Search Results for "secure cryptosystem"
Find videos related to your search query. Browse through our collection of videos matching "secure cryptosystem". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "secure cryptosystem"
50 results found

15:11
INS: Unit:4 Public key cryptosystem (Asymmetric key Cryptosystem)
Twinkal Patel
1.1K views

5:31
CSS #10 Symmetric-key Cryptosystem | What is Symmetric-key Cryptosystem | Be The Best | BTB
Be The Best
362 views

0:39
HOW TO PRONOUNCE CRYPTOSYSTEM'S? #cryptosystem's
/ The WordBox / #1 Pronunciation Guide Videos
2 views

27:01
Cryptography lecture 17: Rabin Cryptosystem, ElGamal Cryptosystem
Maths Submarine
292 views

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views
1:11
A Secure DNA Cryptosystem based on Steganography and Indexing Cipher
Intl J of nw security & its applications (IJNSA)
58 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views

0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views
1:19:44
Introduction to Hill Cipher and RSA Cryptosystem
Maths Department(FN)
291 views

1:49
Cryptosystem
WikiAudio
210 views

20:15
Lesson 54: Symmetric VS Asymmetric Cryptography | RSA Rivest Shamir Adleman Public-key Cryptosystem
Fahad Hussain
5.4K views

21:11
Cryptography Lecture 03: Practically Useful Cryptosystem, Confusion, Diffusion
Maths Submarine
23 views

0:16
What is a hybrid cryptosystem?
Intelligence Gateway
146 views
25:25
Cryptography and Information Security - ElGamal Cryptosystem and Variants
Rene Dena
211 views

3:07
Product Cryptosystem
Qwertyfied
420 views
5:56
What is Homomorphic Encryption Explained | Paillier Cryptosystem | PHE | SHE | FHE
Learn with Whiteboard
34.9K views

31:24
Classical Cryptosystem.
Internetwork Security
37.2K views

6:29
Rabin Cryptosystem
Vaishali Tutorials
54.4K views
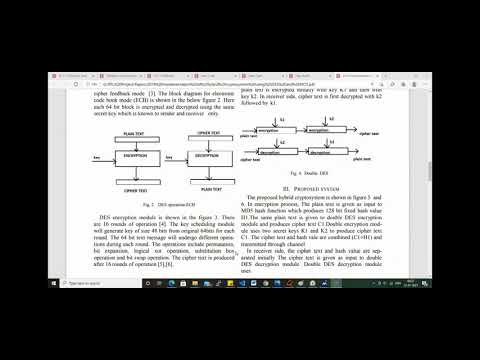
0:32
hybrid cryptosystem using DES and MD5 in verilog
Omicron Project
51 views

0:51
The Incredible Journey of the Rivest–Shamir–Adleman (RSA) Cryptosystem
Brainy Bites
103 views

50:32
The RSA Cryptosystem
nptelhrd
15.8K views

11:49
Cryptography and Components of Cryptosystem
Mariyam Maniyar
1.2K views

27:44
Asymmetric Key Cryptography - RSA Algorithm and Elgamal Cryptosystem
Vaishali Yadav
470 views

44:57
Symmetric Cryptosystem, Data Encryption Standard (DES)
Princy Ann Thomas
270 views

17:10
Generalized Discrete Logarithm based Public-Key Cryptosystem Part 2 - Digital Signature Scheme
Elucyda
379 views
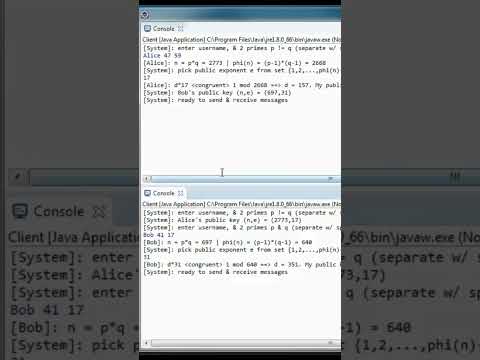
21:09
RSA cryptosystem- Abhishek Singh
Abhishek Singh
12 views

1:06:00
NTRU cryptosystem (continued) and Introduction to Primality testing
Ch-35: IIT Madras: Metallurgical and Others
405 views

25:28
IS U4 1 public key cryptosystem Intro
Anitha Haridas
278 views

44:55
Lec 11| Encryption | cryptosystem & Services |algorithm | Key | Keyspace | Kirchoff's Principal |
Qasim Ali
343 views
1:01
RSA Cryptosystem
Prototype Project
238 views

15:43
Post-Quantum Cryptography: Module Learning with Errors (Module-LWE) based Public Key Cryptosystem
Elucyda
2.8K views

16:17
Discrete Logarithm based Public-Key Cryptosystem: Diffie-Hellman Key Exchange & ElGamal Encryption
Elucyda
901 views
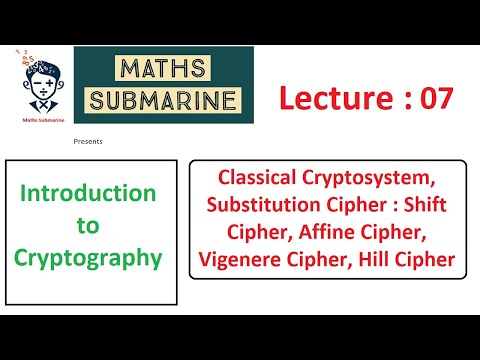
37:30
Cryptography lecture 07: Classical Cryptosystem, Substitution Cipher : Shift, Affine, Vigenere, Hill
Maths Submarine
37 views
10:11
Elgamal Cryptosystem - Public key Cryptography - Cyber Security - CSE4003
Satish C J
37.4K views
0:50
iitb virtual Lab |Cryptography lab |Public Key Cryptosystem |(PKCSv1.5)
Sheldon vibes
1.9K views

1:28:27
Lecture 12: The RSA Cryptosystem and Efficient Exponentiation by Christof Paar
Introduction to Cryptography by Christof Paar
171.5K views

13:30
Generalized Discrete Logarithm based Public-Key Cryptosystem Part 1 - Asymmetric Encryption
Elucyda
610 views

54:46
RSA Algorithm (Rivest–Shamir–Adleman) | public-key cryptosystem | Encryption | Decryption
ATT ArabTechTeam
89 views
12:38
Integer Factorization based Public-Key Cryptosystem: RSA Encryption & Shor's Factoring Algorithm
Elucyda
1.4K views

2:58
What is Caesar Cipher cryptosystem | Cryptography and Hashing Fundamentals in Python and Java
ITExamtools
18 views
19:24
A New Public Key Cryptosystem via Mersenne Numbers
IACR
408 views
Page 1