Search Results for "Authentication vs Authorization in Security"
Find videos related to your search query. Browse through our collection of videos matching "Authentication vs Authorization in Security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Authentication vs Authorization in Security"
50 results found
2:03
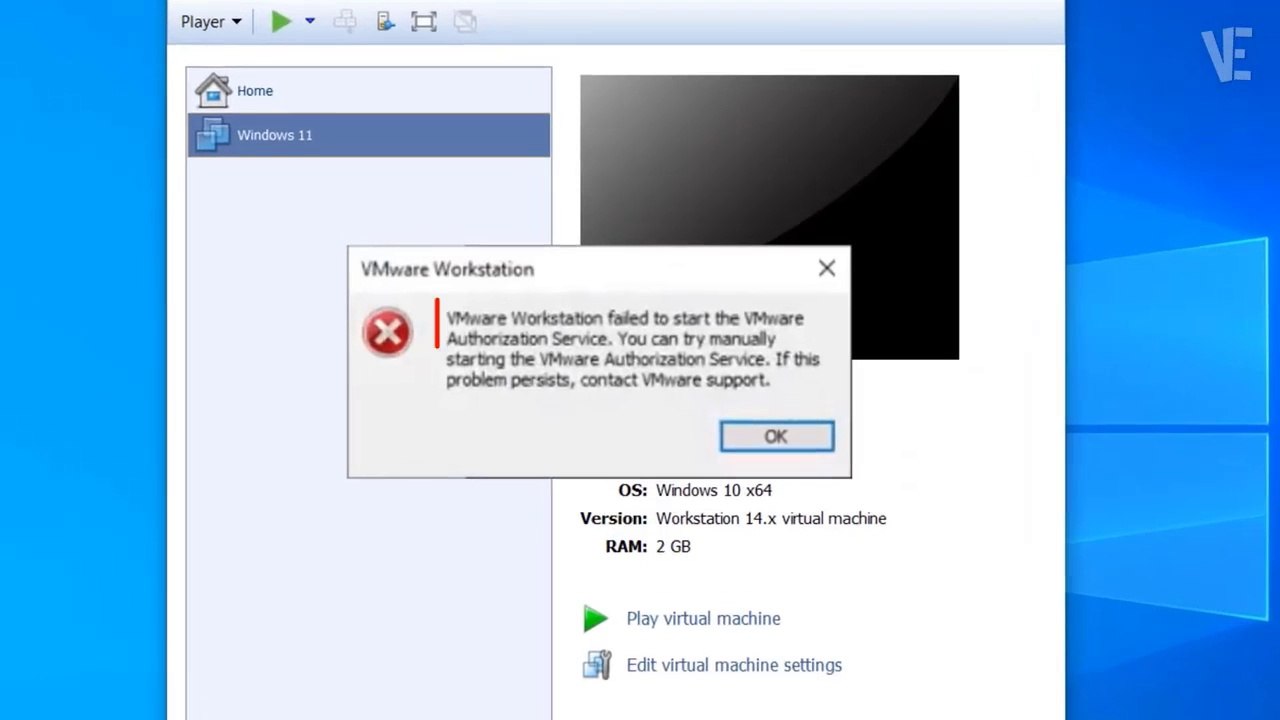
Solved - VMware Workstation failed to start the VMware Authorization Service / VMware Authorization Service is not running
VictorExplains
220 views

1:00
Authentication vs Authorization
A Binary Code
92.8K views

8:26
Authentication vs Authorization | With Animation and Real Life Analogy
Gourab Banerjee
2.2K views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views
7:35
Final Year Projects | Offline QR Code Authorization Based on Visual Cryptography
ClickMyProject
2.1K views

1:05
A Step by Step Instruction on how to apply for the H4 EAD (H4 work authorization new law)
Shahpeerallylawgroup
82 views

1:58
Pfizer COVID pill gets U.S. authorization
The Star
231 views

0:38
2nd Generation Apple Airpods Gets FDA Authorization
Cheddar News
1.1K views

5:13
Trump confirms CIA authorization in Venezuela
Diario As
930 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

11:49
Network Security - Message Authentication Code (MAC) | Cryptography and Network Security
Lectures by Shreedarshan K
2.5K views

2:31:55
Network Security Full Course ! Cyber Security Tutorial ! Cryptography ! Encryption ! Authentication!
Sharan S
468 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views

14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views
0:44
Kerberos Authentication Explained | How Login Tickets Work in Enterprise Security #CISSPFlashcards
Cyber Security Learning
3.2K views
7:13
MACs Message Authentication Codes in Network Security
Cihangir Tezcan
145 views

20:53
MAC in Cryptography || Message Authentication Code in Network Security And Cryptography.
Anas Khan
192 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

6:26
Types of Message Authentication | MAC | Part 2 | Network Security | Hindi Urdu
Ask Faizan
1.9K views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

2:24
Network Security and Cryptography: Message Authentication Code(MAC)
OnlineTeacher
598 views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views
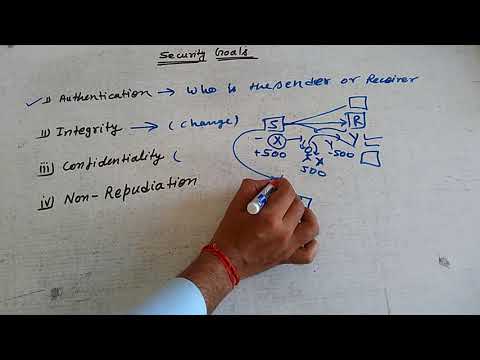
9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

10:25
Network Security 4.4: Message Authentication Codes (MACs)
Cihangir Tezcan
258 views

3:24
MAC (Message Authentication Code) | Unit 4 Cryptography and Cyber Security CB3491 | Anna University
CSE IT Exam Preparation
1.1K views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views
17:04
UNIT IV-COMMUNICATION SECURITY,AUTHENTICATION PROTOCOLS
janadeep n
24 views

22:57
20-What is X.509? | Digital Certificates & Authentication in Network Security | Part 1
Sundeep Saradhi Kanthety
127.1K views

7:00
Authentication Header in IP Security #youtube #cryptography #ipsecurity #networksecurity #videos
Lab Mug
338 views
2:21
Distributed Programming Fullstack 2021 | S3P7 | Security | JWT Use Authentication schema package
Lars Bilde
135 views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views
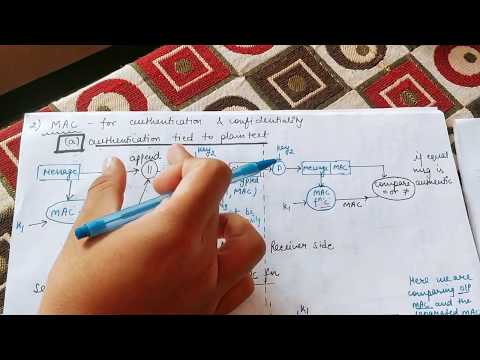
14:41
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views

39:35
19-Learn Kerberos in Network Security 🔐 | How Kerberos Works? | Authentication Protocol Made Simple
Sundeep Saradhi Kanthety
184.1K views

11:16
Authentication Requirements | Cryptography and Network Security
Ekeeda
8.7K views
5:15
🔒 Security in Grid Systems: Authentication & Resource Management @DatabasePodcasts
Database Podcasts
4 views
10:23
Analysis of Biometric Authentication System – Security Issues and Working using Visual Cryptography
OKOKPROJECTS
114 views

59:27
CCoE Webinar Series: Stronger Security for Password Authentication
Trusted CI
148 views

20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

5:55
#Authentication Requirements In Cryptography and Network Security #cns #jntuh #conceptclearbydrmvk
Concept Clear
733 views

9:01
Message Authentication Code (MAC) in Cryptography Hash Function || Network Security in Telugu
Lab Mug
14.3K views
Page 1