Search Results for "how attackers exploit diameter protocol vulnerabilities"
Find videos related to your search query. Browse through our collection of videos matching "how attackers exploit diameter protocol vulnerabilities". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "how attackers exploit diameter protocol vulnerabilities"
50 results found

0:32
How Attackers Exploit Diameter Protocol Vulnerabilities
Offensive Wireless
523 views

2:06
Virtual Protocol Latest News Today In Hindi | Virtual Protocol Crypto | Virtual Protocol News | BTC
MR KRYPTO
42 views

0:30
Rangers protocol vvip protocol Punjab pakistan | Rangers | protocol vvip | Ghouri4u Official
Ghouri4u official
18 views
3:33
WoW Exploit: Sunken Temple Leveling Exploit
annepinup
2.0K views

25:17
CS C S009 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
539 views

41:17
CS M S022 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
429 views

0:23
Rice popped chips rice cracker making machine 90mm diameter rice cake #machine #factory
Jinan Arrow Machinery Co., Ltd
927 views

7:26
Diameter of Binary Tree - Leetcode 543 - Python
NeetCodeIO
111.3K views
![Torsional Equation: Calculate Diameter of Shaft [Solved Problem] Strength of Material | Shubham Kola](/image/s2.dmcdn.net/v/UB6v41e9DJdj2AzFE/x720)
3:36
Torsional Equation: Calculate Diameter of Shaft [Solved Problem] Strength of Material | Shubham Kola
Shubham Kola
2 views
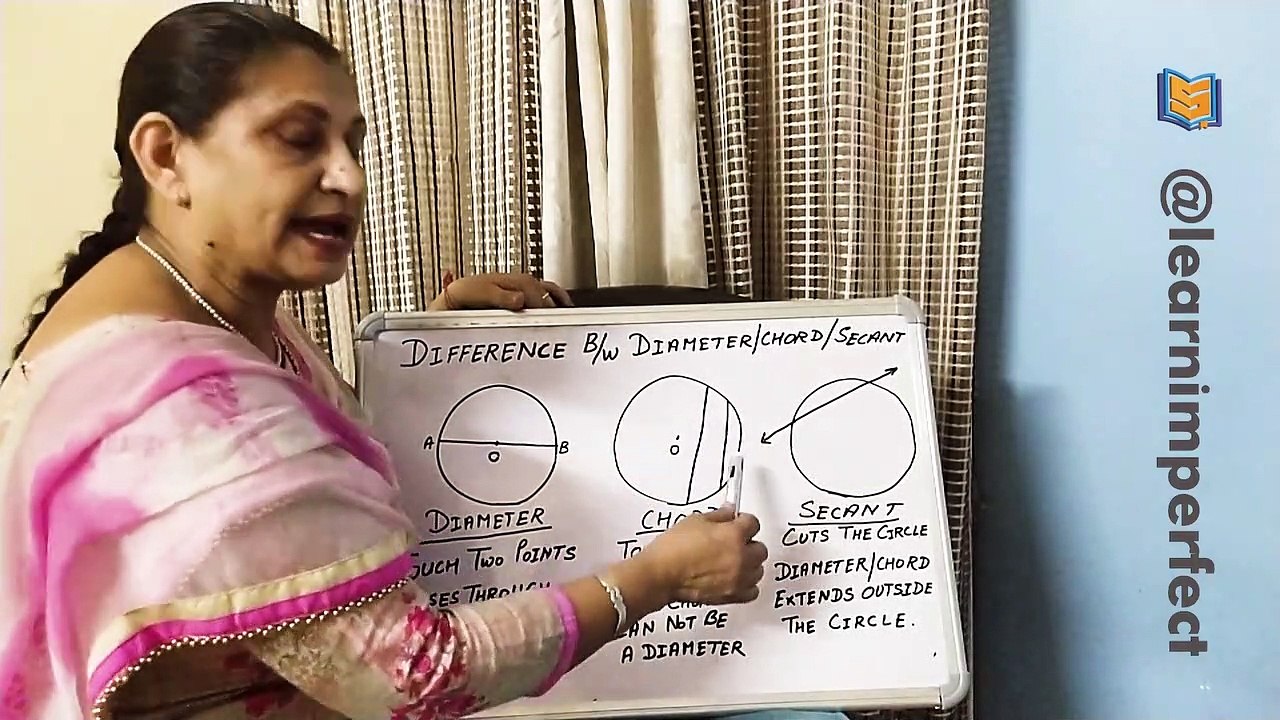
5:46
What is Diameter,Secant, chord in Hindi | Circle Vocabulary | Parts of Circle | Related to Circles |
Learn Imperfect
70 views
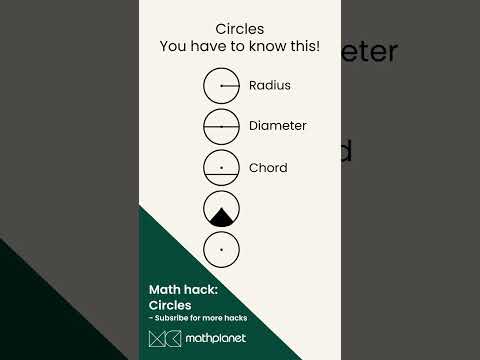
0:09
Circles: Radius, Diameter, Chord, Sector and Segment, all you need to know. #math #shorts
MathPlanetVideos
300.4K views

42:41
Cryptography Lecture 04: Cryptanalysis, Types of Attackers, Types of Attacks, Security Norms
Maths Submarine
35 views

1:33:16
Sweet pet nurse by day—shadow killer by night! 100 attackers? she wiped them out barehanded!
Bikan-hot drama
16.5K views

19:36
ShmooCon 2014: Attacker Ghost Stories: Mostly Free Defenses That Give Attackers Nightmares
Christiaan008
3.0K views

50:05
ShmooCon 2014: Raising Costs for Your Attackers Instead of Your CFO
Christiaan008
1.5K views
0:48
What’s the secret to making cryptographic hash functions tougher for attackers? #securityplus
CyberTech Guard
60 views
9:02
How you get Hacked: what attackers use today
PC Security Channel
212.0K views

0:29
February 04, 2024 - "US Imposes Sanctions on Iranian Cyber-attackers"
Embracing Digital Transformation
22 views

0:15
The attackers fleeing the scene.
Shropshire Star
6.8K views

0:27
Self Defense Against Multiple Attackers 12 on 1
Kevin Goat Self Defense
625.4K views
9:16
Mga Batang Riles: Baklitang Riles, nahanap na ang kanilang attackers?! (Episode 15 - Part 2/3)
GMA Network
245 views

9:11
TCP/IP Model | Internet protocol suite | Protocol and services of TCP/IP Model
Chirag Bhalodia
1.5K views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

3:22
Alpha Protocol - Alpha Protocol - Developers Diary
Games2C_INT
9 views

2:05
Ed Protocol Ingredients || Erectile Dysfunction Protocol
Helenaghv
8 views

9:59
Alpha Protocol Walkthrough - Infiltrate Alpha Protocol ...
MahaloGames
1 views

1:32
Massive protocol PM Abbasi Protocol in Karachi
MTV
49 views

5:18
Session 11 : Open RAN Protocol Stack | PDCP Protocol and SDAP Layer
Learn And Grow Community
10 views

1:24
IMAM E KABA PROTOCOL IN PAKISTANIMAM E KABA PROTOCOL IN PAKISTAN
All In one
1 views

2:33
Ed Protocol Review || Erectile Dysfunction Protocol Review
Vernitaw0z
1 views

0:06
Encryption Protocol. #cybersecurity #cyberpunk #viral #protocol #sslcertificate
Infintysec
179 views

1:27
people Bushing Sharif Brothers Because of protocol In jinah hospital because of protocol
harpal.pk
16 views

1:45
erase herpes protocol review - erase herpes protocol
Get rid of hives
24 views

11:00
Web and HTTP protocol tutorial | Hypertext Transfer Protocol explained | World Wide Web | TechTerms
TechTerms
65.6K views

14:31
Network Protocol Explained | Types Of Network Protocol | Fundamentals Of Networking | Simplilearn
Simplilearn
1.4K views

5:35
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Petrina Corine
25 views

34:39
Cryptography careers and IoT vulnerabilities | Cyber Work Podcast
Infosec
4.0K views

3:21
How Does The Rise Of AI Impact Military Cryptography Vulnerabilities? - Tactical Warfare Experts
Tactical Warfare Experts
17 views

2:26:01
Virtual Machine Reset Vulnerabilities; Subspace LWE; Cryptography Against Continuous Memory Attacks
Microsoft Research
314 views

2:56
How Common are Cryptographic Vulnerabilities?
Cryptosense
615 views

1:32:49
RWPQC 2024 Session 5: Applied Cryptography, Vulnerabilities, and Countermeasures
SandboxAQ
26.2K views
38:56
Nmap Tutorial For Beginners | Nmap Tutorial to find Network Vulnerabilities | Amader Canvas
Amader Canvas
45.1K views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 7/8
Christiaan008
148 views

1:11:10
Black Hat EU 2010 - Hiding in the Familiar: Steganography & Vulnerabilities in Pop Archives Formats
Black Hat
231 views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 1/8
Christiaan008
1.8K views

0:47
Researchers Discover New Vulnerabilities In Common Email Encryption Tech
Entertainment (now)
5 views

0:46
Risks Are Accelerating, Yet Traditional Security Vulnerabilities Plague Cryptocurrencies
Benzinga
14 views

10:41
USENIX Security '20 - TeeRex: Discovery and Exploitation of Memory Corruption Vulnerabilities...
USENIX
668 views

8:44
Armitage- Scanning a network for computers and finding their Vulnerabilities
DonDoes30
19 views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 6/8
Christiaan008
194 views