Search Results for "quantum cryptographic algorithms"
Find videos related to your search query. Browse through our collection of videos matching "quantum cryptographic algorithms". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "quantum cryptographic algorithms"
50 results found

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views

48:03
A Comparative Study of Classical and Post-Quantum Cryptographic Algorithms in the Era of Quantum Com
Aljazari Foundation
6 views

4:15
How Secure Are Current Cryptographic Systems Against Quantum Algorithms? - Quantum Tech Explained
Quantum Tech Explained
2 views

19:15
#1 Quantum Algorithms & Cryptography | Quantum Algorithms & Cryptography
NPTEL-NOC IITM
15.3K views
33:46
Clustering Algorithms | Data Science Algorithms | ML Algorithms | Edureka | ML Rewind - 3
edureka!
4.0K views

0:33
Scientists Have Successfully Hacked Cryptographic Algorithms Using a Quantum Computer!
B World Trade
282 views

4:42
Quantum Supremacy?! What a Quantum Computer can really do! From Feynman to Quantum Algorithms!
Christoph Gruebl
93 views

1:04:33
Quantum-Safe Algorithms | Quantum AI, Post-Quantum Cryptography (PQC) Kya Hai? Cybersecurity Future
RAKTIM SINGH
147 views
1:46:54
Quantum Algorithms part 2 | Fundamentals to Shor's and Grover's Algorithms, Oracles, Entanglement
Research Tech info
44 views

0:43
Quantum Resistant Algorithms - QR Algorithms Future Proofing Encryption Short
Technically U
703 views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

0:34
Cryptographic | CRYPTOGRAPHIC meaning
Word Mastery Channel
0 views

0:34
How To Pronounce Cryptographic🌈🌈🌈🌈🌈🌈Pronunciation Of Cryptographic
Isabella Saying
33 views

0:02
How to pronounce Cryptographic / Cryptographic pronunciation
Raccoon Teaches You
48 views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

15:46
🌟🔒 Preparing for Quantum Threats Developing Quantum Resistant Cryptographic Protocols
Science News
10 views

2:58
What Is Cryptographic Agility For Quantum Disruption? - Quantum Tech Explained
Quantum Tech Explained
3 views
3:12
Why Is Cryptographic Agility Key For Quantum Readiness? - Quantum Tech Explained
Quantum Tech Explained
9 views
0:36
Quantum Cryptographic Protocol..| Quantum Key Distribution
NO NONSENSE PROPERTIES & INVESTMENTS
252 views

0:25
Read The Physics of Quantum Information: Quantum Cryptography, Quantum Teleportation, Quantum
Vchana
0 views

4:44
What is Quantum? | Quantum Tech: Unveiling the Future| Quantum Computng| Quantum Cryptography
SarmadTechUmpire
7 views

6:34
Quantum Key Distribution QKD | Quantum Cryptography | Quantum Mechanics| Quantum Computing tutorial
Ligane
81 views

1:45
Quantum Computing Questions and Answers | Quantum Computing Explained | Quantum Computer #quantum
LearnWithDhiru
292 views

4:47
PBL RKS-115 Implementation of Cryptographic Algorithms in Steganography and Puzzle Game
Kelompok 5 PBL-115 RKS
35 views
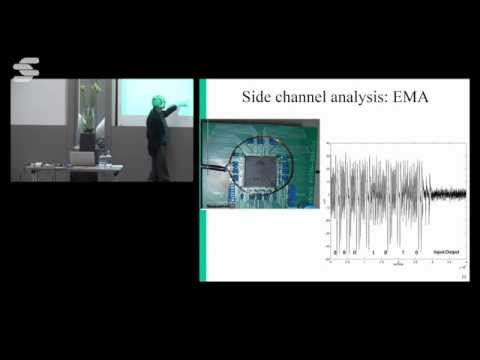
1:31:37
Cryptographic Algorithms - Bart Preneel
secappdev.org
1.6K views

6:48
CISSP Cryptographic Algorithms - Domain 3 Security Architecture & Engineering | Urdu | Hindi |
Free Education Academy - FreeEduHub
102 views

4:07
What Cryptographic Algorithms Does KMS Use For Security? - Cloud Stack Studio
Cloud Stack Studio
0 views

2:32
What Are Common Cryptographic Algorithms? - Tactical Warfare Experts
Tactical Warfare Experts
9 views

19:07
Symmetric/Asymmetric Cryptographic Algorithms - Privacy Best Practices | Information Security Course
Free Education Academy - FreeEduHub
543 views

1:01
Understanding cryptographic algorithms in cybersecurity.
Shield Identity
17 views

0:45
Types of Cryptographic Algorithms ✍️
ComputeVerse
672 views
![WGAN-GP & Genetic Algorithms [Side-Channel Attacks, Cryptographic Protocol Optimization]](/image/i.ytimg.com/vi/EZohUbomaiw/hqdefault.jpg)
9:40
WGAN-GP & Genetic Algorithms [Side-Channel Attacks, Cryptographic Protocol Optimization]
All About AI Tech
20 views

12:06
04-Understanding Cryptographic Algorithms 🚨 | Network Security & InfoSec Concepts
Sundeep Saradhi Kanthety
32.3K views

3:00
Why Are Cryptographic Algorithms Crucial For KMS Data Protection? - Cloud Stack Studio
Cloud Stack Studio
0 views
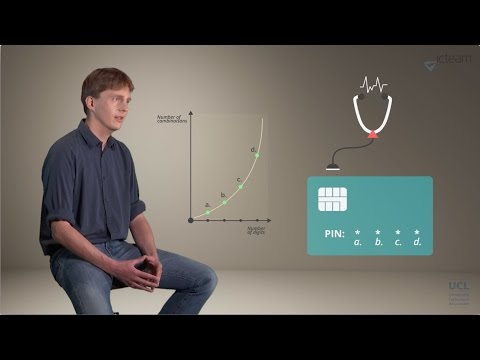
3:34
Cryptographic Algorithms and Secure Hardware
UCLouvain - Université catholique de Louvain
3.1K views
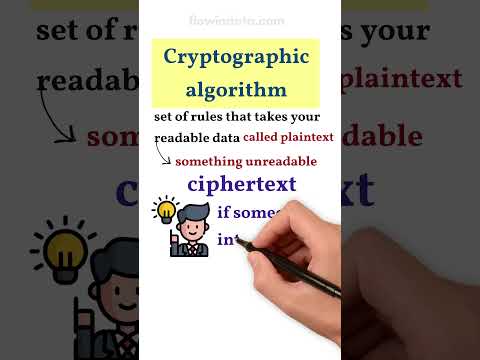
1:22
How Cryptographic Algorithms Keep Your Data Safe
flowindata
269 views

7:27
Types of Cryptographic Algorithms - Lecture 2,
Sudaisahmad1
60 views
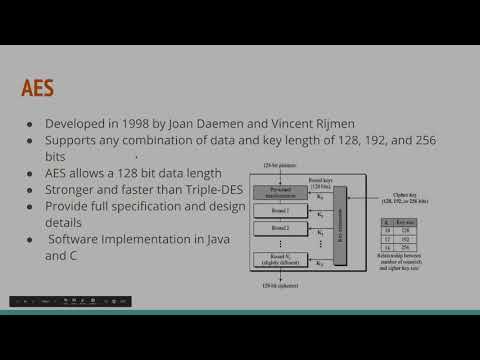
15:22
A Comprehensive Evaluation of Cryptographic Algorithms
Bert Franyie (mrkali88)
75 views

4:10
Openssl - Cryptographic algorithms, short explanation
Kind Spirit Technology
93 views

49:37
Cryptographic Algorithms: Bitcoin for Developers Study Session #2
Saylor Academy
2.8K views

4:00
How Do Cryptographic Algorithms Protect Your KMS Keys? - Cloud Stack Studio
Cloud Stack Studio
0 views

0:08
Read Cryptographic Algorithms on Reconfigurable Hardware (Signals and Communication Technology)
Varsenig
0 views
![[PDF] A Brief History of Cryptology and Cryptographic Algorithms (SpringerBriefs in Computer](/image/s2.dmcdn.net/v/FQ77z1e0lMtIy_oyi/x720)
0:05
[PDF] A Brief History of Cryptology and Cryptographic Algorithms (SpringerBriefs in Computer
MichellaMoss
4 views

0:26
Read A Brief History of Cryptology and Cryptographic Algorithms (SpringerBriefs in Computer
Tegan Brown
0 views

16:32
Cryptographic Algorithms
ScienceUp.org
1.5K views

1:24
A quick intro to cryptographic algorithms and protocols
Systemise
192 views

11:29
Episode 45: Cryptographic Lifecycle: Algorithms, Strength, Obsolescence
Bare Metal Cyber
3 views

6:00
The Validation of Cryptographic Algorithms and Development of Block Ciphers with Electronic
BP International
15 views

0:17
What are lattice-based cryptographic algorithms?
Intelligence Gateway
367 views

2:54
Unlocking Secure Data Mining: Cryptographic Algorithms Explained
Operational Excellence Mastery
8 views