Search Results for "hmac authentication"
Find videos related to your search query. Browse through our collection of videos matching "hmac authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hmac authentication"
50 results found

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views

6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views

20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views

6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views

57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views
5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views

7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views
7:05
HMAC - Cryptography I
Nguyen Duong Anh
80 views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views
1:09:59
Go UUID HMAC
Learn To Code
945 views

10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views
22:00
CNS HMAC
Kallam Gopala Reddy
312 views
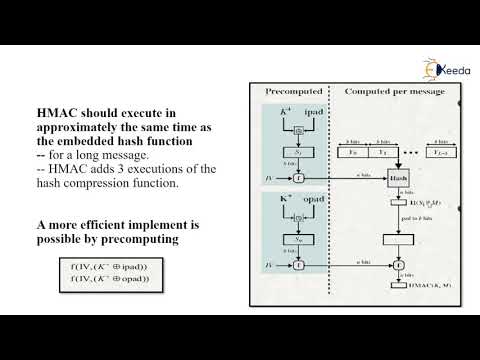
20:35
HMAC | Cryptography and Network Security
Ekeeda
677 views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views

0:46
HMAC Promo take 2
Players 2Pros
29 views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

15:16
5 1 Message Authentication Codes 16 min
Osiris Salazar
2.7K views

51:12
Authentication-1 : MSR VTU CNC
Rohit M
41 views

6:49
Message Authentication Code (MAC)
cipaaa
6 views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

12:48
How Kerberos Authentication Works and Why You Should Use It Detailed Explanation in Telugu
Lucky Tech
7.7K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

2:16:38
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

0:26
EKE Authentication - Applied Cryptography
Udacity
1.4K views

7:42
Digital Signature - Asymmetric Key , Why used for Authentication & Non Repudiation (Hindi)
Easy Engineering Classes
177.3K views

16:52
Kerberos Authentication Explained | A deep dive
Destination Certification
424.5K views

11:28
Kerberos Version 4 | Kerberos Version 4 using Authentication and Ticket Granting Server
Chirag Bhalodia
27.4K views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views
Page 1