEC TRAIN
8.9K views
28:14
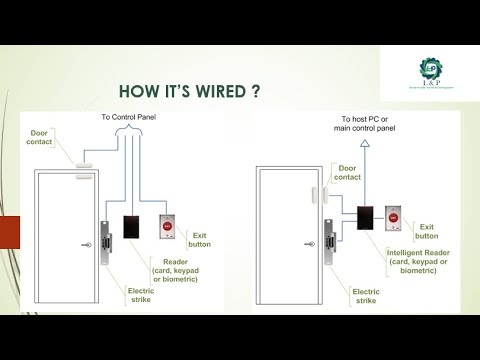
ACCESS CONTROL SYSTEM BASICS PART 1 OF 5 ENGLISH
L&P RENEWABLE SYSTEM INTEGRATOR
3.3K views

5:48
Access Control Models: An Overview of the Four Main Types
GetSafeAndSound
31.1K views

9:21
CSMA (Carrier Sense Multiple Access) Protocol in Computer Networks
Sudhakar Atchala
92.1K views

3:42
How Can I Protect My Network From Unauthorized Access and Data Breaches? | SecurityFirstCorp News
SecurityFirstCorp
16 views

2:01
Get to Know Patriots Wide Receiver DeMario Douglas | Patriots All Access
New England Patriots
964 views

7:49
Access Controls - CompTIA Security+ SY0-701 - 4.6
Professor Messer
85.2K views

0:21
How to wire an access control system Quick & Easy Guide #accesscontrol #shortsfeed
Electrical genius
137.5K views

0:48
Card + Pin Password | Access Control Reader | 8019619680 |SA-32 | #accesscontrolinstallation #essl|
Right Vision Security Systems
79.8K views

0:27
Getting Ready To Self-Access My Port
Shayla Talei
6.3K views

6:58
Secure Cloud Computing Access via Hybrid Encryption Techniques
U.K.K Sandeepa
149 views
2:26
Unauthorized Access Admin Panel Vulnerability
Ibnu Fachrizal
230 views

0:55
How to secure your Facebook account to prevent unauthorized access?
Ask About Money & Health
41 views

2:32
CISSP Introduction: Domain 5 -Identity and Access Management
Secure Ideas
79 views

0:20
Condo Security FAQ How can we prevent unauthorized access in a condominium
Guard-TAC
6 views

8:47
Essl JS-32E Standalone Access control Power supply, EM Lock & Exit switch Wiring connection
TECHLOGICS
166.0K views

5:58
Identity & Access Management
SecureLearn for CISSP & CISA Training
136 views

0:25
Hackers Gained Unauthorized Access to Government Agency for Months: CISA
Tech News Today
280 views
![[Part I] Bug Bounty Hunting for IDORs and Access Control Violations](/image/i.ytimg.com/vi/BfbS8uRjeAg/xhqdefault.jpg.pagespeed.ic.b8-iPWgdqS.jpg)
1:33:18
[Part I] Bug Bounty Hunting for IDORs and Access Control Violations
rs0n_live
81.6K views

3:02
Dodger Stadium All-Access Tour | Legendary location of the Los Angeles Dodgers!
MLB
32.0K views

7:14
What is aws access points EFS (Elastic File System) | Aws Training Tutorial | Aws Beginner Guide
MyLearningSense
4.6K views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views
12:32
Intro to Access Control: Diversified Keys, RSA, Asymmetric Encryption, & Other Smart Card Security
SchlageSecurity
6.2K views

11:26
CISSP Domain 5 Review / Mind Map (1 of 2) | Access Control Overview
Destination Certification
56.1K views

20:08
how to get remote access to your hacking targets // reverse shells with netcat (Windows and Linux!!)
NetworkChuck
2.6M views

1:06
How to download IEEE paper free without access permission in 2022
Huỳnh Hữu Nhân
90.5K views
5:05
How to Access Free PDF Versions of Paid Books: Easy Tips and Tricks #freebook , #freepdf #learning
NET GUIDE
113 views

2:26
How To Prevent Unauthorized Access? - SecurityFirstCorp.com
SecurityFirstCorp
115 views

0:10
Dark web quickest way to access😳😀😀🤩🤩🤩
Real Code Camp Tv
143.4K views

2:07
How To Detect Unauthorized Access? - SecurityFirstCorp.com
SecurityFirstCorp
97 views

5:41
How Access Control Systems Work | Point Monitor Corporation
Point Monitor Corporation
53.8K views

30:04
CCT 022: Access Control Types (CISSP Domain 5) #shongerber
CISSP Cyber Training - Shon Gerber
25 views

23:11
CISSP Domain 5: Identity and Access Management (CISSP IT-Tutorial)
sumon infosec
402 views

0:37
The Unauthorized Access. #foryou #series #shorts #movieclips #drama
RyDca
13.3K views
1:00
How to get rid of Request Access on Google Drive
Tarver Academy
107.9K views

2:25
What Are Some Examples of Unauthorized Access? - SecurityFirstCorp.com
SecurityFirstCorp
146 views

1:04
BETTER-AUTH's built in access controls are 👏🏻👏🏻👏🏻👏🏻👏🏻
Syntax
6.9K views
7:44
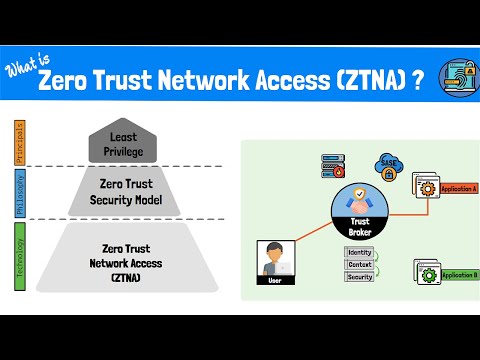
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
The CISO Perspective
164.3K views
1:36
Samsung Wallet Finally Supports NFC Access Cards. Here’s How It Works
SoyaCincau
143.9K views

1:09
Unauthorised Access (From "Casino Royale" Soundtrack)
David Arnold - Topic
63.9K views

0:57
What is Unauthorized access ?cyber security terminology #cybersecurity #vlrtraining #education
VLR Training
454 views
14:34
How to Secure Switch from unauthorized access
Dipak Bari
3.2K views
2:15
How to Access YouTube Trending After It Was Removed – See Trending Videos on YouTube
Explainic
1.2K views

1:07
BIOS Passwords Protect Against Unauthorized Access
ISEA - Stay Safe Online
78 views

0:36
CyberSecurity Definitions | Mandatory Access Control
Relative Security
1.9K views

3:06
【HSR Silver Wolf Fan Song】Hanser - Unauthorized Access lyrics 越權訪問 繁中歌詞 (Color Coded Lyrics)
Yvelisse
767.8K views

37:42
Unauthorized Access
cultdeadcow
27.2K views