Search Results for "Encryption schemes"
Find videos related to your search query. Browse through our collection of videos matching "Encryption schemes". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Encryption schemes"
50 results found
53:07
session-28: Cryptanalysis of authenticated encryption schemes
IACR
234 views

4:50
Compact and Tightly Selective-Opening Secure Public-key Encryption Schemes
IACR
66 views
19:01
FHE Lecture 04: Somewhat Homomorphic Encryption Schemes over Integers (SHEOI) : Asymmetric Crypto
Maths Submarine
63 views
26:49
FHE Lecture 03: Somewhat Homomorphic Encryption Schemes over Integers (SHEOI) : Symmetric Crypto
Maths Submarine
116 views

12:49
Lecture 3 (Part3) : Classical Encryption Schemes : The Vigenere Cipher
The-Planet1729
113 views

20:17
Generate Mixed Encryption Alphabets Using ACA Keying Schemes
Cryptography for Everybody
654 views

49:45
Data Encryption Schemes (Ch 2 Part 1)
Lecture Notes of Information Technology
137 views

38:27
An attempt to revive Knapsack-based public-key encryption schemes
Jean Martina
157 views

1:25:26
Winter School: Authenticated encryption schemes and Misuse-resistance - Thomas Ristenpart
Bar-Ilan University - אוניברסיטת בר-אילן
518 views

6:56
Accelerating Lattice based Proxy Re Encryption schemes on GPUs - Short version
CANS - Cryptology and Network Security
65 views
21:19
Analysis of Multivariate Encryption Schemes: Application to Dob
IACR
305 views
21:44
PQCrypto 2020 | Multivariate Encryption Schemes... • T. Yasuda, Y. Wang, T. Takagi
PQCrypto 2020
1.4K views
1:13:43
Candidate iO from Homomorphic Encryption Schemes
Simons Institute for the Theory of Computing
679 views

0:48
Wireless Body Area Network | Encryption Techniques for WBAN | Energy-Efficient Schemes for WBAN
Techsparks
69 views

5:33
Lecture 1: Encryption Schemes
Alptekin Küpçü - Cryptography & Cyber Security
1.1K views

1:11
What is Encryption? Explain Encryption, Define Encryption, Meaning of Encryption
Audioversity
261 views

1:17
Truth About Pump & Dump Crypto Schemes with @talkswithrochit | Deepak Wadhwa | #pump #dump #money
DeepakWadhwa.Official
1.0M views
24:00
PQCrypto 2023: Session VI: Overbeck’s attack and Twisted Gabidulin-based schemes (Ilaria Zappatore)
QuICS
74 views
1:10:10
Cryptanalysis on Public-Key Schemes (Asiacrypt 2024)
IACR
310 views

0:36
Fake and schemes, yet their hearts keep being torn together.💔 #1e809i #honeyreels #cdrama #drama
KISS CHU RECAP
15.8M views
52:41
Secret Sharing Schemes
nptelhrd
21.2K views
0:24
Ranking Kyle Busch's M&M Primary Paint Schemes #nascar
The SuperSquad
33.1K views

43:07
On Attacking Hash functions in Cryptographic schemes
Simons Institute for the Theory of Computing
962 views
![[CSC587] Comparison of DNA Cryptography Schemes](/image/i.ytimg.com/vi/mCoC1WyVcN8/hqdefault.jpg)
8:04
[CSC587] Comparison of DNA Cryptography Schemes
Term Project Videos in Dr. Manki Min's Classes
1.5K views

12:39
Digital Signature schemes RSA | Cryptography and System Security
Ekeeda
216 views
3:30
Visual Cryptography Schemes for Encoding of Secret Image - PASS Project MSc
Pass Tutors
1.3K views

52:13
Leonard Schild - "Lattice-Based Cryptography: Signature & KEM Schemes" (PQCSA summer school 2025)
COSIC - Computer Security and Industrial Cryptography
40 views

25:11
Text Steganography Concealment through Dark Colour Schemes
deXsym
12 views
7:06
Evaluation Criteria for Visual Cryptography Schemes via Neural Networks
王云超
62 views

28:49
tradeoff cryptanalysis of password hashing schemes dmitry khovratovich alex biryukov johann großschä
Adrian Crenshaw
394 views

0:36
Full of lies and schemes, but they still fall for each other.🥹 #1e809i #honeyreels #cdrama #drama
Snap Recap
16.4M views
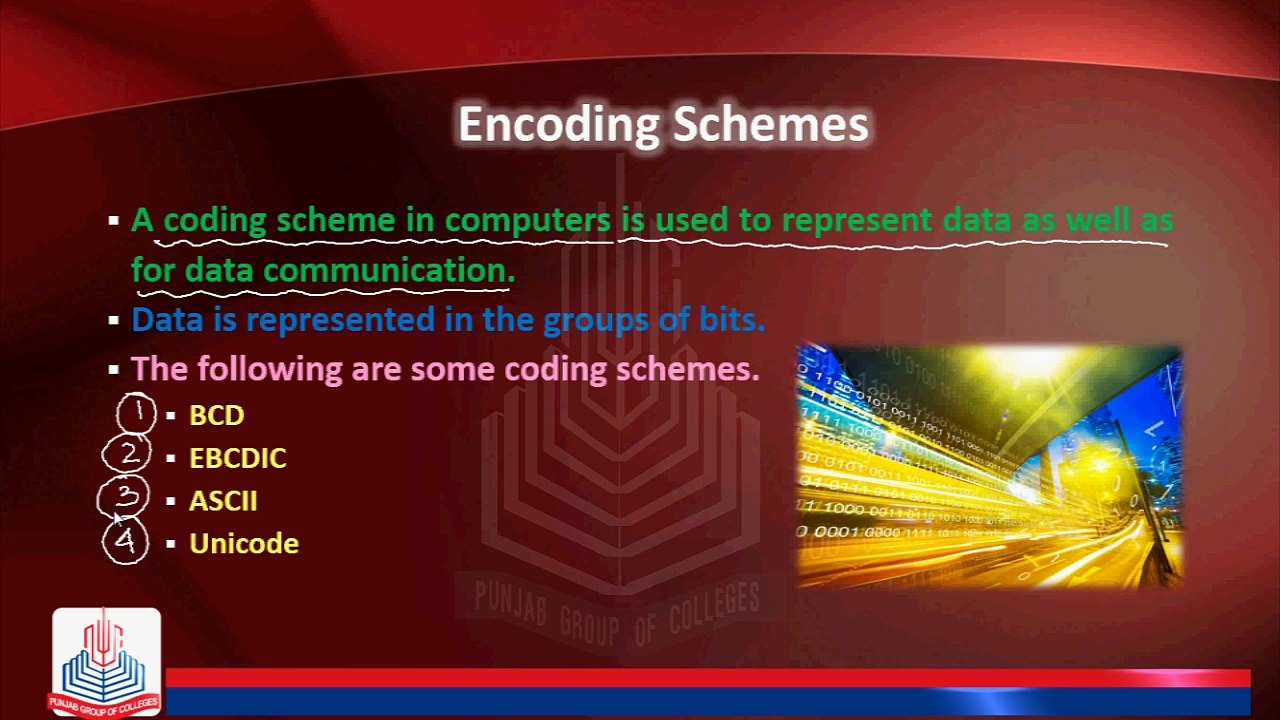
13:33
Encoding Schemes
Punjab Group Of Colleges
4 views

0:06
Read Digital Signature Schemes: General Framework and Fail-Stop Signatures (Lecture Notes in
Lwieser
3 views

5:10
Ponzi Schemes: What they are and how not to fall for one
TheNewsMinute
17 views

58:56
🚓 Danger Ahead (1935) | Smugglers, Schemes & Fast-Talking Reporters 🕵️♂️ #fullmovie #classicmovies
Just-Trending
7 views

0:58
Welfare Schemes’ Deadlines Advanced Ahead Of 2024 LS Polls & Other Headlines | News Wrap @8 AM
Hindustan Times
4.3K views

0:30
Post-quantum cryptography refers to new cryptographic schemes designed to
Peace Growba
53 views

19:12
Public-Key Identification Schemes Based on Multivariate Quadratic Polynomials
IACR
1.1K views

22:07
Multivariate-quadratic signatures II -- MQ-based identification schemes
Tanja Lange: Post-quantum cryptography
485 views

16:13
Side Channel Attacks on Post Quantum Signature Schemes based on Multivariate Quadratic Equation
IACR
288 views

9:47
Ponzi scheme explained simply Urdu Hindi _ How pyramid scheme works_ _Ponzi schemes India Pakistan
Dr Muhammad Farooq Buzdar
61 views

58:51
Crytanalysis of Symmetric key schemes using classical and quantum techniques
Get Masudur
45 views
10:46
Boosting the Security of Blind Signature Schemes
IACR
254 views

26:19
Identity-Based Aggregate and Multi-Signature Schemes Based on RSA.
IACR
704 views
21:37
Beyond quadratic speedups in quantum attacks on symmetric schemes
IACR
213 views

2:28
Debunking Pyramid Schemes #ethereum#Crypto#Blockchain#CryptoUpdate#AIBlockchain#USDT
Iztoch
8 views

1:02:05
s-8: SCA of Symmetric-Key Schemes
IACR
300 views
2:30
Modi's high tea talks of poor in all schemes, no word on Maharashtra
Inkhabar
1 views

0:07
Read Introduction to Affine Group Schemes (Graduate Texts in Mathematics) Ebook Free
Anblokvoort
4 views

0:05
Download Model-based Fault Diagnosis Techniques: Design Schemes Algorithms and Tools PDF Free
Bjerre
4 views
Page 1 Next