Search Results for "hmac vs hash"
Find videos related to your search query. Browse through our collection of videos matching "hmac vs hash". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hmac vs hash"
50 results found

10:30
Introduction to HASHING in Data Structures || Hash Functions,Hash Table, Hash Keys,Hash Values in DS
Sundeep Saradhi Kanthety
11.5K views

0:13
Hash Oil,buy Hash oil online,Hash oil for sale,Prefilled hash oil cartridges for sale http://dabstarshop.com
dabstarshop dabstarspharmacy
1 views

57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views

6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views
20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

14:52
Applications of Hash Function | Purpose of Hash Function | Real Time Application of Hash Function
Chirag Bhalodia
32.1K views

9:00
Hash Functions || hash function algorithm || hash function cryptography || hashing vs encryption
The Ecomly Tech
24 views

12:00
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
Chirag Bhalodia
107.9K views

12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views

8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views
1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views

7:05
HMAC - Cryptography I
Nguyen Duong Anh
80 views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views
1:09:59
Go UUID HMAC
Learn To Code
945 views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views

10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views
22:00
CNS HMAC
Kallam Gopala Reddy
312 views
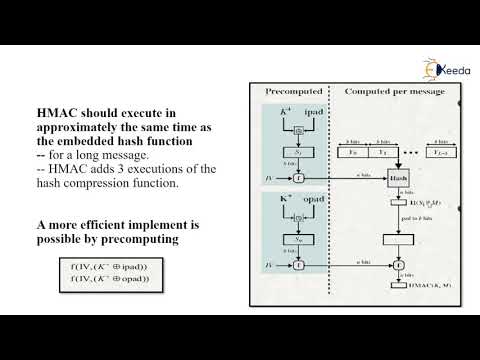
20:35
HMAC | Cryptography and Network Security
Ekeeda
677 views
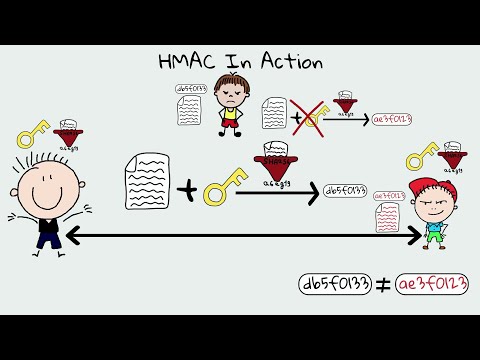
6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views

0:46
HMAC Promo take 2
Players 2Pros
29 views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views

0:46
What Is Hash Collision and What Does It Mean To Be Resistant To Hash Collisions?
Binance Academy
1.3K views

7:53
Introduction to Hashing|Hashing in Data Strucutures|What is Hashing|Hash Table|Hash function
Scratch Learners
107.6K views
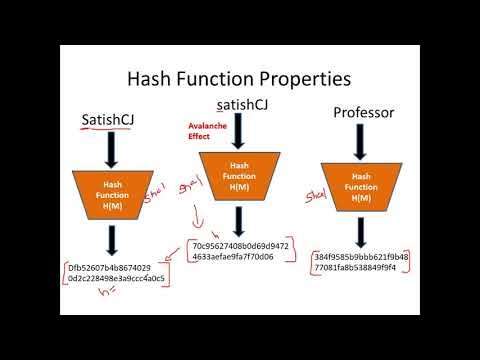
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

25:51
Hash Tables: Hash Functions, Sets, & Maps - DSA Course in Python Lecture 4
Greg Hogg
84.9K views

13:56
Hash Tables and Hash Functions
Computer Science Lessons
1.7M views

7:40
Hash function based on CBC in cryptography | Hash function based on cipher block chaining
Chirag Bhalodia
24.0K views

13:39
Introduction to Hashing in Data Structure | Hash Table, Hash Function | DSA using Java #56
ForMyScholars
27.2K views

26:41
What is HASHING ? | Why do we NEED it? | What is a Hash Function | (Example - Array vs Hash Table)
Simple Snippets
9.5K views

0:17
What is Hash and what it is used for? |#blockchain #blockchain #Hash #block #BlockchainSeekho
Blockchain Seekho
1.2K views

1:34
Hash Security, Pass-the-Hash, and PKI Explained | Security+ in 60 Seconds
Cyber Buddy
40 views

9:32
Hash function Keya hai? hashing Algorithm? password hashing? password and hash function Hindi
Technical Haroon
8.1K views

9:33
What is Hashing? Hashing Algorithm, Hash Collisions & Hash Functions
Monis Yousuf
20.2K views
![[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide](/image/i.ytimg.com/vi/qMemCPACnWw/xhqdefault.jpg.pagespeed.ic.G9pQ20ONPm.jpg)
12:21
[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide
Bitten Tech
35.7K views

13:13
Hashing in Data Structure - Hashing in DSA - Hash Table - Hash Function - Collisions - Load Factor
Coding With Clicks
1.9K views

13:18
Introduction to Cryptographic Hash Function| Merkel Damgard Scheme | SHA-256 | Secure Hash Algorithm
Muhammed Mustaqim
607 views

27:54
CRYPTOGRAPHIC HASH FUNCTIONS in HINDI/URDU | , Secure Hash Algorithm | Birthday Paradox Attack
Shahzeb Khan Dasti
256 views

1:14
error:0308010C:digital envelope routines::unsupported at new Hash (node:internal/crypto/hash:68:19)
Coffee Programmer
11.5K views

37:31
Five* non-cryptographic hash functions enter. One hash function leaves.
Linux.conf.au 2016 -- Geelong, Australia
4.7K views
Page 1