Search Results for "Blue Protocol"
Find videos related to your search query. Browse through our collection of videos matching "Blue Protocol". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Blue Protocol"
57 results found

2:30
Briefly describe on characteristics of the UDP(User datagram protocol)
Informative Tutorials
159 views

17:02
9 - Cryptography Basics - SSH Protocol Explained
CBTVid
43.1K views

3:45
Quantum cryptography: The BB 84 protocol (U3-02-03)
QuantumVisions
32.1K views

25:17
CS C S009 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
539 views
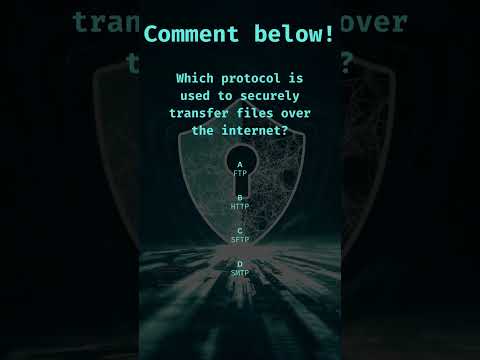
0:11
Which protocol is used to securely transfer files over the internet?
KrofekSecurity
38 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

10:00
BB84 Protocol of quantum key distribution
창하김
36.5K views

0:32
Why Did AI Crypto Coin Virtual Protocol Pump 1000%? | Shocking Crypto Rally Explained!
Coin Rishi
9.5K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

3:48
What Is A Cryptographic Protocol? - Tactical Warfare Experts
Tactical Warfare Experts
6 views

20:18
Model Context Protocol (MCP), clearly explained (why it matters)
Greg Isenberg
1.2M views

0:35
The Enigma of the Doxiadis Protocol
Zenith
634 views
0:51
NEAR Protocol Price Prediction AI Pivot Impact! #cryptonews #crypto #near
Gordon Frayne
2.9K views

17:06
Post-Quantum Key Exchange for the TLS Protocol from the Ring Learning with Errors Problem
IEEE Symposium on Security and Privacy
2.1K views

0:59
BIO protocol #bioprotocol #bioprotocolprice #bioprotocolpriceprediction 2025 #Crypto #CryptoNews
Pakistan Times
664 views

46:29
Paillier homomorphic encryption and a share conversion protocol - Federico Mazzone
De Componendis Cifris
757 views
17:11
Lesson 10: Attacks to the SSL Protocol (intypedia)
UPM
2.4K views

1:13:04
Bob Cowles: 🔑 Introduction to Cryptography and the Bitcoin Protocol 1/2 - CERN
CERN Lectures
494 views

3:15
How Does The BB84 Protocol Secure Quantum Communications? - Quantum Tech Explained
Quantum Tech Explained
13 views

5:53:10
FREE Full-Length Audiobook | The Patriot Protocol | Thriller Post-Apocolyptic #audiobook
BookTV
358.8K views

1:13
Cryptographic protocol Top # 9 Facts
Srimalui Trivedi
27 views

1:00:18
The 8th BIU Winter School: Verified Cryptographic Protocol Implementations - Karthik Bhargavan
The BIU Research Center on Applied Cryptography and Cyber Security
244 views
9:44
How Signal Instant Messaging Protocol Works (& WhatsApp etc) - Computerphile
Computerphile
521.1K views

0:12
Network Protocols #coding #artificialintelligence#network #protocol#programming#working#introduction
Information hub
203.1K views

5:24
Register Drones, Diffie-Hellman Protocol Flaw, Facebook Alerts for Attacks, and More - Threat Wire
Hak5
10.4K views

6:57
IP Security Protocol : Encapsulating Security Payload (ESP) Explained in Hindi
5 Minutes Engineering
127.5K views

2:55
Key Determination Protocol
Shailesh Shetty
433 views
![WGAN-GP & Genetic Algorithms [Side-Channel Attacks, Cryptographic Protocol Optimization]](/image/i.ytimg.com/vi/EZohUbomaiw/hqdefault.jpg)
9:40
WGAN-GP & Genetic Algorithms [Side-Channel Attacks, Cryptographic Protocol Optimization]
All About AI Tech
20 views
0:47
204 what is a cryptographic protocol?
How To Linux
49 views

3:31
The Cryptographic Protocol - what are the techniques of cryptography?
BitCoin XTreme
692 views

34:55
Episode 1 - The Protocol Paradox in Cryptography and System Security
Maitt Saiwyer
3 views

1:31:16
Lecture 1: Interactive Proofs and the Sum-Check Protocol, Part 1
MIT OpenCourseWare
97.2K views

11:09
Quantum Key Distribution (BB84 Protocol) Explained Simply | Quantum Cryptography Made Easy
Engineering_enigma
66 views

27:57
Lecture 6. The Signal Protocol (Applied Cryptography 101: Real-World Deployments)
Cryptography 101
1.5K views
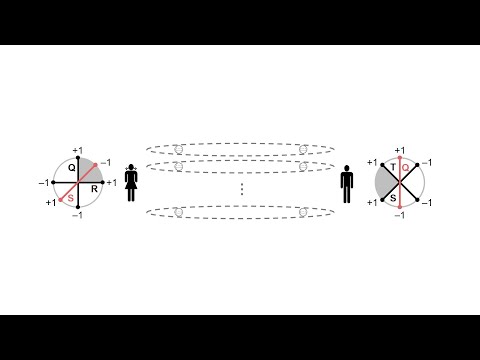
11:59
41.Quantum key distribution II: EPR protocol
Jochen Rau
892 views

6:59
19.4 Cryptographic protocol
World Gurukul way of Learning Values and Wisdom
3.6K views

10:02
S/MIME protocol in Hindi | Cryptography and Network Security
Abhishek Sharma
142.4K views

3:24
Skeng X Sparta - Protocol (Official Music Video)
Skeng
104.2M views

1:02:51
DEF CON 8 - Bennett Haselton - A protocol that uses steganography to circumvent
DEFCONConference
202 views

6:32
URGENT - Tounkara réagit au discours en anglais de Diomaye Faye et tire sévèrement sur le protocol
Senegalactu Tv
88.7K views

14:08
Low Exponent Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
11.4K views

3:03
Is The BB84 Protocol Essential For Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
14 views
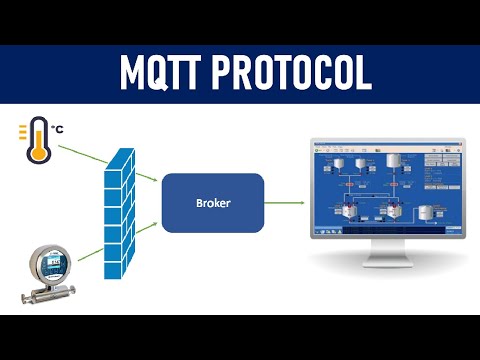
7:19
What is MQTT Protocol ? How it works ? | 2022
IT and Automation Academy
178.4K views

5:43
How To Hide A Message In An Image (Steganography) Using Linux Terminal | The Protocol S
The Protocol S
140 views

6:43
Kerberos Authentication Protocol 🔥🔥
Perfect Computer Engineer
198.5K views

1:07:03
Steve Girvin: Secure Communication in a Quantum World – BB84 Protocol
Yale University
4.3K views

1:01
Symmetric Cryptography - AES Encryption - Exa Protocol #shorts
Exa Protocol
96 views

9:24
Kerberoes protocol in Cryptography and Network Security #cryptography #education #computerscience
Lab Mug
1.8K views

16:34
Graciela Bachu: The BB84 Quantum Cryptography Protocol (TSI)
Talaria
221 views
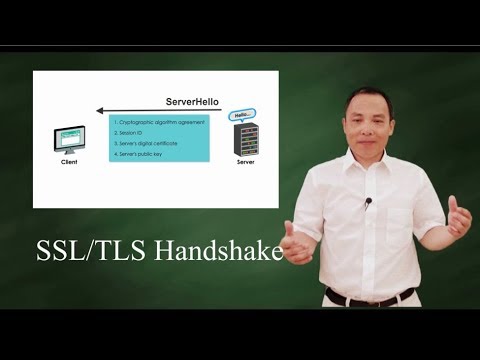
5:04
SSL/TLS handshake Protocol
Sunny Classroom
496.8K views

1:05
Blue Protocol (Star Resonance) arrive en 2025
Tiro & Antituis 🎮
2.7K views
9:10
BLUE PROTOCOL : La Renaissance Qui Va Tout Changer !
Hormain
3.1K views

2:00
Tráiler de anuncio de Blue Protocol: Star Resonance
3djuegos
6.6K views

2:16
Tráiler de anuncio de Blue Protocol - The Game Awards
3djuegos
397 views

2:16
Blue Protocol: Das neue MMO von Amazon zeigt seinen ersten Trailer
GameStar
3.3K views
0:49
Die Entwickler von Blue Protocol: Star Resonance zeigen den Charakter Editor
MeinMMO
2.2K views

1:44
Blue Protocol: Star Resonance präsentiert bunte Charaktervielfalt im neuen Release-Trailer
MeinMMO
35.7K views