Search Results for "using keyword algortihm in information security"
Find videos related to your search query. Browse through our collection of videos matching "using keyword algortihm in information security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "using keyword algortihm in information security"
50 results found

1:06
Keyword Research Tools - Best Keyword Tools - Multiple Keyword Research Tools
wallacelopez2823
1 views

1:19
Keyword Research Tool - Best Keyword Tools - Multiple Keyword Research Tools
wallacelopez2823
1 views

0:27
Keyword Elite - Keyword Elite Software - Keyword Elite ...
BPT2008
10 views

8:05
KEYWORD ELITE 2.0 (Keyword Elite 2.0) "Keyword Elite 2.0"
Richard Jameson
2 views

0:15
Simple python caesar cipher #python #script #programming #encryption #code #cipher #algortihm
Taavet X
2.3K views

12:19
Keyword Research Strategy: How to Do Keyword Research, Tips, Tools & Examples
WsCube Tech
343.9K views
![Keyword Research Tool Cracked - keyword research tools seo [2015]](/image/s2.dmcdn.net/v/93Nbz1e0SxSOa9iJb/xx720.pagespeed.ic.FEtmIGaUU9.jpg)
1:50
Keyword Research Tool Cracked - keyword research tools seo [2015]
Darren Alzaman
25 views

0:56
Top Keyword Search tools| Best keyword search tools
Top information
3 views

1:06
Best keyword research tools for youtube | Free keyword research tools
Accurate Data
5 views

0:30
Keyword Tool, Keyword Research Tool
kcompetite1
1 views

2:09
Longtail Keyword Research Software Uses Google Autosuggest-win Or Mac | Longtail Keyword Research Software Uses Google Autosuggest-win Or Mac
DarinGaskell
5 views

2:06
Micro Niche Finder Keyword Software | Micro Niche Finder Keyword Software
JenniferSkiba
7 views

0:15
Elements of Information Security #shorts #security #information #knowledge #facts #education
Educryst
3.1K views

6:54
What is Information Security ? | Information Security Explained in 5 mins | Great Learning
Great Learning
54.6K views
5:12
What is Information Security || Introduction to Information Security Tutorial in urdu/hindi
A Z Computing
66.0K views

3:10:22
Certified Information Security Manager, CISM, Course 01, Information Security Governance,
Open Learning
108.6K views

0:15
Download Legal Issues In Information Security Jones Bartlett Learning Information Systems Security Assurance Pdf
Ogiemaryanti
5 views

0:15
Download Legal Issues In Information Security Jones Bartlett Learning Information Systems Security Assurance Series pdf
Ogiemaryanti
2 views

2:59
Information Security Project output - Information security Project
Academic College Projects
2 views

0:17
PDF Download Electronic Healthcare Information Security Advances in Information Security PDF Online
Choaib15omran
1 views

0:16
Read Electronic Healthcare Information Security Advances in Information Security Ebook Free
Abdur Jagot
0 views
![[PDF] Electronic Healthcare Information Security (Advances in Information Security) Popular](/image/s2.dmcdn.net/v/Hg3Wn1e9-WYLu6Q99/x720)
0:27
[PDF] Electronic Healthcare Information Security (Advances in Information Security) Popular
Biel Payton
1 views

6:14
Difference between Hash and MAC in Information Security | Comparison | Information Security Lectures
Easy Engineering Classes
10.7K views

1:53
What is Information technology?, Explain Information technology, Define Information technology
Audioversity
66.2K views

0:56
Information Technology – All About Information Technology - What Information Technology means
ComputeWorld
1 views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

10:19
#2 Security Approaches and Principles or Goals of Security- Cryptography |Information Security|
Trouble- Free
99.1K views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

5:30
What is security , information security and cyber security
Noor_khan official
3 views

9:43
Information Security (IS) Vs Cyber Security (CS) || Security Goals
Simple & Effective Learning
735 views

2:46
Decrypt using a keyword based transposition cipher
OCLPhase2
65.6K views

3:05
Substitution Cipher using a Keyword
Wellington Computing Channel
25.6K views
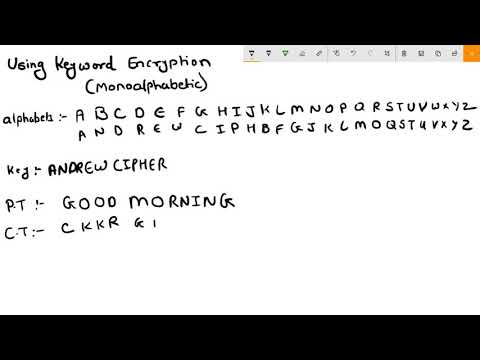
3:48
Using Keyword Cipher Technique | Mono-alphabetic
Ketul Patel
15.8K views

2:21
Keyword Research Tools - Using Market Samurai
AlaisterLow
19 views

2:36
Encrypting using a keyword-based transposition cipher
OCLPhase2
76.7K views

5:50
Using the Index of Coincidence to Determine Vigenère Keyword Length
Taylor Gibson
19.6K views

13:16
USENIX Security '22 - Constant-weight PIR: Single-round Keyword PIR via Constant-weight Equality
USENIX
423 views

10:22
INFORMATION SECURITY( HINDI).WHAT IS CRYPTOGRAPHY AND HOW IT WORKS TO SECURE YOUR INFORMATION.(ICT)
Computerprime
2.3K views

54:30
Designing an Information Architecture to Support Cyber Security and Information Assurance
Tech
213 views
![[PDF Download] Information Assurance: Security in the Information Environment (Computer Communications](/image/s1.dmcdn.net/v/D7aRX1cldHGr_Ey5g/xx720.pagespeed.ic.0AzhZq3dUt.jpg)
0:05
[PDF Download] Information Assurance: Security in the Information Environment (Computer Communications
Donammis42
1 views
![[PDF Download] Managing Risk In Information Systems (Information Systems Security & Assurance)](/image/s2.dmcdn.net/v/DB1S81e0J9e8R5SHb/xx720.pagespeed.ic.B6QP-QHvYN.jpg)
0:07
[PDF Download] Managing Risk In Information Systems (Information Systems Security & Assurance)
Zqleukji
1 views

0:07
Read Information Assurance: Security in the Information Environment (Computer Communications
Tegroothulsens
1 views

0:06
Read Information Security: Policy Processes and Practices (Advances in Management Information)
Abazasdze
0 views

0:07
Read Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Tsereteli Lia
0 views

0:05
Read Information Assurance: Security in the Information Environment (Computer Communications
Hecke
0 views

0:08
Read Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Bbuhler
0 views

0:08
Read Trusted Recovery and Defensive Information Warfare (Advances in Information Security)
Ungers
1 views
Page 1