Search Results for "Control system vulnerabilities"
Find videos related to your search query. Browse through our collection of videos matching "Control system vulnerabilities". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Control system vulnerabilities"
51 results found

5:30
Rodent control | Pest Control service | rat control | Termite control | Indian Pest Control | Bedbug Control | Pest Control Delhi NCR | Pest Control Noida U. P. | Pest Control Haryana
rkhan71in
3 views

0:51
Blue Pest Control | Bed Bug Control in Norbury London | Mice Control in London | Rat Control | Cockroach Control
Blue Pest control
6 views

1:06
Fly Control, Pest Control , Termite Control, Pest Control in Delhi NCR, cockroaches control service
rkhan71in
1 views

0:46
Pest Control | Termite Control | Rodent Control | Indian Pest Control | Mosquito Control
rkhan71in
3 views

3:35
Silverfish control | bedbug control | All Pest Control Service | Pest control in India | Indian Pest Control
rkhan71in
1 views

5:23
Pest Control | Termite Control | Rodent Control | Indian Pest Control
rkhan71in
12 views

0:25
Access Control System Wiring Diagram | access control system installation
Electrical genius
148.2K views

8:12
Door access control system |How to install Access control system |Secureye B4CB installation /Wiring
Technical GuideWala
5.3K views

0:49
1 Degree system | 1 Degree system in Hindi | 1 Degree system mathematical tool | what is 1 Degree system #cityclasses
cityclasses
1 views
0:41
911 Outage Sparks Concerns Over Emergency System Vulnerabilities
Benzinga
610 views

12:23
AIAG Control Plan (V1, 2024) | Types of Control Plan | Benefits of Control Plan |
Quality HUB India
17.6K views

11:19
Goose, Control Control Control
Le Soir
8 views

1:28
Control cancer book | control cancer ebook | control cancer
Don Paent
20 views

8:26
Control, control, control 3D3
Brumail
17 views

13:42
Control Your Mind, Control Your Life : Jesus | How to control your mind | Jesus Speaks
Jesus Speaks
8 views

6:32
Mass shootings reignite gun-control debate in United States | Gun Control Debate | How Do We Fix America's Gun Control Problem? | Democratic Candidates Debates in United States Of America
Fun Doze With Me
4 views
![Download [PDF] Feedback Control Problems Using MATLAB and the Control System Toolbox (Bookware](/image/s1.dmcdn.net/v/MEGLY1e0SCTp_meL0/xx720.pagespeed.ic.x2Wg-rz7vR.jpg)
0:37
Download [PDF] Feedback Control Problems Using MATLAB and the Control System Toolbox (Bookware
yirzofolta
29 views

0:31
ESSL Js32 access control password programming system #essl #access #control
NF CCTV
3.8K views
13:14
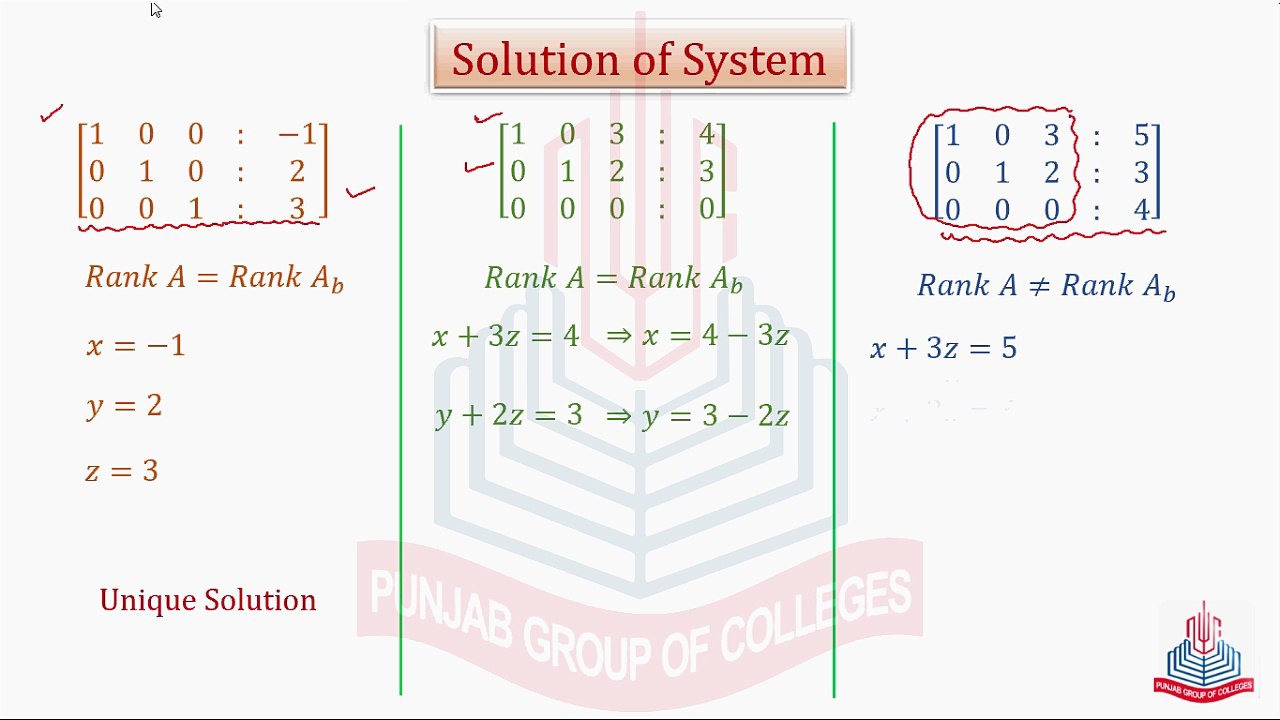
Consistent System, Inconsistent System & Solution of System of Non-Homogeneous Equations
Punjab Group Of Colleges
1 views

1:00
security system (security system) "security system"
localvideotv
5 views

45:22
Google Drive System Design | Dropbox System Design | File Sharing Service System Design
Think Software
8 views
5:14
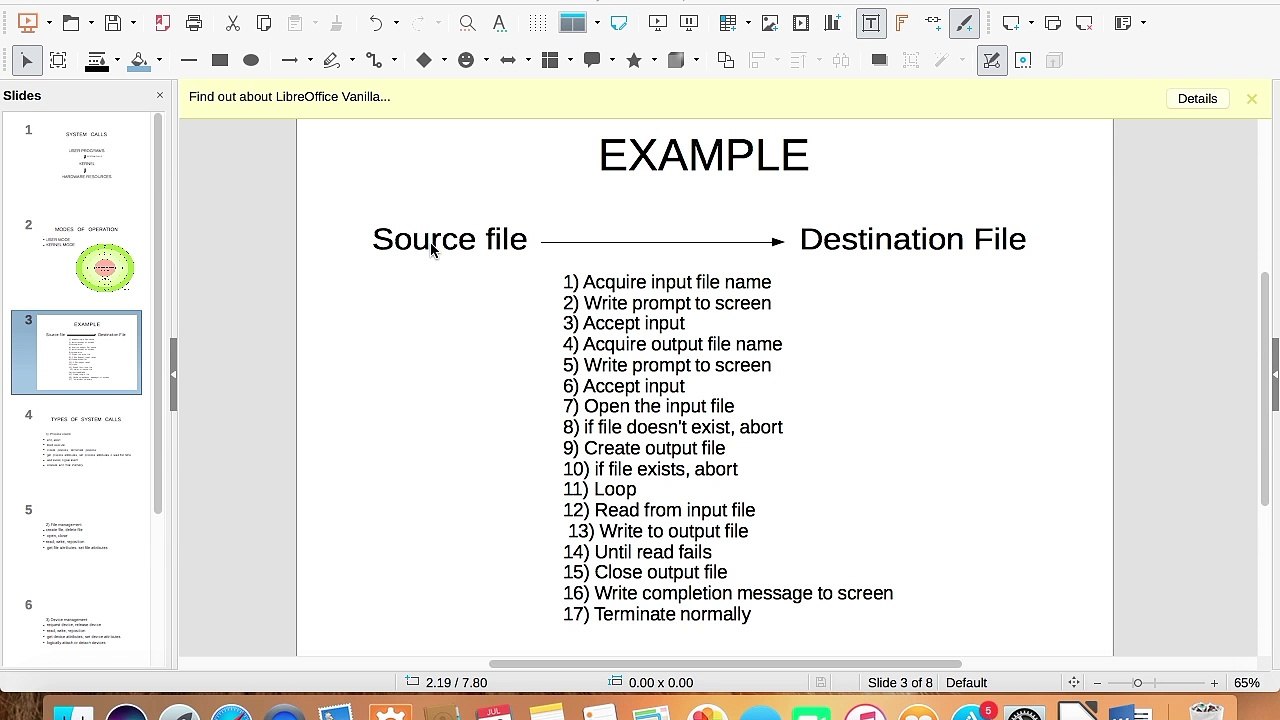
System calls and System call types in operating system
Last moment learning
1 views
0:13
Airline Booking System, Flight Booking System, Airline Booking Systems, Airline Reservation System
David Mathew
102 views

25:17
CS C S009 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
539 views

5:35
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Petrina Corine
25 views

34:39
Cryptography careers and IoT vulnerabilities | Cyber Work Podcast
Infosec
4.0K views

41:17
CS M S022 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
429 views

3:21
How Does The Rise Of AI Impact Military Cryptography Vulnerabilities? - Tactical Warfare Experts
Tactical Warfare Experts
17 views

2:26:01
Virtual Machine Reset Vulnerabilities; Subspace LWE; Cryptography Against Continuous Memory Attacks
Microsoft Research
314 views

2:56
How Common are Cryptographic Vulnerabilities?
Cryptosense
615 views

1:32:49
RWPQC 2024 Session 5: Applied Cryptography, Vulnerabilities, and Countermeasures
SandboxAQ
26.2K views

38:56
Nmap Tutorial For Beginners | Nmap Tutorial to find Network Vulnerabilities | Amader Canvas
Amader Canvas
45.1K views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 7/8
Christiaan008
148 views

1:11:10
Black Hat EU 2010 - Hiding in the Familiar: Steganography & Vulnerabilities in Pop Archives Formats
Black Hat
231 views

0:32
How Attackers Exploit Diameter Protocol Vulnerabilities
Offensive Wireless
523 views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 1/8
Christiaan008
1.8K views

0:47
Researchers Discover New Vulnerabilities In Common Email Encryption Tech
Entertainment (now)
5 views

0:46
Risks Are Accelerating, Yet Traditional Security Vulnerabilities Plague Cryptocurrencies
Benzinga
14 views

10:41
USENIX Security '20 - TeeRex: Discovery and Exploitation of Memory Corruption Vulnerabilities...
USENIX
668 views

8:44
Armitage- Scanning a network for computers and finding their Vulnerabilities
DonDoes30
19 views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 6/8
Christiaan008
194 views

5:45
Threats Vulnerabilities and Exploits
IBM Technology
34.4K views

17:37
TWIM Episode 2: Sodinokibi Ransomware Vulnerabilities & Maryland Criminalizes Malware Possession
This Week in Malware
66 views

29:23
Quantum Threat: Impact of Quantum Computers on Cybersecurity | Threats & Vulnerabilities Summit 2025
Cloud Security Alliance
155 views

20:58
Hackers expose deep cybersecurity vulnerabilities in AI | BBC News
BBC News
524.3K views

0:33
SQL Injection 101: Exploiting Vulnerabilities
CyberSquad
354.4K views

0:18
Critical Go Parser Vulnerabilities Enable Authentication Bypass and Data Theft in Production Systems
Secure Thread
122 views

5:10
Exploiting Windows Vulnerabilities with Metasploit
Hak5
831 views

9:35
Data Exfiltration Vulnerabilities in LLM Applications and Chatbots: Bing Chat, ChatGPT and Claude
Embrace The Red
1.9K views

4:48
What Are The Biggest Microservices Security Vulnerabilities? - Next LVL Programming
NextLVLProgramming
6 views

0:41
911 Outage Sparks Concerns Over Emergency System Vulnerabilities
Benzinga
610 views
Page 1 Next