Search Results for "sp:ti:away=LEC"
Find videos related to your search query. Browse through our collection of videos matching "sp:ti:away=LEC". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "sp:ti:away=LEC"
50 results found

20:53
Home And Away 8607 Full Episode 21st October 2025 | Home And Away 21 October 2025 | Home And Away Tuseday October 21, 2025 | Home And Away 21st October 2025 | Home And Away 21 October 2025 | Home And Away 21-10-2025 |
Newmarkit7
446 views

51:09
FNATIC POBY DEBUT IN THE LEC VERSUS HERETICS - LEC SUMMER 2025
Caedrel
343.2K views

2:54
AWAY FROM CROWD - Away from crowd
On Music
1 views

4:12
AWAY FROM CROWD- AWAY FROM CROWD
On Music
1 views

0:48
Sridevi Died In Dubai _ Bollywood Actor Sridevi Passes Away _ Sridevi Passes Away In Dubai _
Md. asibur rahman
6 views

3:06:04
The president became obsessed with his fiancee after she passed away. He got drunk and mistook the girl for a substitute. He fell madly in love with her until she ran away pregnant. He then realized that she was the one he missed and loved day and night.
NLK Channel
84 views

0:28
What is panic away - panic away one move technique
awer bahi
53 views

5:33
(Roddy flushing away) - Flushed-Away
Evan Robert/Edward McClintock Senior
212 views

16:56
Lec-12: DFA (Part-2) | What is DFA in TOA with examples in hindi/urdu | DFA in TOC | Finite Automata
YZ Tutorials
162 views

53:26
Mod-01 Lec-01 GRAMMARS AND NATURAL LANGUAGE PROCESSING
nptelhrd
389.0K views

19:31
Lec 59 Cyclic Groups and Discrete Logarithm
NPTEL - Indian Institute of Science, Bengaluru
509 views

3:31
Can You HIDE a SECRET PAYLOAD in a JPEG Image? - Lec 27
Hack Sphere X
5.9K views

48:04
Lec 6: Velocity, acceleration; Kepler's second law | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
252.5K views

1:04:54
CSE104, Computational Complexity: Lec 1, Cantor's diagonalization
C. Seshadhri
1.0K views
9:07
Complexity Classes | P & NP classes | TOC | Lec-96 | Bhanu Priya
Education 4u
197.8K views

35:47
Cryptography & Network Security | Unit-2 | Lec-2 | One Shot | KCS-074 | Aktu Exams| PYQ Solutions
Multi Atoms
10.3K views

51:37
Lec 3: Bias-Variance Tradeoff
NPTEL IIT Guwahati
16.3K views

13:53
Lec-13: NFA to DFA (Part 2) | Explained in Detail | YZTutorials
YZ Tutorials
120 views

19:29
POBY DEBUT GAME in the LEC | FNC vs TH Voicecomms
FNATIC
80.5K views

50:10
Lec 12: Gradient; directional derivative; tangent plane | MIT 18.02 Multivariable Calculus, Fall 07
MIT OpenCourseWare
261.7K views

59:33
Mod-01 Lec-11 Regular expressions, they denote regular languages.
nptelhrd
24.4K views

8:31
CCS | Unit-1 | Lec-01 | Introduction to Computer Security
s kalaivani
270 views

5:51
Lec-9: Operators in Python 🐍 Precedence & Associativity with examples | Python for Beginners
Gate Smashers
166.5K views
12:55
Tuples in Python | 11th Computer - Chapter 2 - Lec 23
Academics with AB
6.7K views

17:36
TOC Lec 43-Turing machine problem Palindrome by Deeba Kannan
DEEBA KANNAN
216.3K views

52:18
Lec 10: Second derivative test; boundaries & infinity | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
228.4K views
53:53
Mod-13 Lec-03 Undecidability2
nptelhrd
1.6K views

34:31
Lec 25: Sequential Decision Problems
NPTEL IIT Guwahati
11.0K views

11:02
TOC Lec 46-Multiplication in turing machine using subroutines by Deeba Kannan
DEEBA KANNAN
90.9K views
4:07
Personal Computing system | OS | Lec-09 | Bhanu Priya
Education 4u
94.8K views
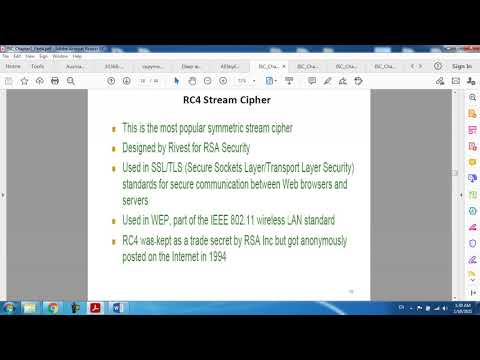
25:36
Cryptography and Network Security I \ Lec. 7 \ ( RC4 , RC5 and Blowfish Algorithms)
Dr. Ali J. Abboud
1.4K views
56:03
Mod-06 Lec-01 Variants of FA
nptelhrd
675 views
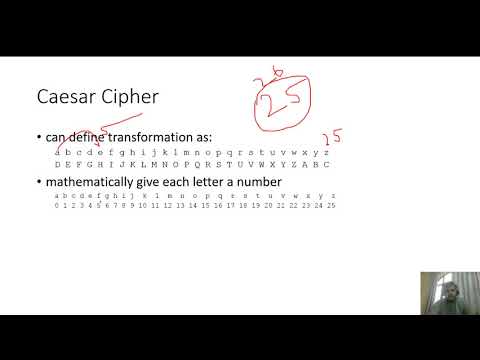
9:43
Caesar Cipher Explained with Solved Example|lec 3|urdu|hindi
ITphile
379 views

1:01:04
Mod-01 Lec-02 Introduction to finite automaton.
nptelhrd
93.0K views

50:50
Lec 5: Parametric equations for lines and curves | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
315.7K views

54:31
Mod-10 Lec-01 Pushdown Automata
nptelhrd
1.7K views

50:03
Cryptography & Network Security | Unit-3 | Lec-2 | One Shot | KCS-074 | Aktu Exams| PYQ Solutions
Multi Atoms
11.8K views

16:58
Deterministic Finite Automata|LEC-7|Formal Languages andAutomata Theory, VTU syllabus module - 1
Vijaya Prasad Lectures
2.6K views

11:08
Lec-5: What is Grammar in TOC | Must Watch
Gate Smashers
1.3M views

6:43
Turing machine ( TM) | Introduction | Part-1/2 | TOC | Lec-85 | Bhanu Priya
Education 4u
290.9K views

7:43
Convert Regular Expression to Finite Automata | Examples | TOC | Lec-43 | Bhanu Priya
Education 4u
202.2K views

6:14
Lec-81: Symmetric Key Cryptography in Network Security with examples
Gate Smashers
663.8K views

55:49
Mod-01 Lec-20 Introduction to context free languages (cfls)
nptelhrd
40.0K views

15:52
what is cryptography lec 2
#tech
1 views

7:26
NFA Example | Part-1/3 | TOC | Lec-14 | Bhanu Priya
Education 4u
234.8K views

12:43
Lec-03:Asymmetric Key Or Public Key | CRYPTOGRAPHY AND NETWORK SECURITY
webSak
45 views

50:09
Lec 11: Differentials; chain rule | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
226.4K views

13:13
Converting CFG to CNF | Example | TOC | Lec-71 | Bhanu Priya
Education 4u
780.6K views

10:30
Introduction to cryptography and network security lec-1
John dance master
17 views

56:02
Mod-01 Lec-31 Introduction to pushdown automata (pda).
nptelhrd
31.7K views