Search Results for "implementation-defined"
Find videos related to your search query. Browse through our collection of videos matching "implementation-defined". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "implementation-defined"
50 results found
16:38
13. Data Structure and Implementation- Josephus Problem Implementation
Log(n)Academy Trainings
839 views
3:33
Implementation of Steganography(Network Security)
Sppu practicals
228 views

16:03
A Cryptographic Implementation: Hybrid Encryption
Luciano Scarpaci
25 views

5:23:58
End to end Deep Learning Project Implementation using MLOps Tool MLflow & DVC with CICD Deployment 🚀
DSwithBappy
83.8K views
49:37
Informatik 2 — Chapter #07 — Video #043 — Queues (Implementation)
Database Systems Research Group at U Tübingen
716 views
19:25
C++ program array implementation of circular queue data structure
MicroNG
2.1K views
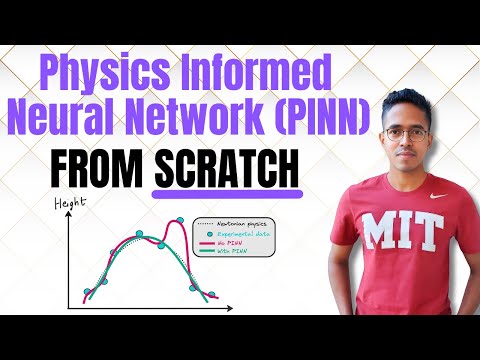
57:00
Physics Informed Neural Networks explained for beginners | From scratch implementation and code
Vizuara
20.0K views

4:47
PBL RKS-115 Implementation of Cryptographic Algorithms in Steganography and Puzzle Game
Kelompok 5 PBL-115 RKS
35 views

4:46
Demonstration of Implementation of Image Steganography using LSB Technique and Morse Code.
ProkillerGirl
110 views

1:55:57
Linked List Tutorial - Singly + Doubly + Circular (Theory + Code + Implementation)
Kunal Kushwaha
1.2M views

4:28
Post-Quantum Cryptography: implementation from theory to practice
IDEMIA Group | Unlock the World
1.2K views
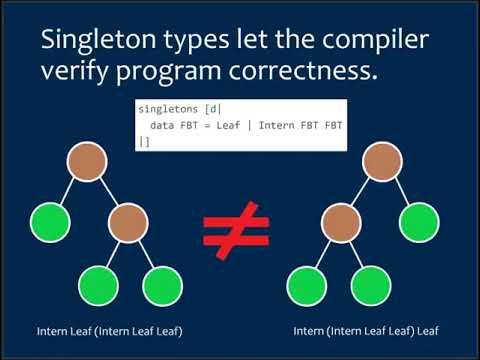
10:36
Haskell Implementation of Key-Homomorphic PRF based on Lattice Cryptography
Michigan Engineering - Honors Program
180 views

0:41
RSA Cryptography Implementation with Socket (Android + JavaFX) with Source Code
eslam gad
841 views
0:12
Implementation Attack
Quick Cybersecurity Study
117 views
1:41
Implementation And Comparison of Three Network Steganography Methods
IBIMA Media
43 views
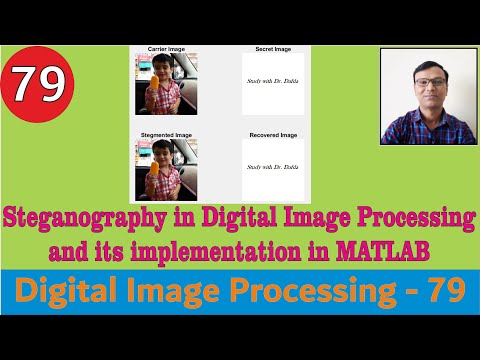
8:04
Steganography in Digital Image Processing & its implementation in MATLAB || LSB based ||Watermarking
Study with Dr. Dafda
2.1K views

19:15
Securing The Future: Cloudflare's Implementation of Post-Quantum Cryptography - Michiel Appelman
Cloudflare
581 views

9:50
Circular Queue Implementation - Array
Blue Tree Code
127.1K views

2:42
Cryptography/Caesar Cipher Decryption/ Matlab Implementation with in 3 Min
Hayder Mazin
1.7K views

6:18
Implementation of Disease Prediction Chatbot and Report | Cloud Technologies | IEEE Projects
Cloud Technologies
510 views
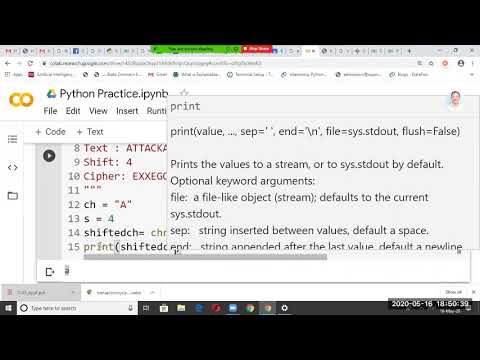
36:59
Python code for Implementation of Caesar Cipher in Cryptography, Prof V N Jokare, NBNSCOE, Solapur
Prof. V N Jokare
147 views
1:00
VLSI IEEE Project Successfully Done by Students | Real Implementation Demo
ProV Logic
1.3K views
0:08
Full Adder Implementation using only NAND Gates
eatwithpeak
56.7K views

49:31
Mobile VoIP Steganography From Framework to Implementation DeepSec 2010
All Hacking Cons
2 views
0:28
Implementation and Performance Evaluation of RNS Variants of the BFV Homomorphic Encryption Scheme
IFoxProjects
62 views

5:42
Double Linked List javascript implementation and How to reverse a linked list
Before Semicolon
2.3K views

15:41
Python Implementation in CS - Caesar Cipher (Cryptography) | Code Analysis - EP 01 | Ran$ome
Ran$ome
84 views

1:29:13
What is Cryptography? | Introduction to Cryptography | Java and C++ implementation | Caesar Cipher
The CS Revelation
442 views

1:28
C++ : Implementation of AKS primality test in Scheme or C++
Hey Delphi
70 views

25:25
How to Reveal the Secrets of an Obscure White-Box Implementation | Junwei Wang | RWC 2018
Real World Crypto
1.0K views
9:01
6 Hill cipher 'c' implementation
Neil gogte Institute of Technology
164 views

8:24
Circular Queue | Set 1 (Introduction and Array Implementation) | GeeksforGeeks
GeeksforGeeks
127.0K views
17:30
Mode-Level vs. Implementation-Level Physical Security in Symmetric Cryptography: A Practical Gu...
IACR
316 views

22:44
Part 3 Unlocking Cryptography - Caesar Cipher Implementation with C
Ai000 Cybernetics QLab
53 views

18:58
Modern Cryptography & Implementation Flaws | RSA Conference
RSA Conference
7.0K views

0:58
implementation of boolean expression using logic gate #logicgates #booleanexpression #shorts
Electronic 2.O
138.5K views

20:55
SIR മറവിൽ എൻ.ആർ.സി? | SIR implementation in Kerala | Out Of Focus
MediaoneTV Live
74.5K views

13:30
implementation single round key part in AES Algorithm by java
Shahriar Hayder Annoy
180 views
5:04
Implementation of hybrid security layer of steganography and cryptography on a credit card purchase
Banu Rekha
177 views
2:09
SD IEEE VLSI IMPLEMENTATION OF DNA CRYPTOGRAPHY USING QUANTUM KEY EXCHANGE
SD Pro Solutions Pvt Ltd
585 views

16:15
What is Data Fabric architecture? Implementation best practices & design principles
Future of AI & Data
3.4K views

21:14
2.10 Implementation of Doubly Linked List - Data Structures
Jenny's Lectures CS IT
504.3K views
2:31
Implementation Hide Text In Image with encryption Using Digital Steganography Technique
Ebtsam Alkhawlani
156 views

49:31
DeepSec 2010: Mobile VoIP Steganography: From Framework to Implementation
Christiaan008
492 views

10:27
Python MD5 implementation
mCoding
48.4K views
24:51
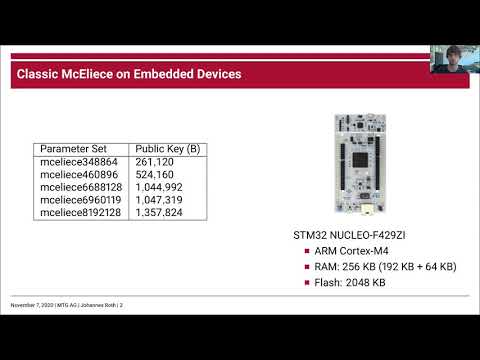
Classic McEliece Implementation with Low Memory Footprint
MTG AG – Enterprise Resource Security
336 views

0:20
Abstract Class: Definition, Method, and Implementation Explained #shorts
Durga Software Solutions
9.8K views

19:08
Stack Implementation Using Linked List C++ | Stack Using Linked List C++ | Data Structures Playlist
Coding With Clicks
5.4K views

33:29
IMPLEMENTATION OF CIRCULAR QUEUE USING LINKED LIST | CIRCULAR QUEUE | DATA STRUCTURES
Parnika Tutorials
382 views
11:39
Prims lazy algorithm implementation I
talkisoverrated
77 views