Search Results for "transposition techniques in cryptography with examples"
Find videos related to your search query. Browse through our collection of videos matching "transposition techniques in cryptography with examples". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "transposition techniques in cryptography with examples"
50 results found

12:09
Keyless and Keyed Transposition techniques | Types of transposition techniques in Cryptography
Abhishek Sharma
169.7K views

16:34
Rail Fence and Row Transposition cipher techniques | Types Of Transposition Techniques
Abhishek Sharma
352.9K views

12:06
TRANSPOSITION TECHNIQUES || RAIL FENCE TECHNIQUE || COLUMNAR TRANSPOSITION -- NETWORK SECURITY
t v nagaraju Technical
11.8K views

12:47
06-Transposition Techniques in Network Security 🔐 | Rail Fence & Row Transposition Cipher Explained
Sundeep Saradhi Kanthety
155.1K views

5:53
Network Security - Transposition Techniques | Row Transposition Cipher | Rail Fence Cipher | Hindi
Ask Faizan
605 views

3:16
Substitution and Transposition Techniques | Substitution & Transposition cipher explain
DK Technical Point 2.0
777 views
2:46
keyless transposition cipher in hindi / types of transposition cipher in cryptography || #mscoder
ms coder
445 views

1:00:12
Traditional Transposition Cipher in cryptography in bangla | Keyed, Keyless, Columnar transposition.
content on demand
153 views

15:27
CLASSICAL ENCRYPTION TECHNIQUES 1.SUBSTITUTION TECHNIQUES2.TRANSPOSITION TECHNIQUES
simplified sem tutorials
6.4K views

5:29
#8 Encryption Techniques - Substitution & Transposition Techniques |Information Security|
Trouble- Free
72.5K views

5:44
CRYPTOGRAPHY & NETWORK SECURITY(8) Cryptography Techniques Transposition Technique
Algorithm Pod
66 views

2:58
Keyless Transposition technique |Transposition Cipher | Introduction in Hindi |CSS
Gyanpur
79 views

10:49
Keyed Cipher|Keyed transposition cipher|Keyed and keyless transposition cipher|Network Security
Last Night Study
12.6K views

3:43
Rail fence Cipher in network Security | Zigzag Cipher | Transposition cipher | Keyless transposition
Chirag Bhalodia
8.8K views

3:50
Transposition Cipher ll Keyless Transposition Technique Explained with Solved Example in Hindi
5 Minutes Engineering
91.1K views

5:34
Substitution Cipher vs Transposition Cipher|Substitution Cipher and Transposition Cipher|E Commerce
Last Night Study
3.5K views

7:35
Part 10 : Transposition Ciphers - Columnar Transposition
Center4CS
2.8K views

2:54
Difference between Substitution Cipher and Transposition Cipher | Substitution vs Transposition
Chirag Bhalodia
22.2K views

57:10
Consultation Transposition NIS 2 : Présentation de la directive et de sa transposition nationale – Partie 1
ANSSI
9.7K views
27:57
Consultation Transposition NIS 2 : Présentation de la directive et de sa transposition nationale – Partie 2
ANSSI
2.8K views

4:19
Columnar Transposition Technique | Transposition Cipher| Introduction in Hindi |CSS
Gyanpur
316 views

7:39
Rail fence cipher and row transposition cipher in hindi types of transposition cipher || #mscoder
ms coder
924 views

15:05
CNS- Cryptography and Network Security-BE IT- Transposition Techniques
CSE-IT-AI-DS Department GHRIBM, Jalgaon JALGAON
38 views

21:50
Transposition Techniques /CS 409 Cryptography and Network Security - Part 5
Renisha's CS Eduworld
249 views

6:27
Substitution vs transposition ciphers | classical encryption techniques | Cryptography | Urdu/Hindi
Fawad Speaks
129 views

23:41
TY BSc-IT - NS Unit 1 - Lec 4 - CRYPTOGRAPHY TECHNIQUES, Substitution, Transposition, Ceasar Cipher
Tirup Parmar
887 views
9:44
Transposition Techniques | Cryptography and Network Security
Ekeeda
304 views
10:12
Hybrid cipher|Hybrid Transportation Cipher|Transposition techniques in cryptography|Network Security
Last Night Study
1.2K views

3:53
Transposition techniques in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
2.0K views

9:12
Feistel Cipher Structure and Column transposition Techniques|| Cryptography and NS
Lab Mug
6.4K views
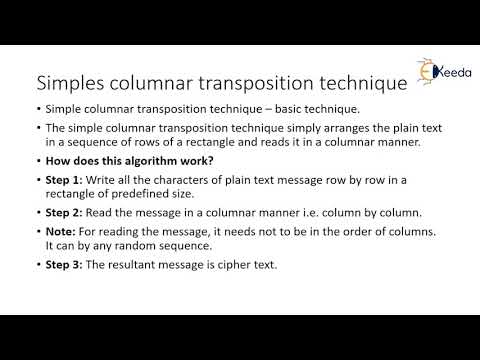
12:54
Key and Keyless transposition techniques | Cryptography and Network Security
Ekeeda
282 views

3:58
Cryptography - Transposition Techniques
IT DEPATRMENT PSGCAS
5 views
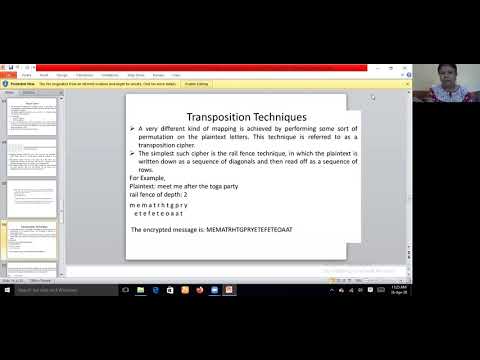
12:47
Transposition Techniques & Steganography Network Security & Cryptography Dipti Prasad MCA Sem4 MCR R
M.C.A Department Marwari College, Ranchi
43 views
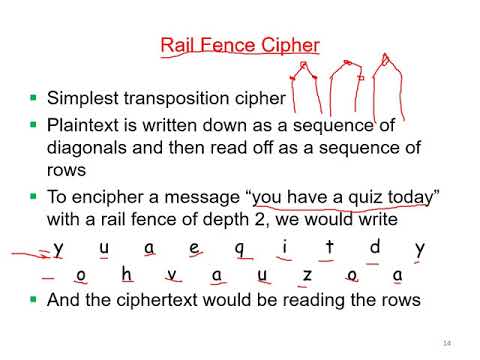
12:13
10 - Cryptography for E-Security - Transposition Techniques
Lectures
174 views

4:20
Encryption Techniques (substitution and transposition) Cryptography and Network security in HINDI.
Helping Tutorials
9.9K views

5:20
Transposition Techniques || Rail Fence technique in cryptography and network security
Lab Mug
11.6K views

0:56
Gold Refining Techniques Traditional Techniques vs. Modern Techniques
K-jhil Scientific
3 views

1:34
work study techniques - study techniques for students - innovative study techniques
villaelisa5000z
1 views

5:45
CRYPTOGRAPHY & NETWORK SECURITY(7) Cryptography Techniques substitution techniques, Hill Cipher
Algorithm Pod
72 views

7:47
CRYPTOGRAPHY & NETWORK SECURITY(6) Cryptography Techniques substitution techniques, Playfair Cipher
Algorithm Pod
67 views

13:13
Substitution Techniques in Cryptography Techniques || Cryptography and NS in Telugu
Lab Mug
17.2K views

4:49
CRYPTOGRAPHY & NETWORK SECURITY(5) Cryptography Techniques substitution techniques
Algorithm Pod
57 views

6:50
CRYPTOGRAPHY & NETWORK SECURITY(4) Cryptography Techniques substitution techniques, Ceaser Cipher
Algorithm Pod
88 views

8:14
Substitution Cipher | Transposition Cipher | Product Cipher With Examples
A Z Computing
12.5K views

10:48
Transposition Cipher, Encryption and Decryption with solved examples | Lecture 08 | by Muazzam Ali
Karo Mumkin
299 views

5:15
Transposition Techniques
WorthWatching
201 views

6:53
Transposition Techniques | Prof. Priyanka Sorte | PHCASC
MES e-Learning
142 views
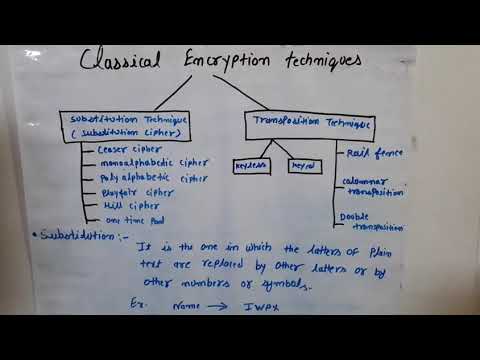
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

29:36
Transposition Cipher Techniques & Steganography
Learning Hub for IT Engineering
45 views

46:54
Encryption Techniques || Substitution and Transposition ||Caesar, Atbash, Polybius, Pigpen, Playfair
Kifayat Ullah
408 views