Search Results for "steganographic technique"
Find videos related to your search query. Browse through our collection of videos matching "steganographic technique". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "steganographic technique"
50 results found
6:09
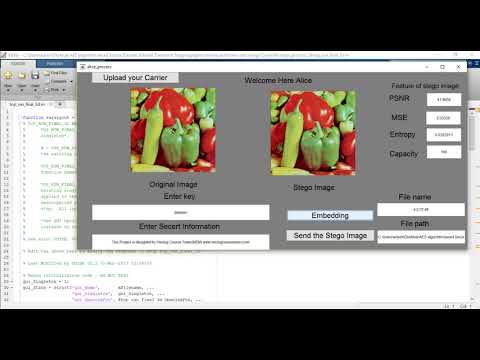
AES ALGORITHM BASED SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE IMAGES
VERILOG COURSE TEAM
739 views

10:38
SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE COLOR IMAGE
VERILOG COURSE TEAM
1.3K views

1:55
AI Used to Hide Secret Messages - New Steganographic Technique Bypasses Cybersecurity Systems
ThreatScape-AIWatch
1.2K views
7:42
Final Year Projects | An Inpainting-Assisted Reversible Steganographic Scheme
MyProjectBazaar
38 views
1:37
Image steganographic techniques with improved embedding capacity and robustness
SHPINE TECHNOLOGIES
1.0K views
5:24
Final Year Projects | A Secure Image Based Steganographic Model Using RSA Algorithm and LSB I
ClickMyProject
7.0K views

16:19
Use of steganographic tools like OpenStego, to detect data hiding or unauthorized file copying
VIVA Institute of Technology Computer Engg Dept
2.9K views

38:23
DEF CON 10 - Michael Rogers - Steganographic Trojans
DEFCONConference
132 views
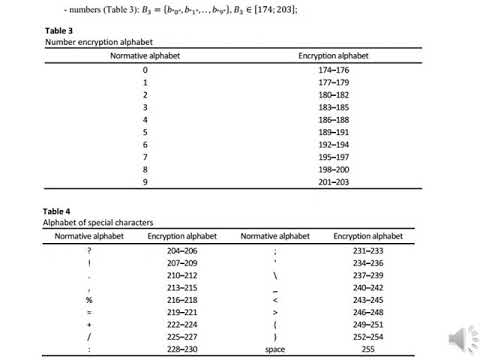
14:08
Information encryption method based on a combination of steganographic and cryptographic algorithm’s
Василь Триснюк
22 views

0:31
A Multilayer Steganographic Method Using Improved Exploiting Modification Directions Scheme
IFox Projects
9 views

0:31
A Multi-Layer Arabic Text Steganographic Method Based on Letter Shaping
IJNSA Journal
59 views

1:16
LACK steganographic method
steganonet
1.1K views

1:12:25
Decoding Satoshi: The Steganographic Hidden Message in the Bitcoin Whitepaper || Gavin Mehl
Gavin Mehl
1.8K views

0:57
Advanced Steganographic Malware. #ai #history #cyberhacking #cybersecurity #facts
Dr. Nachaat Mohamed (Cyber Security)
43 views

12:37
Hidden in Plain Sight? A Steganographic Analysis of The Bitcoin Whitepaper - Interesting results!
The Satoshi Observer
1.8K views
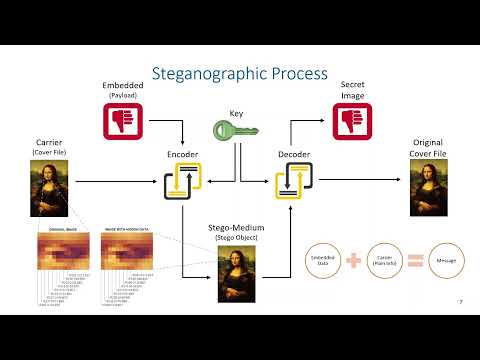
3:15
Steganography - Steganographic Process
Dustin Ormond
92 views
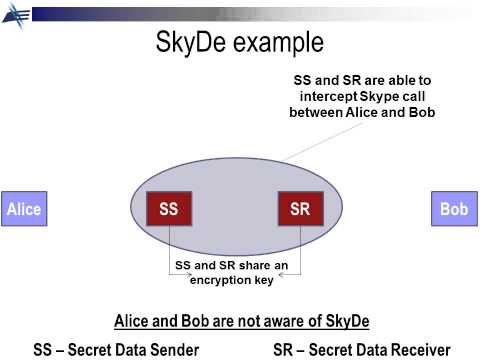
2:30
SkyDe (Skype Hide) - a new Skype-based steganographic method
steganonet
3.2K views

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views
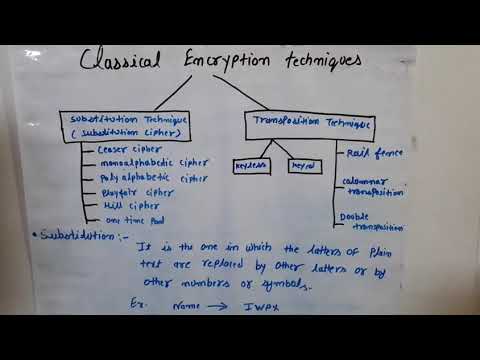
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

23:16
NIS-3.2-1 : Types of Cipher Technique (Substitution Cipher Technique, Caesar cipher)
rathod_sir
361 views

4:05
Substitution Cipher Technique V/s Transposition Cipher Technique in Cryptography and Network Securit
Short Tricks Learning
631 views

0:46
What technique do you use during competitive eating?: Competitive Eating Strategy And Technique
Scribble
1 views

5:42
Hair Cutting Technique: Mahogany Cutting Technique
Grant Sharp
8.7K views

3:05
Steganography: How to send secret file using steganography technique || by tech knowledge
tech knowledge
92 views

6:31
Hill cipher technique
Sivaraman
4 views

4:14
Row Transposition Technique|| Cryptography and Network Security
Lab Mug
7.1K views

56:41
Day 21 - What Is Image Steganography? | Secret Data Hiding Technique
Cyber SecGuru
59 views

6:17
Show, Don't Tell Writing Technique | EasyTeaching
EasyTeaching
124.7K views
7:57
griet-it-2012- a cryptographic technique for heterogenous sensor networks.wmv
Maruti Kumar
18 views

1:36
How to hide files/data behind any file using command prompt- Crptography Technique
TechSci City
1.1K views
1:01
Technique pour avouer ses sentiments à son crush 😂 #crush #sms #message #dm #histoire #humour
MrFromages
314.9K views

16:00
PLAYFAIR CIPHER WITH EXAMPLE||SUBSTITUTION TECHNIQUE||MATHEMATICS OF CRYPTOGRAPHY-- NETWORK SECURITY
t v nagaraju Technical
45.9K views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views

0:21
Satisfying art with glue gun technique!🎨 #art #artideas #craftideas #paintingideas #viralshorts
Mr.RS.technologist
3.0M views
31:43
Data Hiding with Encrypted Multi Secret Sharing using Modified LSB Technique
IJERT
167 views
8:21
Final Year Projects | AN OVERVIEW OF DATA HIDING TECHNIQUE:-STEGANOGRAPHY
ClickMyProject
659 views

0:10
Technique of taekwondo fight 🥋
PS Taekwondo
2.6M views
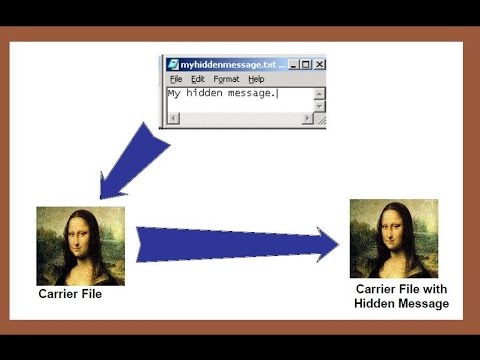
5:51
Steganography technique
Kids& Code
1.8K views

4:46
Demonstration of Implementation of Image Steganography using LSB Technique and Morse Code.
ProkillerGirl
110 views

12:59
Caesar Cipher Encryption and Decryption with Solved Example || Substitution Technique
A Z Computing
37.3K views
1:01
Kisiko Manane Ki Ninja Technique!! 🤣 😂 #k3g #srk #funny #kareenakapoorkhan #hrithikroshan #kajol
Just Chill
19.2M views

15:14
BEHAVIOURAL Interview Questions & Answers! (The STAR Technique for Behavioral Interview Questions!)
CareerVidz
663.7K views

10:53
PART 4 | HASH FUNCTION ATHENTICATION TECHNIQUE IN CRYPTOGRAPHY & NETWORK SECURITY (BANGLA)
COMPUTER SCIENCE WITH BHASKAR SIR
229 views

11:08
5 STAR Interview Questions and ANSWERS! How To Use The STAR Technique!
CareerVidz
87.8K views
2:25:42
Cryptography in network& computer security |Cryptography Encryption Technique| chapter three #በአማርኛ
Universal-tube
6.2K views

10:57
Additive Shift Ceaser Cipher Technique || Lesson 5 || Cryptography || Learning Monkey ||
Wisdomers - Computer Science and Engineering
435 views
7:38
MONOALPHABETIC CIPHER || SUBSTITUTION TECHNIQUE || CRYPTOGRAPHY || LECTURE 6 || HIRALSHASTRI
Shastri Hiral
112 views
4:55
A new image encryption technique combining Elliptic Curve Cryptosystem with Hill cipher in Matlab
OKOKPROJECTS
204 views

12:06
TRANSPOSITION TECHNIQUES || RAIL FENCE TECHNIQUE || COLUMNAR TRANSPOSITION -- NETWORK SECURITY
t v nagaraju Technical
11.8K views
16:50
The Caesar Cipher: A Simple Yet Powerful Cryptographic Technique
Harshit Jain
78 views