Search Results for "cryptographic primitives"
Find videos related to your search query. Browse through our collection of videos matching "cryptographic primitives". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cryptographic primitives"
50 results found

58:37
s-7: Cryptographic Primitives I
IACR
530 views

2:12
The Power of Cryptographic Primitives
AtlasTV
810 views
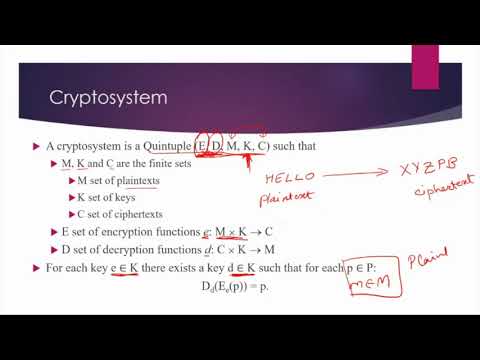
36:33
Cryptographic Primitives
Dr. Shweta Bhandari
1.4K views

1:19:50
#6 cryptographic primitives - encryption ciphers
ralienpp
321 views

22:32
Watermarking Public-Key Cryptographic Primitives
IACR
764 views
1:02:59
s-185 Cryptographic Primitives
IACR
303 views
21:17
"Design of Symmetric-Key Primitives for Advanced Cryptographic Protocols" (FSE 2020)
COSIC - Computer Security and Industrial Cryptography
139 views
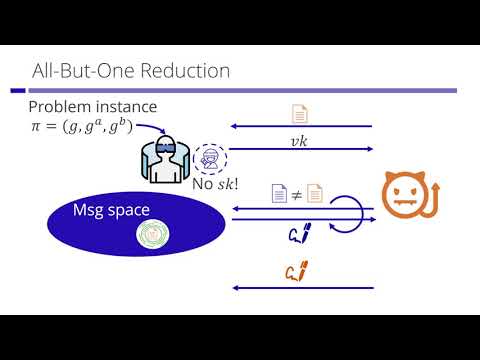
20:44
Equipping Public-Key Cryptographic Primitives with Watermarking (or: A Hole Is to Watermark)
IACR
185 views

21:17
Design of Symmetric-Key Primitives for Advanced Cryptographic Protocols
IACR
225 views

43:58
Tools and Techniques for Assessing the Security of Cryptographic Primitives - Maria Eichlseder
UWindsor CS Colloquium
63 views
3:23
CryptXplorer|AI/ML Framework for Identifying Cryptographic Primitives in Firmware|SIH 2025 Prototype
Pradyumn Tripathi
38 views
2:06
Block Cipher Primitives
Udacity
1.1K views

12:42
Blockchain | Lecture 2 | Cryptography Primitives
Dr. Bipin Kumar Rai
736 views

2:33
The Primitives - Crash
theprimitivesVEVO
5.2M views

55:42
Symmetric-Key Primitives
RSA Conference
53 views

8:52
Cryptography Primitives Explained | Symmetric vs Asymmetric vs Hashing with Real-World Use Cases
Gettobyte
172 views
34:22
Out of Oddity -- New Cryptanalytic Techniques against Symmetric Primitives Optimized for Integr...
IACR
352 views

1:21:21
Winter School: Advanced symmetric primitives - Thomas Ristenpart
Bar-Ilan University - אוניברסיטת בר-אילן
313 views
30:54
Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks
USENIX
1.3K views
44:53
Interesting primitives/applications of Cryptography | O S L Bhavana | CSAUSS17
CSAChannel IISc
75 views
18:20
Perfect Trees: Designing Energy-Optimal Symmetric Encryption Primitives
IACR
77 views

56:37
Dan Boneh: Blockchain Primitives: Cryptography and Consensus
TechCrunch
126.6K views

0:41
Quiet Primitives Steering Crypto’s Long Game
Crypto Secrets
248 views

0:49
What are the Cryptography Primitives?| IGNOU TEE | Competitive Exams | CBSE
ParminderComputerSuccess by Parminder Kaur
86 views

0:06
Read Integrity Primitives for Secure Information Systems: Final RIPE Report of RACE Integrity
Chikovani 1981
1 views

10:24
Primitive Technology - Finding Snake By Girl in forest // Des nouvelles méthodes primitives pour vivre
al-khaliji-tv
12 views

0:55
Les fausses constuctions primitives
LOOKY
2.6K views

7:09
AutoCAD 3D Modelling - Creating 3D Primitives
autocadvids
404 views

3:41
Python Basics Tutorial Cryptography Hazmat Primitives || Data Encryption
Python Basics
1.1K views

3:10
pip install cryptography hazmat primitives ciphers
CodeFlare
257 views

49:30
R11. Cryptography: More Primitives
MIT OpenCourseWare
10.4K views
16:37
Minicrypt Primitives with Algebraic Structure and Applications
IACR
427 views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

0:34
How To Pronounce Cryptographic🌈🌈🌈🌈🌈🌈Pronunciation Of Cryptographic
Isabella Saying
33 views

0:34
Cryptographic | CRYPTOGRAPHIC meaning
Word Mastery Channel
0 views

0:02
How to pronounce Cryptographic / Cryptographic pronunciation
Raccoon Teaches You
48 views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views
2:24
OWASP TOP 10 - Sensitive Data Exposure / Cryptographic failures
WhiteHats
3.2K views

23:38
The Price Of Active Security In Cryptographic Protocols
Fidelity Center for Applied Technology (FCAT®)
31 views

6:31:26
Cryptographic Ledger Database, Analysis & Applications in Decentralized Blockchain & Financial World
HKEBA
71 views

37:26
A complete overview of SSL/TLS and its cryptographic system
TECH SCHOOL
136.0K views

16:03
A Cryptographic Implementation: Hybrid Encryption
Luciano Scarpaci
25 views

12:21
Rapid Prototyping of Cryptographic Systems on Chip - By Dr. Issam W. Damaj
Dr. Issam Damaj
68 views

0:31
CS8792 / Cryptographic and network security / Unit -3 (30 MCQ ) important Questions with answers..
Lincy's Style
416 views

29:55
Cryptographic hash function: Introduction
Introduction to Cryptology
3.7K views

6:06
Unplugged: The show. Part 8: Cryptographic protocols
UC Computer Science Education
14.4K views

0:47
The Enigma Machine: Cryptographic Innovator
Bored Sapien
318 views
7:57
griet-it-2012- a cryptographic technique for heterogenous sensor networks.wmv
Maruti Kumar
18 views
Page 1 Next