Search Results for "user access control"
Find videos related to your search query. Browse through our collection of videos matching "user access control". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "user access control"
50 results found

5:30
Rodent control | Pest Control service | rat control | Termite control | Indian Pest Control | Bedbug Control | Pest Control Delhi NCR | Pest Control Noida U. P. | Pest Control Haryana
rkhan71in
3 views

0:51
Blue Pest Control | Bed Bug Control in Norbury London | Mice Control in London | Rat Control | Cockroach Control
Blue Pest control
6 views

1:06
Fly Control, Pest Control , Termite Control, Pest Control in Delhi NCR, cockroaches control service
rkhan71in
1 views

0:46
Pest Control | Termite Control | Rodent Control | Indian Pest Control | Mosquito Control
rkhan71in
3 views

3:35
Silverfish control | bedbug control | All Pest Control Service | Pest control in India | Indian Pest Control
rkhan71in
1 views

0:31
ESSL Js32 access control password programming system #essl #access #control
NF CCTV
3.8K views

5:00
Access Control Security Explained | Types of Access Control Systems
Heimdal®
4.8K views

7:39
Role-based access control (RBAC) vs. Attribute-based access control (ABAC)
IBM Technology
127.6K views

0:25
Access Control System Wiring Diagram | access control system installation
Electrical genius
148.2K views

8:12
Door access control system |How to install Access control system |Secureye B4CB installation /Wiring
Technical GuideWala
5.3K views

5:19
Learn the Basics of Access Control in this Video: Access Control 101
Security Camera King
151.9K views

5:23
Pest Control | Termite Control | Rodent Control | Indian Pest Control
rkhan71in
12 views

5:17
How To Install Access Control Access Door Lock How Configuration Multi Star Smart Door Lock
nature & future tech
203.5K views

1:29
Biometric Access Systems-Q2 Fingerprint Access Control
ZakariasNordstrom
304 views

0:21
IRCTC User Id & password kaise banaye Hindi #How to create IRCTC user is & password
BIKASH 4888
3.1M views

14:01
VB.NET Creating Login with Admin & User (User Level)
Codinger Tutorial
14 views

8:22
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
8 views

5:39
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
1 views

12:23
AIAG Control Plan (V1, 2024) | Types of Control Plan | Benefits of Control Plan |
Quality HUB India
17.6K views

11:19
Goose, Control Control Control
Le Soir
8 views

1:28
Control cancer book | control cancer ebook | control cancer
Don Paent
20 views

6:32
Mass shootings reignite gun-control debate in United States | Gun Control Debate | How Do We Fix America's Gun Control Problem? | Democratic Candidates Debates in United States Of America
Fun Doze With Me
4 views

8:26
Control, control, control 3D3
Brumail
17 views

13:42
Control Your Mind, Control Your Life : Jesus | How to control your mind | Jesus Speaks
Jesus Speaks
8 views

13:50
Solutions Architect Interview - Limiting User Access (with Salesforce SA)
Exponent
5.0K views
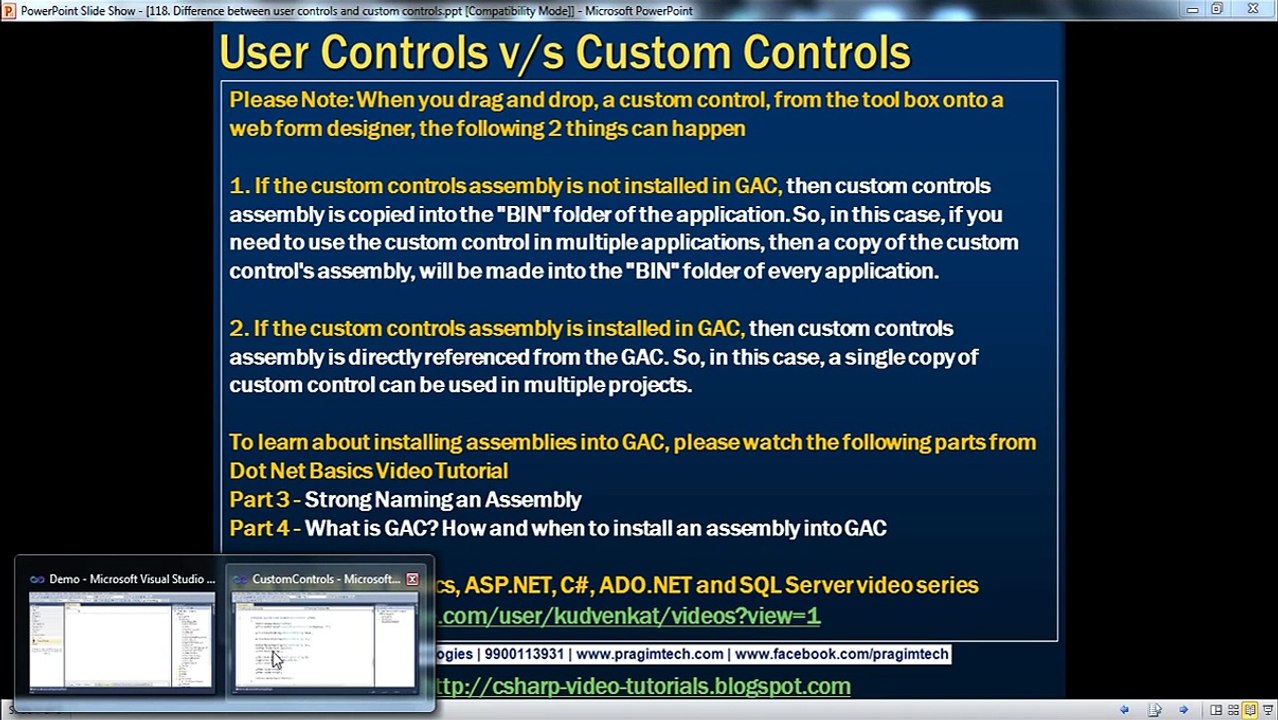
17:25
User Controls vs Custom Control
technofranchise.com
17 views

1:00
Pre launch access: unboxing PS5 Access Controller from Sony! #shorts
86hands
10.5M views

0:30
UniFi Access. Replacing old system with two Enterprise Access Hubs. #ubiquiti #accesscontrol
YesTechie
110.6K views

1:27
You need Permission to access & request access
ABC of Knowledge, A family of Rahmat E Alam
163.6K views

0:41
you need access good drive | Goggle drive request access problem fix #googledrive #shorts
Basics About System
79.6K views

52:34
SA: SQL Server Encryption from Access by Susan Pyne. Q&A with Ben Clothier - Access with SQL Server
AccessUserGroups.org
778 views
![Microsoft Office Access 2010 Key Gen [microsoft office access 2010 tutorial pdf]](/image/s2.dmcdn.net/v/8zc0E1e98ooN1ZWKi/xx720.pagespeed.ic.1wyg8YbTNb.jpg)
1:20
Microsoft Office Access 2010 Key Gen [microsoft office access 2010 tutorial pdf]
Devin Dieujuste
88 views
![[PDF Download] MathXL Standalone Access Card (6-month access) [PDF] Full Ebook](/image/s1.dmcdn.net/v/DGgXd1cms4bnMfJHf/xx720.pagespeed.ic.J7vuwIHVdb.jpg)
0:05
[PDF Download] MathXL Standalone Access Card (6-month access) [PDF] Full Ebook
Gerloza241
11 views

0:08
PDF Access to Health Plus MasteringHealth with eText -- Access Card Package (13th Edition)
ConcettaCaffertyPamella
7 views
![[PDF] Access 2016 For Dummies (Access for Dummies) Popular Colection](/image/s2.dmcdn.net/v/HGztL1e9l53xLGn2J/xx720.pagespeed.ic.UNz-1LYwo5.jpg)
0:29
[PDF] Access 2016 For Dummies (Access for Dummies) Popular Colection
Heatherskoa
8 views

1:39:05
Vascular Access Demonstration - Femoral Access - By Dr.M.Srinivas Rao
TeluguOneTV
386 views

4:34
How To Use Microsoft Access - How To Use MS Access
accesstrainingdvd
4 views

4:08
Basics of Access Control
Kantech Support
326.8K views

21:16
NSDI '20 - TimeCrypt: Encrypted Data Stream Processing at Scale with Cryptographic Access Control
USENIX
924 views

28:14
ACCESS CONTROL SYSTEM BASICS PART 1 OF 5 ENGLISH
L&P RENEWABLE SYSTEM INTEGRATOR
3.3K views

5:48
Access Control Models: An Overview of the Four Main Types
GetSafeAndSound
31.1K views

0:21
How to wire an access control system Quick & Easy Guide #accesscontrol #shortsfeed
Electrical genius
137.5K views

0:48
Card + Pin Password | Access Control Reader | 8019619680 |SA-32 | #accesscontrolinstallation #essl|
Right Vision Security Systems
79.8K views

8:47
Essl JS-32E Standalone Access control Power supply, EM Lock & Exit switch Wiring connection
TECHLOGICS
166.0K views
![[Part I] Bug Bounty Hunting for IDORs and Access Control Violations](/image/i.ytimg.com/vi/BfbS8uRjeAg/xhqdefault.jpg.pagespeed.ic.b8-iPWgdqS.jpg)
1:33:18
[Part I] Bug Bounty Hunting for IDORs and Access Control Violations
rs0n_live
81.6K views

12:32
Intro to Access Control: Diversified Keys, RSA, Asymmetric Encryption, & Other Smart Card Security
SchlageSecurity
6.2K views

11:26
CISSP Domain 5 Review / Mind Map (1 of 2) | Access Control Overview
Destination Certification
56.1K views

5:41
How Access Control Systems Work | Point Monitor Corporation
Point Monitor Corporation
53.8K views

30:04
CCT 022: Access Control Types (CISSP Domain 5) #shongerber
CISSP Cyber Training - Shon Gerber
25 views

0:36
CyberSecurity Definitions | Mandatory Access Control
Relative Security
1.9K views