Search Results for "Implementation Attacks"
Find videos related to your search query. Browse through our collection of videos matching "Implementation Attacks". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Implementation Attacks"
50 results found

5:01
What Causes Anxiety Attacks? Causes of Anxiety Attacks
alextaylor1720
287 views

2:34
Fauci says attacks on him are 'attacks on science'
USA Spot News
15 views

10:55
Leopard attacks dog dog attacks leopard dog wins
WildFilmsIndia
2 views

10:55
Leopard attacks dog, dog attacks leopard dog wins
WildFilmsIndia
94 views

0:41
Vampire Attacks - Desi vs English - How Vampire Attacks in Pakistan vs Other Countries
FunkarNews
102 views

9:32
Top 10 Cyber Attacks In History | Biggest Cyber Attacks Of All Time | Cyber Security | Simplilearn
Simplilearn
359.4K views

14:51
DoS / DDoS ATTACKS IN CYBER SECURITY || Denial of Service || Distributed Denial of Service Attacks
Sundeep Saradhi Kanthety
35.7K views

5:07
J&K Terrorist attacks: Pakistan High Commission condemns terrorist attacks in Jammu
NewsX
322 views

2:57
Most Amazing Wild Animal Attacks - Crocodile vs Zebra - Crocodile Attacks Zebra - Lion vs Zebra
Tout est art
822 views

4:47
PBL RKS-115 Implementation of Cryptographic Algorithms in Steganography and Puzzle Game
Kelompok 5 PBL-115 RKS
35 views

4:46
Demonstration of Implementation of Image Steganography using LSB Technique and Morse Code.
ProkillerGirl
110 views

4:28
Post-Quantum Cryptography: implementation from theory to practice
IDEMIA Group | Unlock the World
1.2K views
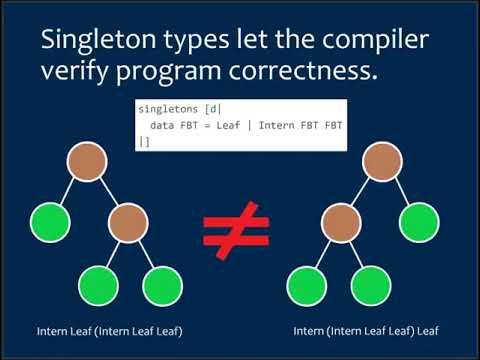
10:36
Haskell Implementation of Key-Homomorphic PRF based on Lattice Cryptography
Michigan Engineering - Honors Program
180 views

0:41
RSA Cryptography Implementation with Socket (Android + JavaFX) with Source Code
eslam gad
841 views
0:12
Implementation Attack
Quick Cybersecurity Study
117 views

19:15
Securing The Future: Cloudflare's Implementation of Post-Quantum Cryptography - Michiel Appelman
Cloudflare
581 views

2:42
Cryptography/Caesar Cipher Decryption/ Matlab Implementation with in 3 Min
Hayder Mazin
1.7K views

15:41
Python Implementation in CS - Caesar Cipher (Cryptography) | Code Analysis - EP 01 | Ran$ome
Ran$ome
84 views

1:29:13
What is Cryptography? | Introduction to Cryptography | Java and C++ implementation | Caesar Cipher
The CS Revelation
442 views

1:28
C++ : Implementation of AKS primality test in Scheme or C++
Hey Delphi
70 views

25:25
How to Reveal the Secrets of an Obscure White-Box Implementation | Junwei Wang | RWC 2018
Real World Crypto
1.0K views
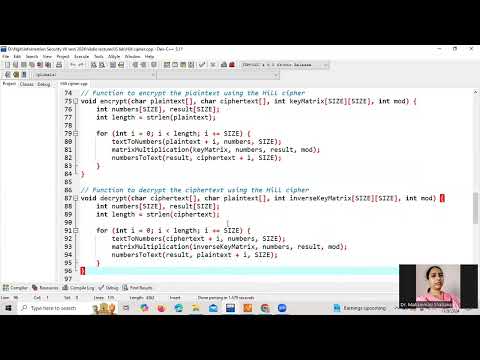
9:01
6 Hill cipher 'c' implementation
Neil gogte Institute of Technology
164 views

17:30
Mode-Level vs. Implementation-Level Physical Security in Symmetric Cryptography: A Practical Gu...
IACR
316 views

22:44
Part 3 Unlocking Cryptography - Caesar Cipher Implementation with C
Ai000 Cybernetics QLab
53 views

18:58
Modern Cryptography & Implementation Flaws | RSA Conference
RSA Conference
7.0K views
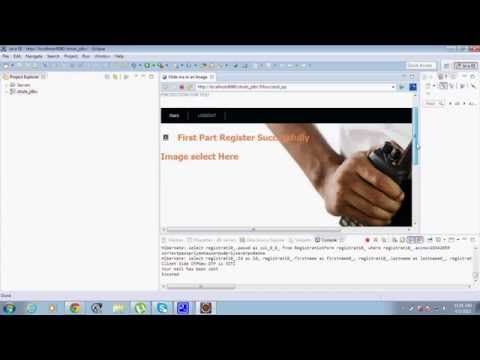
5:04
Implementation of hybrid security layer of steganography and cryptography on a credit card purchase
Banu Rekha
177 views

16:15
What is Data Fabric architecture? Implementation best practices & design principles
Future of AI & Data
3.4K views

2:31
Implementation Hide Text In Image with encryption Using Digital Steganography Technique
Ebtsam Alkhawlani
156 views

49:31
DeepSec 2010: Mobile VoIP Steganography: From Framework to Implementation
Christiaan008
492 views
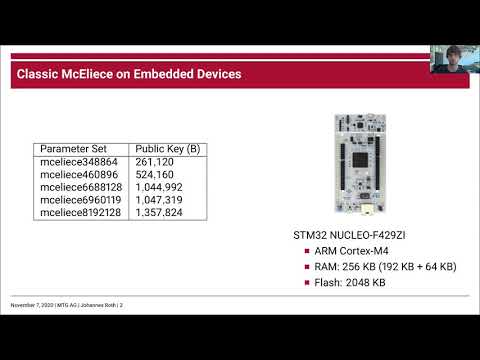
24:51
Classic McEliece Implementation with Low Memory Footprint
MTG AG – Enterprise Resource Security
336 views

19:08
Stack Implementation Using Linked List C++ | Stack Using Linked List C++ | Data Structures Playlist
Coding With Clicks
5.4K views

5:24
RSA Algorithm | Encryption and decryption | Implementation in java
BLENDIDE
10.3K views

20:17
Live Demonstration & implementation of Caesar Cipher Algorithm | Java Coding Exercise | @TechRanch
Tech-Ranch
885 views

2:23
Steganography - Explanations & Implementation ( Easy To Understand)
CompuSalle
176 views

22:57
Cryptography - Caesar Cipher - Theory and Implementation
Asib
32.2K views

24:51
Classic McEliece Implementation with Low Memory Footprint - CARDIS 2020
CARDIS Conference
368 views
25:41
Exploratory Data Analysis Explained for Beginners-Python Implementation
AI Sciences
621 views

32:29
RSA Algorithm Explained + implementation
Tech With Nikola
13.7K views
9:47
Machine Learning Tutorial 13 - K-Nearest Neighbours (KNN algorithm) implementation in Scikit-Learn
ProgrammingKnowledge
165.6K views
40:10
Crypto: Caesar Cipher explained | Java implementation
The CS Revelation
8.6K views

3:33
What Are The Advantages Of Quantum Cryptography Implementation? - All About Capitalism
All About Capitalism
3 views

7:33
RSA - Algorithm for Asymmetric Cryptography (JAVA Implementation)
Rafael Queiroz Gonçalves
2.1K views

2:00
Importance of Timing and Implementation of Post Quantum Cryptography
Cybersecurity Insights
152 views

30:56
Queue Data Structure - Queue Operations - Queue Implementation using Array - DSA Course
Coding With Clicks
29.8K views

22:50
Towards Practical Implementation of Quantum Key Distribution for Secure Communication in the Post
Citedi IPN
37 views
31:09
LSB & Jsteg Steganography implementation and comparison
Manohar Koya
1.5K views

0:06
Read A Comprehensive Lecture Notes on RSA-1024 Cryptography: Implementation by Using Java Remote
Ljepsen
1 views

0:05
Download Synthetic Datasets for Statistical Disclosure Control: Theory and Implementation (Lecture
Solene Loup
2 views

0:26
Read Book Language Processing with Perl and Prolog: Theories, Implementation, and Application
Zeljko Adiputera
2 views

1:06
Trump says US to 'cease all implementation' of Paris accord
AFP English
0 views