Search Results for "adaptive chosen ciphertext"
Find videos related to your search query. Browse through our collection of videos matching "adaptive chosen ciphertext". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "adaptive chosen ciphertext"
50 results found

8:37
CSS #9 Cryptanalytic attacks|Ciphertext only|Known Plaintext|Chosen Plaintext|Chosen Ciphertext|BTB
Be The Best
3.1K views

12:24
Cryptanalysis | Ciphertext-only | Known plaintext | chosen ciphertext | chosen plaintext
chandu's smart class
111 views
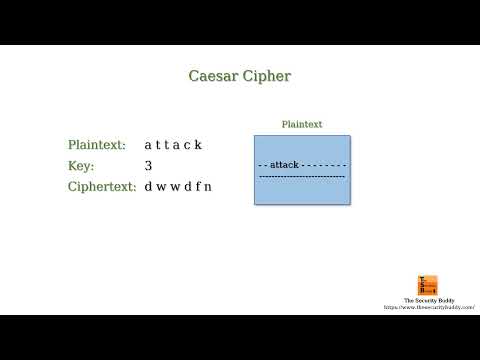
3:59
What are known-plaintext, chosen-plaintext, and chosen-ciphertext attacks in cryptanalysis?
The Security Buddy
8.5K views

3:55
Adaptive Learning 9: Adaptive Mobile Learning
Star Seal
4 views

3:47
What is a plaintext? What is a ciphertext? Ciphertext , Encryption, Decryption Defined and Explained
Technotics World
247 views

5:35
Chosen-ciphertext attack
WikiAudio
2.3K views

2:02
421 Chosen Ciphertext Attack
It Rating
270 views

24:26
Chosen-Ciphertext Security from Slightly Lossy Trapdoor Functions.
IACR
465 views

26:10
Chosen Ciphertext Security via Point Obfuscation
The Qualcomm Institute
251 views

28:41
USENIX Security '16 - Dancing on the Lip of the Volcano: Chosen Ciphertext Attacks on Apple iMessage
USENIX
186 views

12:06
7 3 Chosen ciphertext attacks 12 min
Jake Danniel
329 views
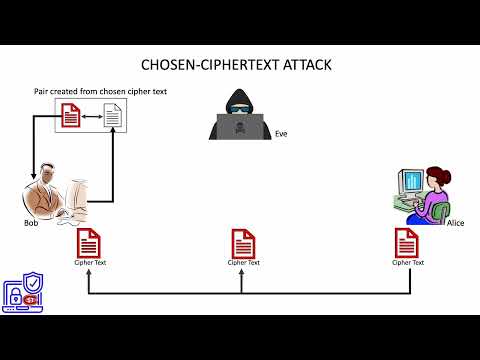
0:37
6. Chosen ciphertext attack
Cybersecurity at St. Cloud State University
6.2K views

16:51
LEC 16 ||Security Against Chosen Ciphertext Attacks
fahad osman
592 views

0:21
Chosen Ciphertext Attack, Cybersecurity Mini Dictionary #shorts
Datasafe World
24 views
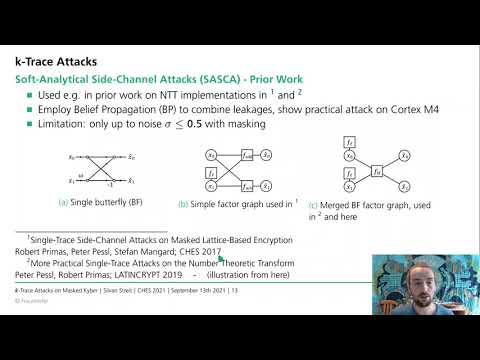
22:54
Chosen Ciphertext k-Trace Attacks on Masked CCA2 Secure Kyber
IACR
600 views

24:28
Alexander Poremba: On Quantum Chosen-Ciphertext Attacks and Learning with Errors
QuICS
137 views

12:17
USENIX Security '20 - Automating the Development of Chosen Ciphertext Attacks
USENIX
272 views
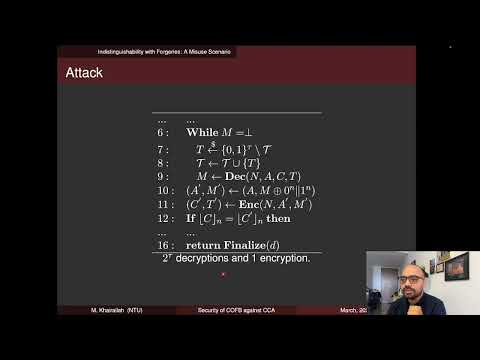
20:32
Security of COFB against Chosen Ciphertext Attacks
IACR
102 views

24:36
Quadratic Residues - Rabin and Chosen Ciphertext Attack - Part 15
DG
177 views

22:12
Realizing Chosen Ciphertext Security Generically in Attribute-Based Encryption and Predicate En...
IACR
354 views

43:18
Automating the Development of Chosen Ciphertext Attacks
IACR
572 views

16:24
Secure Signatures and Chosen Ciphertext Security in a Qu ...
IACR
477 views
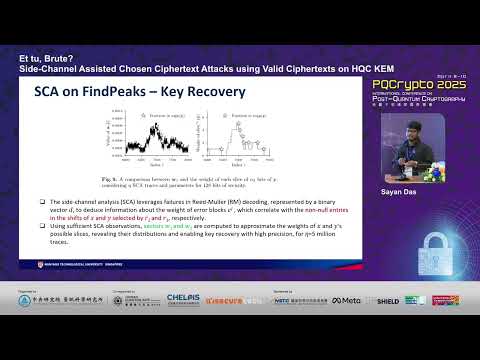
18:12
Et tu, Brute? Side Channel Assisted Chosen Ciphertext Attacks using Valid Ciphertexts on HQC KEM
PQCrypto conference videos
47 views

4:29
CISSP Cyber Security: Cryptographic Attacks (Known/Chosen Ciphertext) #cryptography #cryptosecrets
Cyber Security Cartoons
132 views

34:41
Lecture 14: Chosen Ciphertext Attacks (CCA-Security)
Cryptography - علم التشفير
795 views
0:19
Chosen Ciphertext Only
Quick Cybersecurity Study
38 views
55:37
CDL - Matt Green - Using SMT Solvers to Automate Chosen-Ciphertext Attacks
UCYBR - UMBC Center for Cybersecurity
50 views

23:06
Chosen-Ciphertext Secure Multi-Identity and Multi-Attribute Pure FHE
CANS - Cryptology and Network Security
79 views

5:56
Known/Chosen Plain Text & Known/Chosen Cipher Text Attacks: The Art of Deciphering
Shree Learning Academy
1.0K views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views
0:20
Adaptive Active Power Sharing Techniques for DC and AC Voltage Control in a Hybrid DC AC-2019-20
MATLAB ASSIGNMENTS AND PROJECTS
18 views

4:22
Edge Adaptive Image Steganography Based on LSB Matching - PASS 2010 IEEE Projects
pass pandian
1.7K views
0:39
AI Greenhood Turning Apartments into Adaptive Plant Ecosystems
TechTonic
23 views

0:18
Steganalysis Features for Content Adaptive JPEG Steganography
MICANS INFOTECH IEEE PROJECT PPT VIDEOS 2016
212 views

1:00
422 Adaptive Attacks
It Rating
15 views
11:10
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Final
Akash Joy
22 views
7:50
A New Convolutional Neural Network Based Steganalysis Method for Content Adaptive Image Steganograph
XOOM PROJECTS
5 views

0:17
enable adaptive power saving mode
tik mobile
109.6K views

1:07
IEEE 2016 - 2017 DOT NET PROJECTS STEGANALYSIS FEATURES FOR CONTENT ADAPTIVE JPEG STEGANOGRAPHY
PG Embedded Systems
44 views

0:41
Adaptive Quantum Cryptography for Everyday Security
FutureTech Unveiled
97 views

1:37
A Novel Data Embedding Method Using Adaptive Pixel Pair Matching | MATLAB
Final Year Projects
158 views

4:55
Learning Image-Adaptive Codebooks for Class-Agnostic Image Restoration
ComputerVisionFoundation Videos
15 views

0:03
Image filtering based on the shape-adaptive DCT transform (SA-DCT)
Kazem Gheisari
121 views

1:14
What is an Adaptive Algorithm? Explained Simply
flowindata
87 views

10:58
Adaptive Testing Explained: How ISC2 Exams Like CISSP, CCSP & SSCP Really Work
Mike Chapple
5.8K views

14:33
Adaptive Mountain Biking
The Ab5traktion
1 views

0:10
Read Reinforcement Learning: An Introduction (Adaptive Computation and Machine Learning)# Ebook
Lofis Blok
1 views

0:06
Read Adaptive Cryptographic Access Control (Advances in Information Security) Ebook Free
Melkadze 96
0 views
![[PDF] Data-Driven Methods for Adaptive Spoken Dialogue Systems: Computational Learning for](/image/s1.dmcdn.net/v/FZY5v1e2W1hHkcu6W/x720)
0:05
[PDF] Data-Driven Methods for Adaptive Spoken Dialogue Systems: Computational Learning for
OkeviaFranklin
4 views
![[Download] Reinforcement Learning: An Introduction (Adaptive Computation and Machine Learning)](/image/s2.dmcdn.net/v/Fb5ig1e9GOJFscRHE/x720)
0:08
[Download] Reinforcement Learning: An Introduction (Adaptive Computation and Machine Learning)
NieshaEisenba
1 views
Page 1