Search Results for "Linux Security"
Find videos related to your search query. Browse through our collection of videos matching "Linux Security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Linux Security"
50 results found

8:08
windows 10 hacking Kali Linux | Windows 10 Exploit Kali Linux
Kali Linux Tutorial
16 views

54:58
Linux Training for DevOps | Linux Tutorials for DevOps | DevOps Online Training
usedevops
4 views

7:58
Kali Linux dual boot setup | Encrypted Kali Linux installation, the Logical Volume Manager
prime-rad-sec
33 views

0:35
Online Comptia Linux+ Guide to Linux Certification For Free
dm_f354ab4d2138363e5339bd3011feaba5
2 views

0:40
Full version Comptia Linux+ Guide to Linux Certification Complete
dm_c924e51076f89b89ddc177e609276e98
1 views

3:43
LINUX y GNU LINUX: QUÉ ES y CÓMO FUNCIONA
Genbeta
42.6K views

1:48
Embedded Linux Porting _ Upskill Embedded Linux Engineering _ RuggedBoard
Rugged Board
6 views

1:02
How to Upgrade Kali Linux | Update Kali Linux to Latest Version
Hardik Gehlot
15 views

2:26
How to Run Kali Linux on Windows without VirtualBox | Kali Linux App
Hardik Gehlot
82 views

8:11
LinkedIn Linux Assessment Questions and Answers 2023 - Linkedin Linux Quiz Answers - Linkedin Skill Test Answers 2023
RB Tech Tips
54 views
10:18
Is Linux Different? | Understanding Linux | Part 3
NixNexus
23 views

15:44
Kali linux Tutorial For Beginners (2021) : #Kalilinux Course | Kali Linux Commands 2021 - Part5
Artificial Intelligence 🤖
36 views

7:33
How to Make A Kali Linux 2021.2 Bootable USB - Persistent Kali Linux USB Drive
Steam Labs
1.4K views

20:39
Kali linux Tutorial For Beginners (2021) : #Kalilinux Course | Kali Linux Commands 2021 - Part3
Artificial Intelligence 🤖
32 views

15:10
How to Install Kali Linux 2025 in VirtualBox | Kali Linux 2025.1
Techy Druid
405.5K views
0:49
Linux for Windows? #shorts #linux #windows #wsl #kalilinux
David Bombal
1.2M views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views
11:30
DIY Cyber Security Tool Under $10! Create Your Own Kali Linux Bootable Flash Drive!
GhostStrats
6.3K views

0:13
Best AI Tools Used By Hackers || Used To Kali Linux || Used Cyber Security || Used Forensic Lab
WOW COMPUTER
264 views

1:30
Burp Suite Quick overview on Parrot Security Linux
GoPenTests
591 views

5:16
Linux in Windows Operating System | Hacking Area | Cyber Security | Easy Bash script execution
Hackerala 1.1
109 views

5:50
VERIFY MD5 / SHA256 Hash or Checksum on Linux - File Security (Ubuntu)
SavvyNik
13.3K views

0:08
Download Advanced Guide to Linux Networking and Security by Ed Sawicki (2005-09-26) Ebook Online
Daugaard
3 views
3:29
Security Academy Practical Ethical Hacking - Exploring Kali Linux
Tutorials Arena
304 views
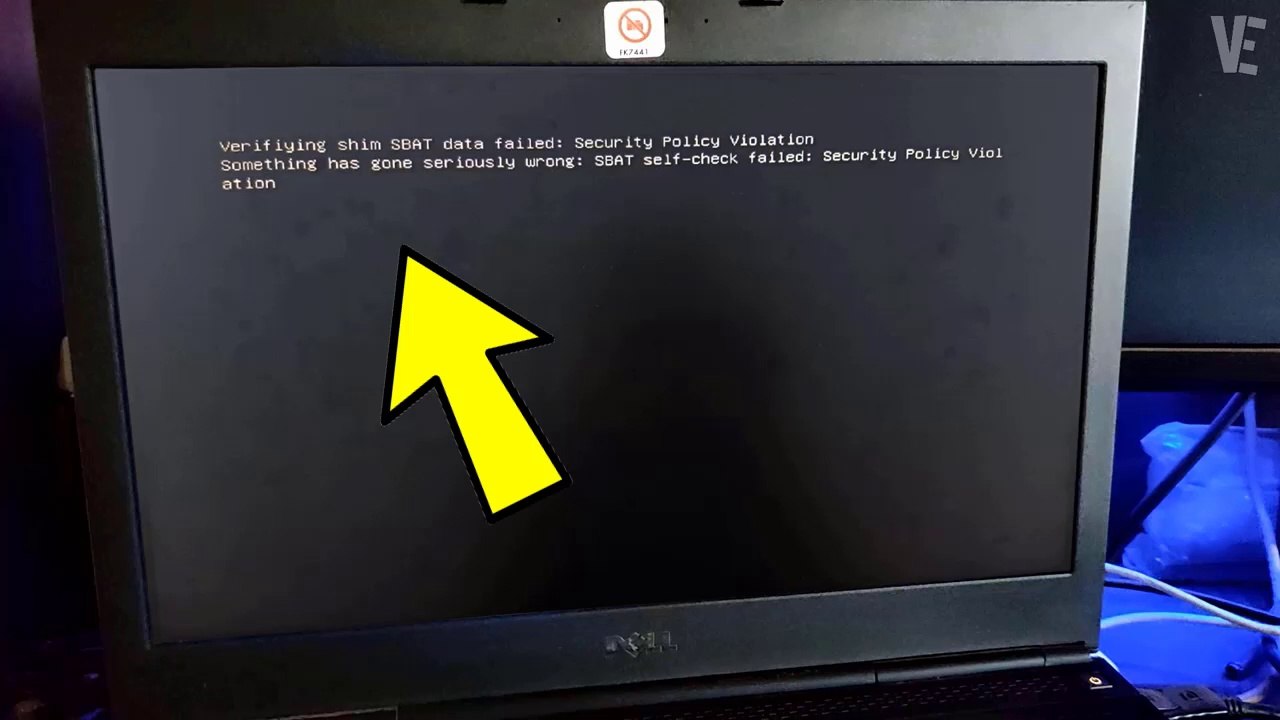
2:07
How To Solve Error "Verifying shim SBAT data failed Security Policy Violation" When Starting Dual Boot (Windows 11 + Ubuntu Linux)
VictorExplains
881 views

0:28
Linux Security Quiz #3 - Symmetric Encryption
Merge To Master
28 views
8:44
Using Steghide in Kali Linux to store Hidden Information | ASWIN MURALI |Cyber Security
ASWIN MURALI
156 views
0:35
Breaking Down RSA (Private Key & Decryption) #cybersecurity #linux #encryption #security
Black Bat Terminal
2.5K views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

44:58
Computer Security | What Is Computer Security | Cyber Security Tutorial | Simplilearn
Simplilearn
95.6K views

12:04
Approaches of web security in urdu hindi | approaches of web security lecture | web security | p 49
IT Expert Rai Jazib
1.3K views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

44:53
Networks Security | Security Services | Security Goals | Cryptography | Steganography | Attacks | IA
Bhavishya Coaching SGNR
929 views

3:44
Cyber security क्या है? | What is Cyber Security in Hindi? | Why Cyber Security is Important?
Deepak TechTimes
59.8K views

9:13
What is Security and security attacks, security services in CNS
Lab Mug
13.4K views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

5:10:06
Cloud Security Full Course | Cloud Security Fundamentals | Cloud Security Training | Intellipaat
Intellipaat
80.6K views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

13:10
Types of security policies, www policy, email security policy, cyber security lecture series
Gaurav Khatri
9.3K views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

10:19
#2 Security Approaches and Principles or Goals of Security- Cryptography |Information Security|
Trouble- Free
99.1K views