Search Results for "Secure Operations"
Find videos related to your search query. Browse through our collection of videos matching "Secure Operations". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Operations"
52 results found

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

7:11
What is BODMAS Rule | PEMDAS | Easy Way | Order of Mathematical Operations | Order of Operations
Epic Learning
35.5K views

0:07
“Increase your business operations with Paymaxima secure and innovative online payment method”.
Fatima Tahir
11 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views

11:19
Rounding and Order of Operations Used in Significant Figures
Melissa Maribel
122.5K views

1:19
Ces 3 opérations sont les plus pratiquées par les stars arabes!
Wada7 France
1.3K views
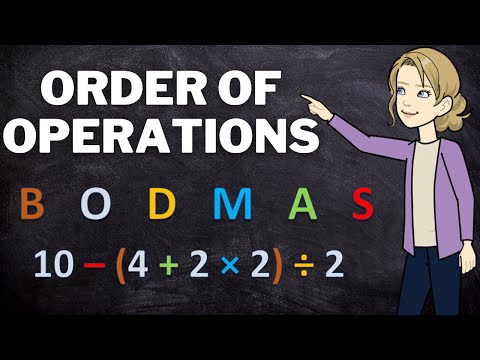
10:49
Order of operations using BODMAS
Mathematics with Marlien
242.2K views

1:51
Así monitoreamos el estado de tus activos desde nuestro NOC (Network Operations Center): NSIT
NSIT
4.8K views

1:00
"Why are you quitting?" Special Operations Candidates conduct pre-dive training
SOCOM Athlete
93.2M views

46:24
Cryptography | Cipher Block Modes of Operations | Christ OpenCourseWare
Christ opencourseware
517 views

27:23
Steganography on Red Team Operations: Beyond CTF by Vinicius Vieira (v1n1v131r4)
Red Team Village
604 views

7:53
Block Cipher Mode of Operations in Tamil | Cryptography and Cyber Security in Tamil Unit 2 | CB3491
4G Silver Academy தமிழ்
23.1K views

52:15
CISA EXAM PREP - Domain 4A - IS Operations
Inside Cloud and Security
1.1K views

32:36
Asymmetric Cryptography: RSA Operations and Mathematics
__cdeclan
26 views
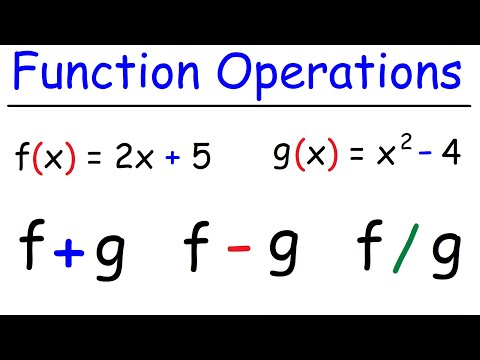
7:10
Function Operations
The Organic Chemistry Tutor
1.7M views

55:41
Leaks and Links: Unmasking Iran’s Cyber Operations Through Breached Banks and Telegram Networks
District 4 Labs
48 views

18:31
CISSP Lecture 41 CISSP Security Operations
URDUIT Academy
2.4K views

2:05
CIRCULAR QUEUE DATA STRUCTURE ,ENQUEUE, DEQUEUE ,PEAK/FRONT, REAR Operations in 2 Minutes.
Code Scribbles
281 views

11:51:18
Security Operations (SOC) 101 Course - 10+ Hours of Content!
The Cyber Mentor
195.1K views

9:37
Cryptography and Network Security: #3 Operations in Zn and Properties
Shreya's E-Learning
2.6K views
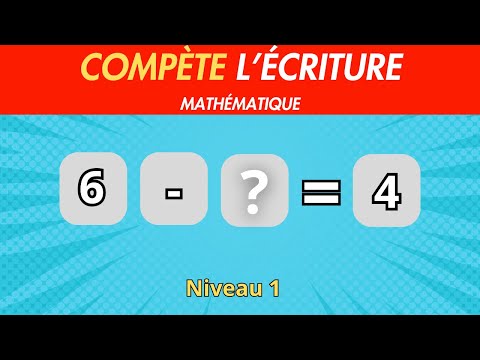
13:10
Quiz Mathématique pour CP, CE1, et CE2 | Complète les opérations Mathématique -1
Quiz Quiz
5.3K views
3:16
How Does Cryptography Protect Data In Cyber Operations Units? - The Frontline Guardians
The Frontline Guardians
0 views

7:45
Operations on Regular Languages
Neso Academy
857.5K views
11:30
Pokrovsk Endgame | Kharkiv-Belgorod Operations Expanded - 18 Sqkm Captured
Weeb Union
65.9K views

6:20
How to use BODMAS (Order of Operations)
Cognito
602.1K views

22:23
Basic Properties of Galois Fields (GF) polynomial operations over Galois Fields
RTU Wallah
33.0K views

14:07
CISSP Made Easy Ep 4 | Cryptographic Modes of Operations
Rashid Siddiqui | CISSP, CCSP and Related Stories
613 views
13:30
Operations on Circular Queue | Data Structures Tutorial
Naresh i Technologies
167.8K views

17:58
Logic in mathematics - meaning, operations, truth table, logical reasoning and connectives
Myschool
37.2K views

26:39
AES S-Box | Types of S-Box | AES S-Box Operations - GF Inversion and Affine Transformation
AIBM | Secure Community
584 views

11:42
Introduction to Symmetry Operations and Point Groups
CCDCCambridge
203.3K views

12:51
OPERATIONS ON SETS - Union, Intersection, Difference, and Complement of a Set | Ms Rosette
Ms Rosette
487.1K views

12:14
Applied Cryptology 4.1: Block Cipher Mode of Operations - Motivation
Cihangir Tezcan
631 views

9:40
Math Antics - Order Of Operations
mathantics
9.1M views

8:03
DG ISPR Press Briefing on Flood Relief and Rescue Operations | ISPR
ISPR Official
11.3K views

32:51
Iran integrates influence and cyber operations
N2K Networks
95 views

0:59
CIRCULAR QUEUE Data Structure ENQUEUE,DEQUEUE,PEAK/FRONT,REAR Operations in 60 seconds
Code Scribbles
22.7K views

4:50
Understanding Cryptographic Modes of Operations - ECB: The Electronic Codebook Mode Explained
securityconceptsnotes
470 views
0:59
How Did NSA Operations Transform During Desert Storm? 🌍💻
Security Unfiltered Podcast
445 views

0:31
Pakistan Army Eliminates 5 Terrorists, Arrests 2 in KP Operations 🇵🇰🔒
TNN TV
618 views

1:48
Administrator says it wants to secure a buyer by the end of the year
ABC NEWS (Australia)
1.9K views

1:32
Northern NSW operation secures 101 weaners from big Elders yarding at Yea
Stock and Land
248 views
Page 1 Next