Search Results for "distributed programming security"
Find videos related to your search query. Browse through our collection of videos matching "distributed programming security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "distributed programming security"
50 results found

15:19
Distributed Systems | Distributed Computing Explained
The TechCave
205.5K views
1:50
Distributed Computing Project output - Distributed Computing
Academic College Projects
8 views
4:56
Distributed Programming Fullstack 2021 | S3P12 | Security | Setup AuthContext and LoginUserEntity
Lars Bilde
116 views
9:06
Distributed Programming Fullstack 2021 | S3P43 | Security | Decode JWT Token | Validate Expiration
Lars Bilde
470 views
3:26
Distributed Programming Fullstack 2021 | S3P2 | Branching Frontend and Backend for Security
Lars Bilde
291 views

6:37
Distributed Programming Fullstack 2021 | S3P26 | Angular Security | Add JWT to Req with interceptors
Lars Bilde
131 views

5:35
Distributed Programming Fullstack 2021 | S3P4 | Security | AuthController with Login Endpoint
Lars Bilde
233 views
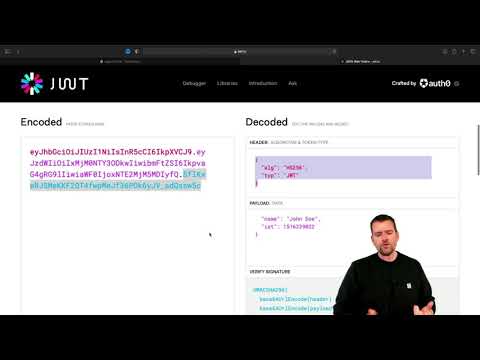
2:24
Distributed Programming Fullstack 2021 | S3P3 | Security | Very basic Json Web Token or JWT intro
Lars Bilde
213 views
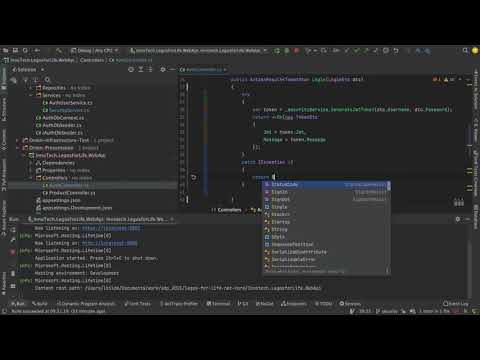
4:25
Distributed Programming Fullstack 2021 | S3P36 | Security | Changing Response from Backend Login
Lars Bilde
129 views

2:46
Distributed Programming Fullstack 2021 | S3P1 | Security Intro
Lars Bilde
791 views

2:17
Distributed Programming Fullstack 2021 | S3P8 | Security | JWT Validation | Digital Signing
Lars Bilde
124 views
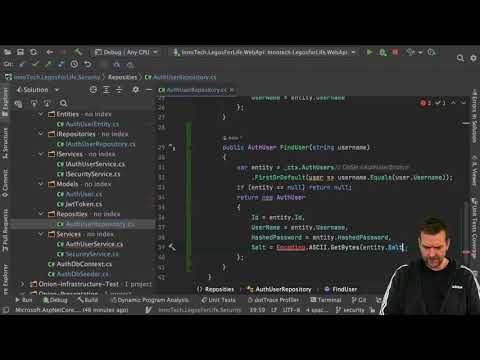
4:40
Distributed Programming Fullstack 2021 | S3P16 | Security | Adding Hashed Password and Salt to AuthU
Lars Bilde
151 views

2:37
Distributed Programming Fullstack 2021 | S3P20 | Security | Intro Creating a Secure Frontend
Lars Bilde
162 views
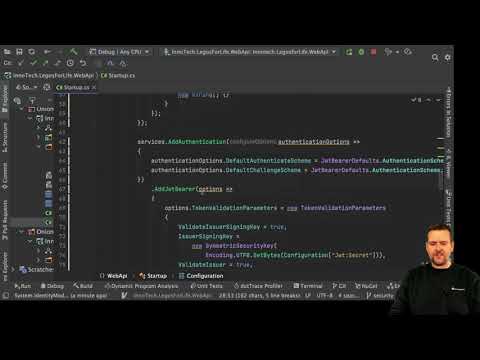
6:07
Distributed Programming Fullstack 2021 | S3P11 | Security | Generate a Json Web Token
Lars Bilde
155 views

4:58
Distributed Programming Fullstack 2021 | S3P42 | Security | Add Create User Form and Call Backend
Lars Bilde
249 views
2:21
Distributed Programming Fullstack 2021 | S3P7 | Security | JWT Use Authentication schema package
Lars Bilde
135 views

7:45
Distributed Programming Fullstack 2021 | S3P38 | Security | Create And save AuthUser in Service
Lars Bilde
201 views
4:50
Distributed Programming Fullstack 2021 | S3P5 | Security | Add a SecurityService
Lars Bilde
176 views
3:13
Distributed Programming Fullstack 2021 | S3P9 | Security | JWT Validation | Audience and Issuer and
Lars Bilde
893 views
4:48
Distributed Programming Fullstack 2021 | S3P18 | Security | Swagger Authentication with Hashed Passw
Lars Bilde
117 views
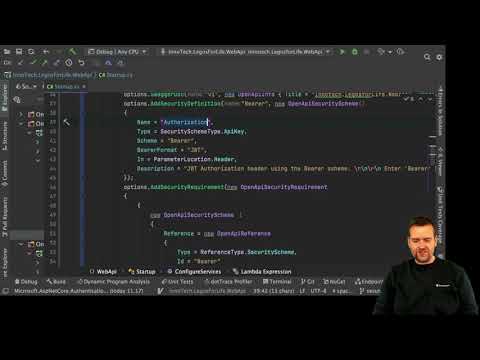
3:10
Distributed Programming Fullstack 2021 | S3P10 | Security | Add Bearer JWT to Swagger in Startup Fil
Lars Bilde
138 views
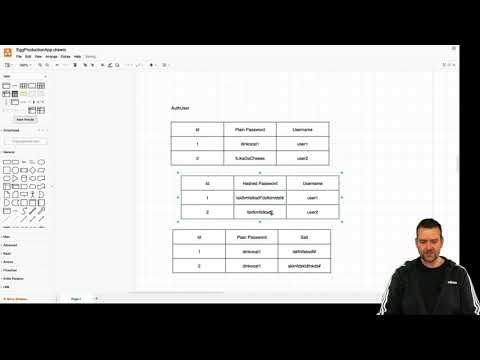
5:12
Distributed Programming Fullstack 2021 | S3P15 | Security | What is Hashed Passwords and Salt
Lars Bilde
123 views
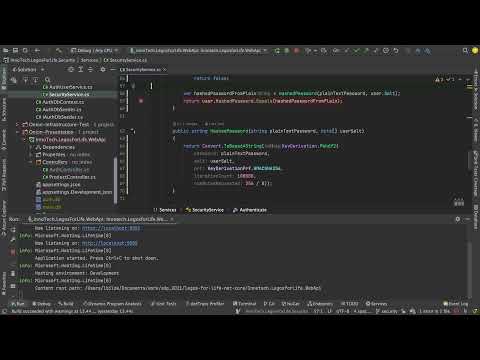
4:54
Distributed Programming Fullstack 2021 | S3P39 | Security | Create AuthUser Route in Our Web API
Lars Bilde
99 views

1:08
Security on distributed systems Cloud security versus traditional IT
IFox Projects
49 views
20:08
Building distributed systems with Msgflo Flow based programming over message queues
All Hacking Cons
9 views

4:27
How Secure Is Distributed Computing? - Next LVL Programming
NextLVLProgramming
3 views

20:28
Distributed secure programming with Spritely Goblins
Christine Lemmer-Webber
270 views

1:21:23
Secure Distributed Programming with Object-capabilities in JavaScript (Mark S. Miller, Google)
softwarelanguageslab
8.9K views

0:40
Principles of Concurrent and Distributed Programming: Algorithms and Models (Prentice-Hall
dm_014d27b77ac07f26e40cb463b06551d9
10 views

0:56
Distributed Security Enforcement in the Cloud | Joe Davolos on Altitude #podcast
Aviatrix Cloud Network Security
59 views

10:22
Foundation of Distributed Systems Security | Symmetric Keys | Asymmetric Keys | Digital Certificates
Think Software
3.4K views

14:51
DoS / DDoS ATTACKS IN CYBER SECURITY || Denial of Service || Distributed Denial of Service Attacks
Sundeep Saradhi Kanthety
35.7K views
0:51
Introducing Cisco HyperShield: Revolutionizing Distributed Security Architecture
Cables2Clouds Podcast
310 views
16:52
🔐 Blockchain Cryptographic Security, Hashing, Digital Signatures, and Distributed Ledgers
Crypto Chronicles
25 views

0:07
Download Recent Trends in Computer Networks and Distributed Systems Security: International
Ssanner
6 views

0:08
Download Distributed Networks: Intelligence Security and Applications PDF Free
Lsachs
2 views

2:33
History Of Java Programming Language | Java Programming For Beginners |Java Programming |Simplilearn
Simplilearn
101.2K views

1:10
BPL - Beginners Programming Language Cracked - BPL - Beginners Programming Languagebpl beginners programming language (2015)
Melanie Hernandez
17 views
![Network Programming Gear Full [Network Programming Gearnetwork programming gear]](/image/s1.dmcdn.net/v/951rI1e0O9SjcbJRp/xx720.pagespeed.ic.vZEtqUTX2C.jpg)
1:32
Network Programming Gear Full [Network Programming Gearnetwork programming gear]
Jarvis Bond
2 views

0:07
Read Programming #53:Python Programming Professional Made Easy & Rails Programming Professional
Vicks47
1 views

0:11
Download AI Application Programming (Programming Series) (Charles River Media Programming)
Naboorugreqirelle
1 views

0:05
Read C++ Programming Professional Made Easy & HTML Professional Programming Made Easy (Programming
Shila Gorelick
1 views

9:50
Funny Programming Memes - Developer Jokes - Programming Humours - Funny Programming
Fun
14 views

7:04
Programming Paradigms | Functional Programming | Object Oriented Programming | Logic | java world
Java World
67.1K views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

0:31
How to Start in Embedded Programming #programming #lowcode #tech #codinglessons #security
Low Level
1.3M views
26:41
Gladius: LWR based efficient hybrid public key encryption with distributed decryption
IACR
214 views
1:10:03
01731, Network Steganography, Chapter 6 (Distributed Hiding Methods), FernUniversität in Hagen
Steffen Wendzel
885 views

3:29
What Is Distributed Ledger Technology For Blockchain Beginners? - CryptoBasics360.com
CryptoBasics360
0 views