Search Results for "Forensics Challenge"
Find videos related to your search query. Browse through our collection of videos matching "Forensics Challenge". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Forensics Challenge"
50 results found

1:08
how to detect steganography files in windows stegdetect computer forensics
Aravind Ch
4.2K views

25:56
8 Best Forensics Tools In Kali Linux | Deleted Data Recovery | Ethical Hacking | FREE Tutorial
The Novice Learner
385 views

0:08
Read Learning Python for Forensics PDF Online
Bgerstner
5 views

0:06
Read Introduction to Security and Network Forensics Ebook Free
Maisi Baker
0 views
1:03
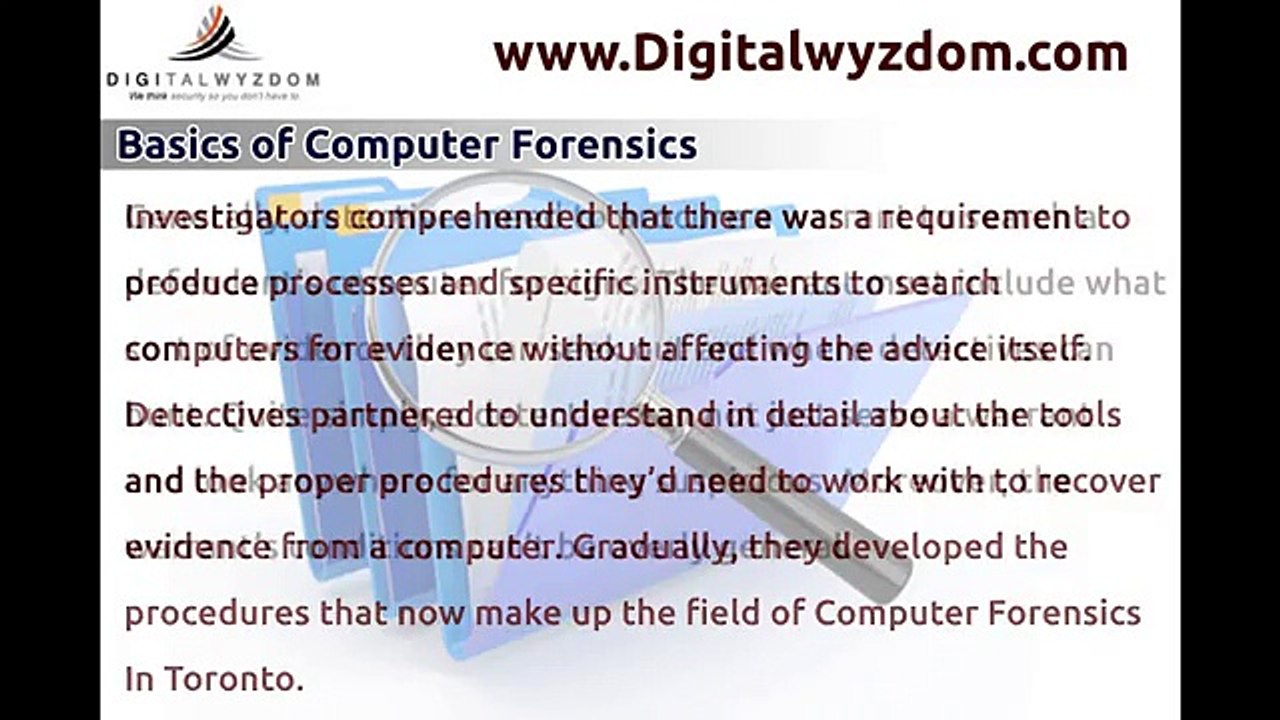
Basics of Computer Forensics
Computer Forensics
6 views

15:00
Steganalysis & Digital Forensics (Ubuntu)
Saugat.
866 views
41:12
DEFT Jam, Forensics with Autopsy- A Look Inside our CHFI Training Course
Advanced Security
2.2K views
11:55
Introduction to Computer Forensics - Intro to Steganography
David Hays
170 views

27:08
Digital Forensics Explained: Hands-On with File Recovery, Encryption & Steganography(Lecture 11)
Cipherbase technologies
110 views
0:41
PDF hidden Text #picoctf #crytography #forensics
hengki lodwig
429 views

11:13
COURSERA:CYBER SECURITY TOOLS|WEEK4 CRYPTOGRAPHY,PENETRATION TESTING& DIGITAL FORENSICS|QUIZ ANSWERS
Anand Ranjit Kumar Mukkala
3.5K views

2:33
PicoCTF - Enhance! - File Forensics
Hoplite Security
412 views

1:00
Inside the Mind of Your Computer: The Power of Memory Forensics
FDI LABS CLASSROOM
225 views

0:55
What is computer forensics? || cyber law || part 1 || part 2 is in description box
Amisha Sharma
1.2K views

3:08
How Is Steganography Used In Anti-forensics? - SecurityFirstCorp.com
SecurityFirstCorp
15 views
3:59
Learning Computer Forensics Tutorial | Steganography
O'Reilly - Video Training
1.6K views

26:52
CyGenixCTF Writeup | Web, Steganography, RE, Forensics, Crypto, OSINT, Misc
HxN0n3
660 views
58:40
CTF : Steganography | Forensics Challenges - Tools to be used - Walkthrough - English
Tech Enn
10.4K views
3:28
What Is The Role Of Steganography In Anti-Forensics? - Law Enforcement Insider
Law Enforcement Insider
29 views

7:52
How Encryption and Decryption Work in Digital Forensics? | Digital Forensic Ep.19
WsCube Cyber Security
3.3K views

15:38
Understanding IPDR: What is Internet Protocol Detail Record? - DIGITAL FORENSICS
FDI LABS CLASSROOM
5.5K views

16:23
Forensics Expert Answers Crime Scene Questions From Twitter | Tech Support | WIRED
WIRED
2.4M views
2:00
Iberia Parish crime lab enhances forensics with new DNA tech
KLFY News 10
40 views
0:56
Evolution Of Digital Forensics !
FDI LABS CLASSROOM
655 views

1:55
Penetration Testing, Incident Response and Forensics Week 1 Quiz Answer | Penetration Test
Course Fry
384 views
4:16
Cyber Security and Ethical Hacking - Steganography & Image Forensics
Turnkey IT Campus
112 views

3:06
How Do Digital Forensics Extract Data From Damaged Devices? - The Crime Reel
TheCrimeReel
2 views

0:05
Read Digital-Forensics and Watermarking: 11th International Workshop IWDW 2012 Shanghai China
Untermann
1 views

0:07
Read Computational Forensics: Third International Workshop IWCF 2009 The Hague The Netherlands
Abicht
0 views

0:17
Free Online Forensics Courses
NN IT
7 views

0:08
Download Android Forensics: Investigation Analysis and Mobile Security for Google Android PDF
Sladouph
1 views

0:08
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives PDF Online
Myrthenbaum
2 views

0:05
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives Ebook Free
Reimold
3 views
9:19
Cyber Hui Forensics Training - Lab One (Steganography)
HawaiiCyberHui
547 views

43:18
Crime Watch - Cold Case Killers (Killer Forensics)
Crime Watch
88 views

1:45:27
Day-2 of 5 Days Online Workshop on Cyber Security & Digital Forensics | Dept. of Comp. Science, AMU
Department of Computer Science, AMU
60 views

2:30:59
Day-1 of 5 Days Online Workshop on Cyber Security & Digital Forensics | Dept. of Comp. Science, AMU
Department of Computer Science, AMU
210 views

2:10:11
Day- 4 of 5 Days Online Workshop on Cyber Security & Digital Forensics | Dept. of Comp. Science, AMU
Department of Computer Science, AMU
33 views

2:15:04
Day-3 of 5 Days Online Workshop on Cyber Security & Digital Forensics | Dept. of Comp. Science, AMU
Department of Computer Science, AMU
73 views

3:31
5 Days Workshop on Cyber Security & Digital Forensics.
ACIC-MIF
176 views

2:47:15
Day-5 of 5 Days Online Workshop on Cyber Security & Digital Forensics | Dept. of Comp. Science, AMU
Department of Computer Science, AMU
141 views

1:28
1025 67 Steganography QuickStego Lab Computer and Hacking Forensics
Dev Skills
46 views

0:25
image forensics using exiftool #cybersecurity #linux #cyber #hacker #tech #ctf #pentesting
Black Bat Terminal
2.1K views

5:38
CTF Learning Series – ExifTool in Forensics
Knull CTF
47 views

1:19
Octo Digital Forensics: Cell Phone Forensic Experts
Octo Digital Forensics
1.0K views

43:14
Digital Forensics - Metadata Analysis #1 - Exiftool
itsMamu213
21.0K views

8:25
Master ExifTool: Extract Hidden Metadata - Home Lab Forensics #2
Dr. K
648 views

22:00
Exiftool Image Forensics Kali Linux 2024 - Extract Info from Images/Photos
Mr. Instruction Pointer
14.4K views

3:52
Understanding Digital forensics In Under 5 Minutes | EC-Council
EC-Council
27.8K views

14:56
Digital Forensics | Davin Teo | TEDxHongKongSalon
TEDx Talks
119.8K views