Search Results for "user authentication in cryptography"
Find videos related to your search query. Browse through our collection of videos matching "user authentication in cryptography". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "user authentication in cryptography"
50 results found

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

0:21
IRCTC User Id & password kaise banaye Hindi #How to create IRCTC user is & password
BIKASH 4888
3.1M views

8:22
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
8 views

14:01
VB.NET Creating Login with Admin & User (User Level)
Codinger Tutorial
14 views

5:39
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
1 views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

0:30
About For Books Mechanics of User Identification and Authentication: Fundamentals of Identity
dm_09d226e7605f9f5a1a3a6425e52120d4
0 views

4:27
Introduction to User Authentication - CompTIA Network+ N10-005: 5.3
Professor Messer
15.0K views

8:37
Remote user authentication using symmetric encryption
Anand Pashupatimath
4.6K views

20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views

1:09:38
CSE571-11-15B: User Authentication Protocols (Part 2 of 3)
Raj Jain
1.8K views

0:40
Why Continuous User Authentication Matters
CyberGuard
1 views

0:27
Unlocking the Secrets of User Authentication
CyberGuard
0 views

58:47
Kerberos Version 4 & 5 and Remote User Authentication with Asymmetric Encryption -#21is71 VTU 7thsem
VTU padhai
2.3K views

13:31
Build Node.js User Authentication - Password Login
Web Dev Simplified
565.0K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views
14:41
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views
1:01
Cryptography - MAC - Message Authentication Code #cryptography
Alon Lalezari - אלון ללזרי
1.2K views
20:53
MAC in Cryptography || Message Authentication Code in Network Security And Cryptography.
Anas Khan
192 views
12:25
Visual Cryptography with Cloud Computing for Personal Security of the User
IJERT
12 views

11:34
Advantage of Cryptography Tools & Securing End User Equipment
Ziauddin Zia
40 views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views

1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views

19:58
V4a: Message authentication codes: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
736 views

28:39
Symmetric-key cryptography VII - Message authentication codes (MACs)
Tanja Lange: Cryptology
191 views

12:09
Lecture 22: Lecture 4 slides- Public key cryptography and authentication method
QZ Historia
42 views

0:59
Passwordless Authentication Using a Combination of Cryptography, Steganography, and Biometrics
Journal Club
14 views
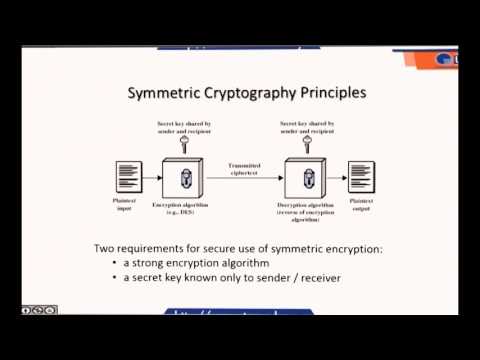
6:05
LECTURE 2- AUTHENTICATION AND BASIC CRYPTOGRAPHY (PART2)
UTeM MOOC
40 views

7:00
Authentication Header in IP Security #youtube #cryptography #ipsecurity #networksecurity #videos
Lab Mug
338 views

12:56
60 Multifold Secured Bank Application authentication service using Random Visual Cryptography and Mu
ICMISC
13 views

24:09
Passwordless Authentication Using Steganography, Cryptography And Biometrics - Tunde Oduguwa
BSides Bristol
39 views

10:23
Analysis of Biometric Authentication System – Security Issues and Working using Visual Cryptography
OKOKPROJECTS
114 views

2:31:55
Network Security Full Course ! Cyber Security Tutorial ! Cryptography ! Encryption ! Authentication!
Sharan S
468 views

25:20
Future-proofing authentication: A look at the future of post-quantum cryptography, Authenticate 2025
Yubico
468 views

9:01
Message Authentication Code (MAC) in Cryptography Hash Function || Network Security in Telugu
Lab Mug
14.3K views

2:31
Cryptography And Network Security :-Authentication And key Agreement
Bharati Kale
496 views

15:15
5 - 1 - Message Authentication Codes-Cryptography-Professor Dan Boneh
Domonique Harder
123 views
Page 1