Search Results for "Euler Totient function cryptography and network security"
Find videos related to your search query. Browse through our collection of videos matching "Euler Totient function cryptography and network security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Euler Totient function cryptography and network security"
50 results found

15:44
Asymmetric Key Cryptography - Euler Phi Function (Euler Totient Function)
Vaishali Yadav
231 views

14:51
EULER'S THEOREM and EULER'S TOTIENT FUNCTION WITH EXAMPLES || MATHEMATICS OF ASYMMETRIC CRYPTOGRAPHY
t v nagaraju Technical
40.6K views

15:47
FERMAT THEOREM,EULER'S THEOREM, EULER'S TOTIENT FUNCTION, DISCRETE & HASH ALGO IN CRYPTOGRAPHY
COMPUTER SCIENCE & ENGINEERING
84 views
21:51
Euler's Totient Function & Euler's Theorem 🔥
Perfect Computer Engineer
10.7K views

0:13
Euler function of 12 |phi function of 12 #Euler function #group #ringtheory #discretemathematics
Alpha Maths Academy
36.8K views

3:51
Euler's Totient Function in Tamil | Cryptography and Cyber Security in Tamil | CB3491 in Tamil
4G Silver Academy தமிழ்
13.1K views
8:40
Euler’s Totient Function (Phi Function)
Neso Academy
350.3K views
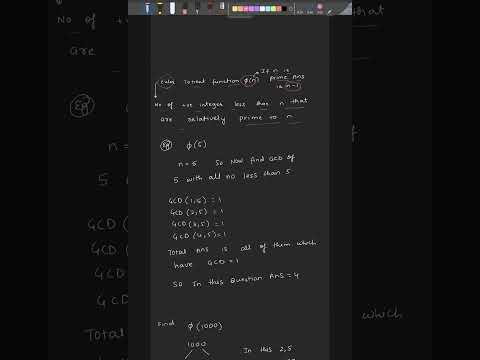
1:05
Euler totient function in principle of cryptography#EulerTotient #Cryptography #NumberTheory #Shorts
marTech with Neel
53 views
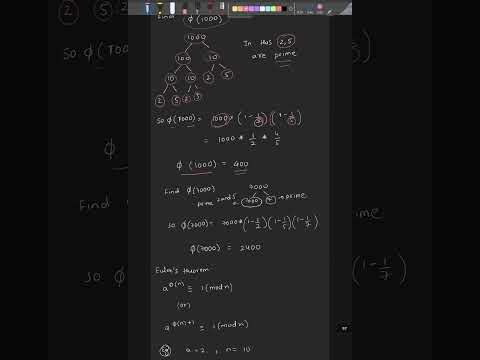
1:20
Euler totient function question in cryptography#EulerTotient #Cryptography #NumberTheory #Shorts
marTech with Neel
3 views

6:37
5 Modular Arithmetic for Cryptography- Part 4: Totient Function, Euler’s & Fermat’s Little Theorem
Dr Nitin Naik - Aston University, UK
19.9K views

2:18
Euler's totient function | Journey into cryptography | Computer Science | Khan Academy
Khan Academy Labs
199.3K views

3:53
Fermat's Little Theorem and Euler's Totient Theorem/Function
AlgoSTEM
576 views

2:12
Properties Of Euler's Totient Function
The Security Buddy
302 views
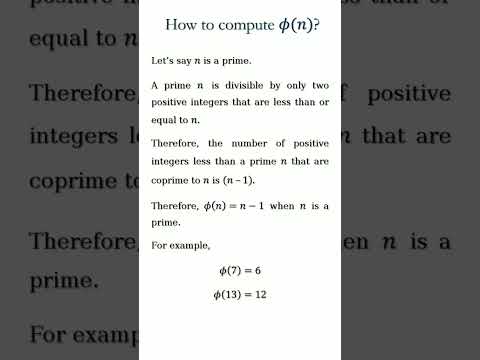
2:07
What is Euler's Totient Function?
The Security Buddy
301 views
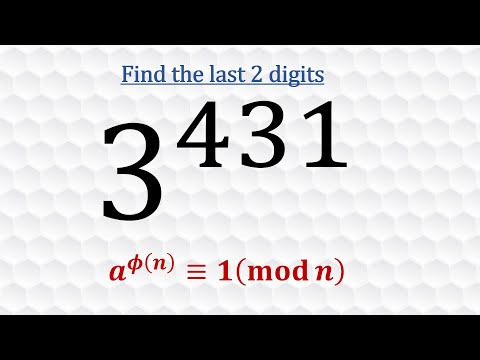
17:15
Last 2 digits using Euler's Totient Function
Prime Newtons
40.8K views

7:42
Euler's Toitient Function in Cryptography and Network Security
Abhishek Sharma
195.9K views
0:09
Function | Definition of function | define function | simple definition of function
Tartull education
23.4K views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

1:31:02
Lecture 11: Number Theory for PKC: Euclidean Algorithm, Euler's Phi Function & Euler's Theorem
Introduction to Cryptography by Christof Paar
156.9K views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

15:29
Euler's Totient Theorem and Fermat's Little Theorem - Complete Proof & Intuition
Mu Prime Math
75.0K views

7:19
Euler's Totient Theorem and Fermat's Little Theorem - Modular Arithmetic
Polynomial Maths
587 views

10:09
Cryptography and Network Security Course | Cryptography and Network Security Playlist | Cryptography
Abhishek Sharma
397 views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

43:15
cryptography and network security || cryptography and network security bangla tutorial.
Online_learning_tube
229 views

3:04:03
Cryptography and Network Security - Cryptography and Network Security Full Bangla Course
BD Techno Expert
1.2K views

9:06
A Model for Network Security in cryptography and Network Security || Cryptography and NS
Lab Mug
10.9K views

1:20
Projects on Network Security and Cryptography | Thesis on Network Security and Cryptography
Phdtopic. com
516 views

11:15
Security of MAC and HASH Function | Cryptography and Network Security
Ekeeda
3.3K views

19:13
Cryptography and Network Security - Prime Numbers, Fermat’s and Euler’s Theorem, CRT
Dr. Bhuvaneswari Amma N.G.
274 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

6:06
Need for Security | Network Security | Cryptography and Network Security
Bikki Mahato
405 views

3:57
Security Mechanisms | Network Security | Cryptography and Network Security
Bikki Mahato
184 views

9:23
MIME protocol in Cryptography and Network Security | Email security in Network Security
Abhishek Sharma
119.7K views

4:11
Cryptography and Network Security BCS072 Syllabus Introduction | AKTU Cryptography Network Security
EduShine Classes - Arman Ali
470 views

9:25
Principles of Public key cryptography in Network Security || Cryptography and Network Security
Lab Mug
7.1K views
0:43
Carmichael's totient function conjecture| Open problems
Ishan Banerjee
398 views

5:31
The Totient Function
1steinstein
43 views

8:09
Modular Arithmetic, Prime, Relatively Prime, Euler's Cryptography and Network security in Hindi.
Helping Tutorials
15.8K views

12:28
Cryptography & Network Security|| Fermat’s and Euler’s theorems|| DSE-2@DU
AV Maths School
52 views

8:24
Inverse Using Euler's Theorem | Modular Exponent | Cryptography And Network Security
Quick Trixx
24.4K views

6:59
Euler's theorem in Cryptography and Network Security
Abhishek Sharma
257.9K views

9:52
Graph Theory: Euler Paths and Euler Circuits
Mathispower4u
442.7K views

0:12
Euler's theorem on homogeneous functions, Corollary and deduction from Euler's theorem......
Vivek Mathematics
4.5K views

35:45
Hash Function in Cryptography(Malayalam)/CS 409 Cryptography and Network Security
Renisha's CS Eduworld
2.8K views

13:31
LEC01|Cryptography & Network Security | Intd.. to Cryptography&Network Security by Ms. M . Saranya
MLID - MLR Institute of Technology
185 views

14:52
Applications of Hash Function | Purpose of Hash Function | Real Time Application of Hash Function
Chirag Bhalodia
32.1K views

12:00
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
Chirag Bhalodia
107.9K views
Page 1