Search Results for "active authentication"
Find videos related to your search query. Browse through our collection of videos matching "active authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "active authentication"
50 results found

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

3:02
Difference between Active and Passive attack | Active vs Passive attack | Passive vs Active attack
Chirag Bhalodia
15.9K views

0:11
Active Voice & Passive Voice | How to use Active & Passive Voice | Active & Passive ka use #english
Englishtra
101.6K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views
![Active Lock Keygen [active lock 2015]](/image/s1.dmcdn.net/v/8_gFE1cmAgv2PUPaB/xx720.pagespeed.ic.xfm23yvcOH.jpg)
1:35
Active Lock Keygen [active lock 2015]
John Miller
49 views

4:36
Asa-failover-active-active
fcug
1 views

1:01
i20 Active - Live Active
lisa5253
1 views

0:30
Active Bodies, Active Minds
Major League Soccer
1 views

0:30
PSA | Active Bodies Active Minds
Major League Soccer
2 views

2:58
passive attack and active attack in hindi / passive attack and active attack difference ||#mscoder
ms coder
3.9K views

5:39
Past indefinite tense passive voice wh questions,past indefinite tense,active passive voice in hindi,passive voice in hindi,past indefinite tense passive voice examples,past indefinite tense passive voice in urdu,present indefinite tense active passive vo
Ilmotameel33
276 views

12:17
Active and Passive Voice Tricks | Active Voice and Passive Voice in English Grammar | ChetChat
ChetChat
532.8K views

9:15
Active and Passive Voice Tricks | 3 Secret Rules | Active Voice and Passive Voice in English Grammar
ChetChat
1.7M views

0:04
Rules of active voice and passive voice| short tricks of active voice and passive voice
Sandhya Singh
930.9K views

0:07
Passive Voice in English || Active and Passive Voice || Active Passive English Grammar
PKM ACADEMY
167.0K views

0:06
Active Voice To Passive Voice||Active Voice Passive Voice Chart #passivevoice #voice #grammar
Curious Classes
425.8K views

5:19
PAN is active but details are not as per pan, pan card active or inactive check,verify your pan card
Rmitanchal
396 views

3:00
Mercedes-Benz Active Safety - Active Brake Assist
AutoMotions
366 views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

51:12
Authentication-1 : MSR VTU CNC
Rohit M
41 views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views
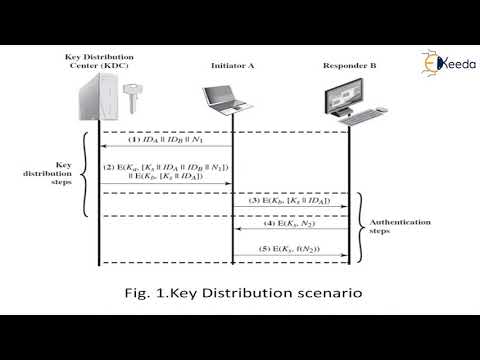
19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

2:16:38
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

31:30
AUTHENTICATION REQUIREMENTS_FUNCTIONS_MAC_HASH FUNCTION
IN TECH
333 views

14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views
1:05
Fast Authentication using Chameleon Hashing Key Chain
University of Glasgow Singapore
229 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views
1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views
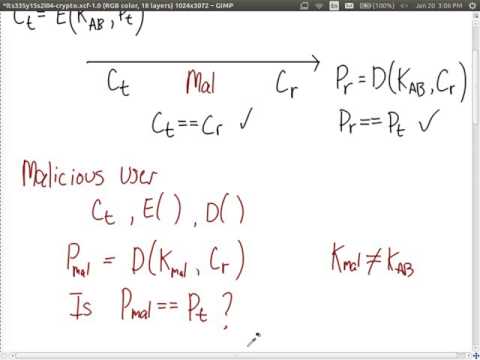
1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views
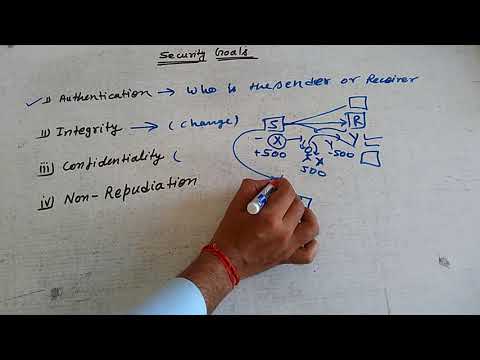
9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

1:00
Authentication vs Authorization
A Binary Code
92.8K views

13:01
Message Authentication Code MAC
Ekeeda
284 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views
Page 1