Search Results for "User Authentication Protocols"
Find videos related to your search query. Browse through our collection of videos matching "User Authentication Protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "User Authentication Protocols"
50 results found

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

1:09:38
CSE571-11-15B: User Authentication Protocols (Part 2 of 3)
Raj Jain
1.8K views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

0:21
IRCTC User Id & password kaise banaye Hindi #How to create IRCTC user is & password
BIKASH 4888
3.1M views

14:01
VB.NET Creating Login with Admin & User (User Level)
Codinger Tutorial
14 views

8:22
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
8 views

5:39
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
1 views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

8:37
Remote user authentication using symmetric encryption
Anand Pashupatimath
4.6K views

4:27
Introduction to User Authentication - CompTIA Network+ N10-005: 5.3
Professor Messer
15.0K views

58:47
Kerberos Version 4 & 5 and Remote User Authentication with Asymmetric Encryption -#21is71 VTU 7thsem
VTU padhai
2.3K views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

13:31
Build Node.js User Authentication - Password Login
Web Dev Simplified
565.0K views

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views

0:30
About For Books Mechanics of User Identification and Authentication: Fundamentals of Identity
dm_09d226e7605f9f5a1a3a6425e52120d4
0 views

0:27
Unlocking the Secrets of User Authentication
CyberGuard
0 views

0:40
Why Continuous User Authentication Matters
CyberGuard
1 views
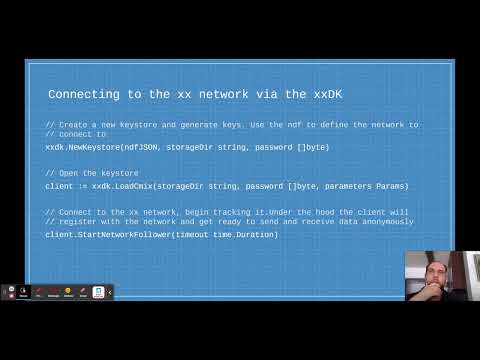
10:01
Preserving a user’s anonymity with cryptographic protocols | BeWater DevCon II
BeWater Community
257 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views
17:04
UNIT IV-COMMUNICATION SECURITY,AUTHENTICATION PROTOCOLS
janadeep n
24 views
1:20:56
COSIC Course 2024: "Cryptographic protocols for entity authentication and..." (Bart Preneel, COSIC)
COSIC - Computer Security and Industrial Cryptography
239 views

0:59
Protocols | meaning of Protocols
The Definition Channel
504 views

0:11
network protocols and ports | networking protocols interview questions
Technical Spartan - Thakur
149.4K views

1:21
Solar Energy - Renewable Energy - Montreal Protocols & Kyoto Protocols
Cyber Energy Ltd
11 views

0:08
Read [ AACN Protocols for Practice: Noninvasive Monitoring[ AACN PROTOCOLS FOR PRACTICE: NONINVASIVE
Airini Arono
0 views

0:05
Download Telephone Triage Protocols for Adults 18 Years and Older (Telephone Triage Protocols
MarianRench
1 views

0:35
Best product Telephone Triage Protocols for Nurses (Briggs, Telephone Triage Protocols for
walker
1 views
![[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley](/image/s2.dmcdn.net/v/Pt3_y1e9_0lvZvH-V/xx720.pagespeed.ic.GE78wmqjuE.jpg)
0:33
[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley
phamza-elhaddars
7 views

0:36
TCP/IP Illustrated, Volume 1: The Protocols: Protocols v. 1 (APC) Review
yoheg
5 views

4:37
Adherence to Covid-19 Protocols: Clamp-down on persons violating protocols begins (10-8-21)
The Multimedia group
3 views

2:30
Briefly describe on characteristics of the UDP(User datagram protocol)
Informative Tutorials
159 views

1:01
Windows 10 user good news for you 🥳 #shorts #windows10 #securityupdate
Prince Shah
587.1K views

3:43
CybersecurityComplianceFramework&SystemAdministration|WEEK 3 Server&User Administration Quiz Answers
Anand Ranjit Kumar Mukkala
2.5K views

10:30
15. Encrypting User Data with EFS in Active Directory
MSFT WebCast
18.2K views
![How to Create Multi User Login Form in java using MySQL Database ? [With Source Code]](/image/i.ytimg.com/vi/4IFvc7JOqtA/xhqdefault.jpg.pagespeed.ic.dVRMxcxVYG.jpg)
18:55
How to Create Multi User Login Form in java using MySQL Database ? [With Source Code]
RunCodes
125.4K views

9:05
How To Conduct User Interviews Like A Pro (UX Design)
CareerFoundry
162.7K views
0:42
Best i videos downloader app for iphone user #viral #shortvideo
Jacobabado Shazii
466.0K views

10:18
The Biggest Women A*user of Bollywood | Exposed
Absolute Aryann
215.7K views

16:13
ACISP2020 Tightly Secure Chameleon Hash Functions in the Multi User Setting and Their Applications
Xiangyu Liu
230 views
12:25
Visual Cryptography with Cloud Computing for Personal Security of the User
IJERT
12 views

0:43
Quickly organise lengthy user research with ChatGPT & Figjam | UIUX Design
yourdesignbestie | UX Design & Lifestyle
12.5K views

11:34
Advantage of Cryptography Tools & Securing End User Equipment
Ziauddin Zia
40 views

11:52
Data Cleaning in Excel | 8 Tricks to Make You a Pro User
Kenji Explains
137.5K views

17:06
Create User Registration Form in Java with MySQL || Swing and JDBC
CS CORNER Sunita Rai
47.8K views

0:25
Fastest way to design a user flow diagram #ux #uxdesigner #ui #uidesign
Jan Mraz UX
99.1K views
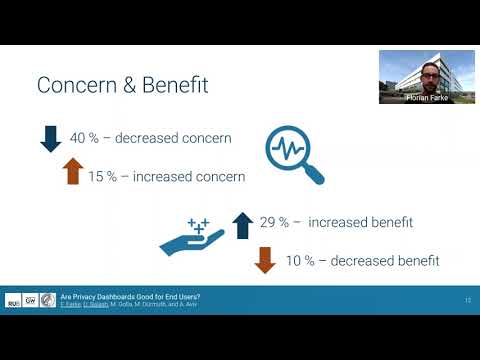
12:32
USENIX Security '21 - Are Privacy Dashboards Good for End Users? Evaluating User Perceptions...
USENIX
162 views