Search Results for "authentication exchange"
Find videos related to your search query. Browse through our collection of videos matching "authentication exchange". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "authentication exchange"
50 results found

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

13:43
Best Crypto App For India 2025 | Top 5 Safest Crypto Exchange | Best Crypto Exchange In India
IITian in Crypto News Today
22.8K views

8:47
Diffie Hellman Key Exchange Algorithm | Diffie Hellman key exchange algorithm example and solution
Chirag Bhalodia
45.5K views

5:02
Crypto Exchange क्या होता है | What is the meaning of Crypto Exchange & How it works #cryptocurrency
SI Traders
719 views

18:25
Diffie hellman key exchange || urdu hindi | diffie hellman key exchange algorithm lecture in urdu|42
IT Expert Rai Jazib
186 views

34:11
12-Diffie-Hellman Key Exchange 🔐 | Step-by-Step Guide | Secure Key Exchange Made Simple
Sundeep Saradhi Kanthety
244.9K views

5:40
london stock exchange online - london stock exchange open
jrgarcia1048
34 views

8:04
market of the london stock exchange - stock exchange in lon
jrgarcia1048
28 views

12:09
Diffie Hellman Key Exchange Algorithm | Secret Key Exchange | Network Security Tutorial | Edureka
edureka!
65.4K views

11:12
Kerberos Version 5 Message Exchange in cryptography | Message exchange in kerberos version 5
Chirag Bhalodia
9.7K views

13:12
Cryptocurrency Exchange for Bitcoin, Ethereum & Altcoins Binance | Binance exchange
Screen saga yt
1.1K views

2:46
Currency Exchange When to Exchange
pvault
668 views

1:03
PRIVATE EQUITY EXCHANGE - Le Private Equity Exchange 2024
B SMART
4.7K views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

51:12
Authentication-1 : MSR VTU CNC
Rohit M
41 views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views
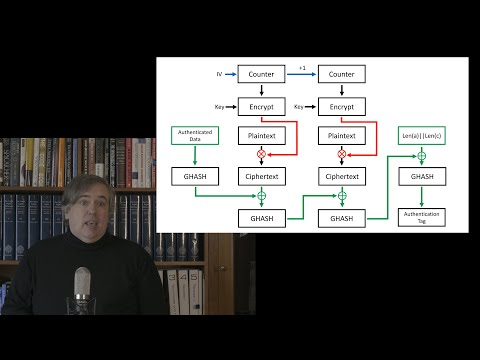
39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views
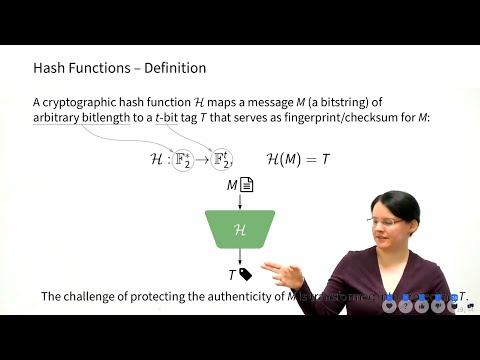
2:16:38
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

31:30
AUTHENTICATION REQUIREMENTS_FUNCTIONS_MAC_HASH FUNCTION
IN TECH
333 views

14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views
1:05
Fast Authentication using Chameleon Hashing Key Chain
University of Glasgow Singapore
229 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

1:00
Authentication vs Authorization
A Binary Code
92.8K views

13:01
Message Authentication Code MAC
Ekeeda
284 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views

0:47
Biometric Authentication in Cybersecurity
Tomorrow’s Tech Today
17 views

1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views

14:06
Authentication Bangla tutorial 2 : encrypting database
Anisul Islam
5.3K views

22:09
PhotoProof: Cryptographic Image Authentication for Any Set of Permissible Transformations
IEEE Symposium on Security and Privacy
851 views