Search Results for "Data Protection with Symmetric Ciphers"
Find videos related to your search query. Browse through our collection of videos matching "Data Protection with Symmetric Ciphers". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Data Protection with Symmetric Ciphers"
53 results found

24:17
Substitution Ciphers-Caesar Cipher-Monoalphabetic Ciphers-Part 1(KTU CSE 409 Cryptography-Module 1)
KTU Computer Science Tutorials
7.7K views

20:09
Codes and Ciphers - Monoalphabetic Ciphers
Chuck Moore
1.7K views

3:26
1.4 - Block Ciphers vs Stream Ciphers (CompTIA Security+ SY0-701)
CyberMuk
507 views
9:47
Modern stream ciphers and asymmetric key ciphers
Pravisha candideyes
93 views

23:21
Basics of Cryptology – Part 9 (Modern Cryptography – Block Ciphers – Feistel Ciphers & SDES)
Cryptography for Everybody
2.1K views
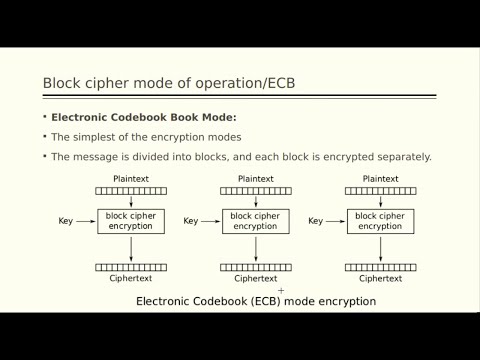
9:50
Introduction to Stream ciphers and block ciphers
AKSHARA CS
570 views
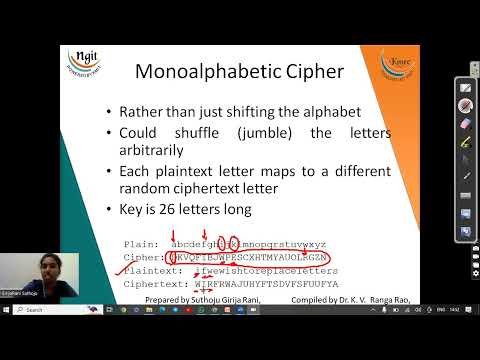
14:01
2.3.1 Traditional Substitution ciphers Caesar, Monoalphabetic and One time pad ciphers 1
ngitkmec01
267 views

0:56
Data Analyst vs Data Scientist | Difference between Data Analyst and Data Scientist | Must Watch
Analytics Vidhya
108.9K views

5:12
Big Data In 5 Minutes | What Is Big Data?| Big Data Analytics | Big Data Tutorial | Simplilearn
Simplilearn
2.1M views

11:42
Data Cleaning In Data Mining | Step by Step Data Cleaning Process | Data Cleaning | Simplilearn
Simplilearn
5.2K views

15:43
Data Science Career Path | Data Science Roadmap | Data Science | Data Scientist | Edureka
edureka!
10.9K views

3:40
Data Exploration & Types of Data Attributes | Data warehouse and data mining | lec 2.3
Engineering io
226 views

29:37
Elevating Data Fabric to Data Mesh: solving data needs in hybrid data lakes with Comcast
Trino
570 views
0:12
Data Saver Setting ||Mobile Data Saver ||Data Saver | how to enable mobile data saver #shorts
RK Raju Technology
611 views

1:49
What is Big Data | Big Data in 2 Minutes | Introduction to Big Data | Big Data Training | Edureka
edureka!
296.4K views
0:33
how to on data saving mode in vivo mobile. data kese save kre.#internet save#data save#data savemode
verma tech
26.3K views

0:58
Data Science And Data Analytics - Key Differences | Data Science vs Data Analytics | Intellipaat
Intellipaat
19.6K views

1:13
Data Entry India, Data entry services, Outsource data entry services , Offshore India Data Entry provides
Mukesh Patel
1 views

0:30
Bpo Data Entry Help, Offshore Data Entry Services, Outsource Data Entry India , Quiclk Data Entry Services
BPO Data Entry Help
53 views

2:27
Data Usage Alert Fix This 1 Minute | Apne Mobile Data Ko Kaise Bachae | Data Saver| Data Usage Alert
Mirror Of Technology
7 views

3:32
Jaldi Se le 1Gb Data Loan | Data Loan Kaise Le | How To Get Jio Emergency Data | Jio Data loan Hindi
Mirror Of Technology
3 views

3:40
instagram secret data saving trick | Cellular data on instagram | Instagram Secret Data Saving Trick | instagram data saver setting
Aslam creator
1 views

4:39
Data Data Ho Sohney Data - Saima - Pakistani Film Nagri Data Di (2004) Naseebo Lal
Bestoflollywood
47 views

0:29
Data Entry, Data Entry Services, Online - Offline Data Entry to 3Alpha Data Entry Services
3alphadataentry
106 views

9:05
Traditional symmetric key ciphers
kings Tutorial
1.4K views
6:02
Symmetric-Key Cryptography: Block Ciphers & Chaining @DatabasePodcasts
Database Podcasts
4 views

13:56
Chapter 3, part 1: Symmetric Key Crypto --- stream ciphers, A5/1, shift registers
Mark Stamp
54.2K views

1:15:57
Cryptography on Hardware - Session 5 - Symmetric Ciphers, AES Round-based
Amir Moradi
164 views

27:36
CTCrypt 2016 – Xiaoyun Wang – Bit cryptanalysis on symmetric ciphers
BIS TV
1.8K views

56:46
CYS232: Ch3 Traditional Symmetric Key Ciphers Dated 20201109 By Malek Barhoush
YUIT
415 views
21:56
DAY 08 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L2
Vidhyaashram
235 views
28:35
2.Traditional symmetric-key ciphers- PART1
VEENA RAMA SETTY
162 views
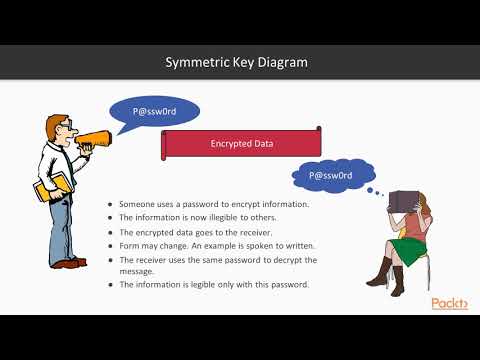
4:54
Hands-On Cryptography with Java : Symmetric Ciphers and Where They Are Used | packtpub.com
Packt
128 views
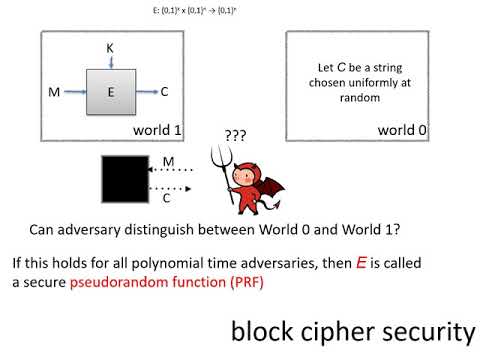
39:03
Symmetric encryption - Block ciphers
Mike Swift
601 views
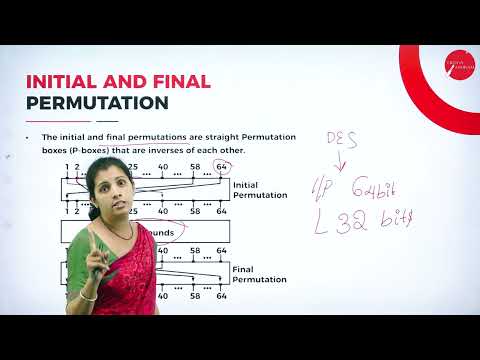
23:26
DAY 13 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L7
Vidhyaashram
137 views

28:30
DAY 07 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L1
Vidhyaashram
241 views

49:17
Network Security, Session 4: Symmetric Key Encryption - Stream Ciphers
ANSLAB
307 views

1:43
Applications Of Symmetric Ciphers - Applied Cryptography
Udacity
3.4K views
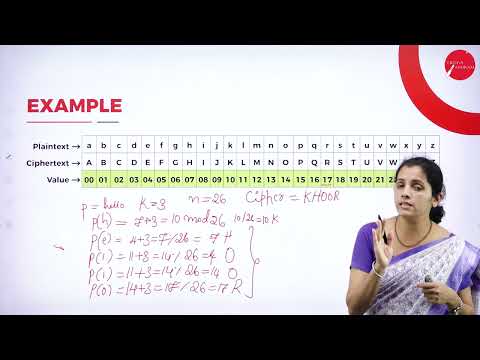
35:47
DAY 10 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L4
Vidhyaashram
205 views

9:05
Cryptography Lab 2 Ciphers and Symmetric Encryption
Level Effect
525 views
6:14
3 Symmetric and asymmetric ciphers | Computer Monk 🔴
Computer Monk
4 views

5:58
ch 2 traditional symmetric key ciphers
JSM eResource
284 views

35:50
DAY 11 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L5
Vidhyaashram
146 views
25:35
DAY 09 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L3
Vidhyaashram
109 views

9:35
Cryptography and Network Security:#8 Symmetric Key Ciphers
Shreya's E-Learning
2.3K views

33:07
DAY 12 | NETWORK SECURITY | V SEM | B.C.A | TRADITIONAL SYMMETRIC KEY CIPHERS | L6
Vidhyaashram
183 views

17:08
Network Security and Cryptography EP3 - Symmetric Ciphers (Playfair, Hill Cipher, Vigenère)
Esoterical
29 views
34:15
Discrete Mathematical Structures, Lecture 5.1: Symmetric cryptographic ciphers
Professor Macauley
2.6K views

1:02:06
Symmetric Key Cryptography Stream Ciphers in Hindi Urdu LECTURE 16
Virtual Comsats
522 views

0:43
Symmetric Ciphers - Applied Cryptography
Udacity
919 views
41:08
Digital Personal Data Protection Bill, 2022: Implications for User Privacy
NDTV Profit
2.2K views

1:00
Encryption_ The Art of Protecting Secret
Badea3
244 views

0:58
These Places Have The Cleanest Air In America
Buzz60
494 views